EN | Sony Subdomain Takeover
Summary
Subdomain takeover was possible in some of the subdomains. The CNAME entry in the subdomain is pointing to an external page service (fanfootballsony.s3-us-west-2.amazonaws.com).
Description
$ nslookup fan.football.sony.net 8.8.8.8 Server: 8.8.8.8 Address: 8.8.8.8#53 Non-authoritative answer: Name: fanfootballsony.s3-us-west-2.amazonaws.com Address: 173.255.201.227
fan.football.sony.net -> fan.football.sony.net is an alias for fanfootballsony.s3-us-west-2.amazonaws.com.
The bucket name must be the same as the CNAME. So fan.football.sony.net/filename would be the same as fanfootballsony.s3-us-west-2.amazonaws.com/filename if a CNAME were created to map fan.football.sony.net to fanfootballsony.s3-us-west-2.amazonaws.com.
PoC:
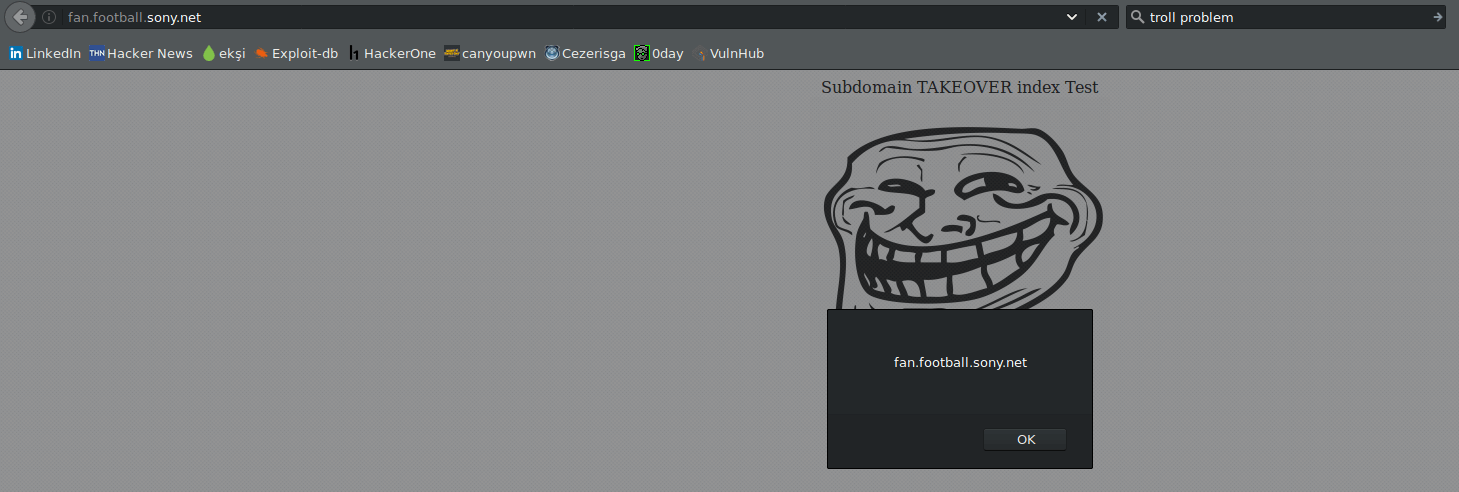
http://fanfootballsony.s3-us-west-2.amazonaws.com/subdomaintakeover/index.html
Risk
- Fake website
- Malicious code injection
- Users tricking
- Company impersonation
Since the vulnerable subdomain is called signup , it’s a perfect place to create a fake login/subscribe page to steal users credentials. An attacker would post links on forums or send emails and then wait for people to signup on the site he owns.
Fix
You should immediately remove the DNS-entry for this domain or point it elsewhere if you don’t use that service.
